API gateways have long played a key role in securing API access, handling authentication, authorisation and traffic management. However, deeper authorisation has often required custom implementations or deferring to service-specific logic, and this introduces inconsistencies and operational overhead. Bespoke or non-standard solutions frequently result in the API Gateway acting as both the Policy Decision Point (PDP) and the Policy Enforcement Point (PEP), tightly coupling access control within the gateway itself.
I addressed this several years back by embedding Open Policy Agent (OPA) as a plugin into the API Gateway middleware. This approach decoupled the PDP from the PEP, allowing for more flexible and scalable policy evaluation. However, while it improved flexibility, it remained a bespoke solution that lacked interoperability. Can we do better?
With AuthZEN, this decoupling takes a significant step forward by providing a standards-compliant API. API Gateways can now enforce authorisation while seamlessly integrating with multiple PDPs, ensuring interoperability and reducing the need for custom integrations. This shifts policy enforcement away from proprietary solutions, towards an open, interoperable model for API security.
The need for medium-grained authorisation
Authorisation can be classified into three levels:
- Coarse-grained authorisation – This controls access at a broad level, such as entire applications or major system functions. Role-based access control (RBAC) often falls under this category, where users are granted permissions based on roles, e.g., can an admin access an admin dashboard?
- Medium-grained authorisation – This applies access control at the API level, determining whether a user can access a specific endpoint based on attributes like roles, request methods, or other conditions. e.g. Can this user perform a GET request on /transactions? Attribute-based access control (ABAC) often falls into this category, allowing for more flexible rules than RBAC.
- Fine-grained authorisation (field-level and object-level control) – This goes much deeper by controlling access to specific data fields or objects within an API response. For example:
• A user can only see the last 4 digits of the bank account
• An analyst can view balances, but not modify
• A customer can only access their own invoices, not somebody else’s
This level of enforcement typically happens within the application logic or databases. The number one most critical vulnerability at this level is Broken Object Level Authorization (BOLA), which appears in the OWASP API security top 10.
Most API security needs fall into the medium-grained category, making API Gateways the natural PEP. Enforcing access control at the gateway level reduces backend load, prevents unauthorised requests from reaching microservices, and ensures consistent security policies across all APIs.
Defence in depth – A layered API security strategy
API gateways sit at the network’s edge, acting as one of the first lines of defence for incoming API requests. This unique position allows them to enforce security policies before traffic reaches the upstream services.
A robust security model doesn’t rely on any single layer of protection. Instead, adopting a defence-in-depth strategy ensures that if one layer is bypassed, there are additional controls to prevent unauthorised access – limiting any blast radius.
With this approach, the API Gateway enforces identity verification and access control centrally. It performs rate limiting and throttling, protecting against denial of service (DoS) or brute force attacks; it is also responsible for things like threat detection and logging. Some API Gateways, like Tyk, can also perform request and schema input validation based on an OpenAPI Schema.
Beyond this layer, the application serves as the final line of defence. This includes verifying user permissions at the business logic level and more business-related input validation, sanitisation, and application-layer monitoring.
This ensures a consistent and scalable security model, freeing microservices from handling cross-cutting concerns like authentication and coarse and medium-grained authorisation. Rejecting unauthorised requests earlier also improves security posture and prevents unnecessary processing by backend services.
Understanding AuthZEN
AuthZEN aims to become a standard designed to provide a unified approach to API authorisation, enabling seamless communication between policy enforcement and decision points. Rather than implementing custom authorisation mechanisms, API gateways and services can rely on AuthZEN’s structured API to request and enforce access control policies in a consistent and interoperable way.
Remember how I mentioned that I had worked on an OPA plugin before? Well, this is exactly what I meant about it being a bespoke solution that lacked interoperability.
For those of us who are using policy engines, everybody is creating their custom API to talk to their policy engine. That makes the implementation brittle.
Why standardising authorisation matters
Omri Gazitt, co-chair of the OpenID AuthZEN working group, describes a fundamental problem in the authorisation space as an “N * M” challenge. Each application has its way of assigning permissions to users, forcing developers to create custom integrations for every system. This fragmentation is inefficient and costly.
Just as OpenID Connect standardised authentication and eliminated the need for custom login integrations, AuthZEN aims to do the same for authorisation. By defining a common API for Policy Enforcement Points (PEPs) to communicate with Policy Decision Points (PDPs), AuthZEN transforms the problem from “N * M” (every app integrating with every authorisation provider) into “N + M” (apps integrating once with a standardised API).
This standardisation benefits everyone:
- API gateways and applications can integrate with multiple authorisation platforms using a single API, instead of creating bespoke integrations.
- Authorisation providers become more accessible to a broader range of applications without requiring custom adapters.
- IT administrators gain a centralised way to manage access policies across applications, ensuring compliance and answering key security questions.
By adopting AuthZEN, API gateways like Tyk can facilitate seamless interoperability, reduce development complexity, and improve security governance across systems.
For full details on the latest working draft of AuthZEN, is available at https://openid.net/wg/authzen/specifications/
Now that we understand a little bit about AuthZEN, let’s explore how we have implemented it at Tyk.
Introducing the AuthZEN plugin for Tyk
The AuthZEN plugin for Tyk enables Tyk API Gateway to act as a fully standardised policy enforcement point. Instead of relying on custom-built logic or proprietary integrations, this plugin allows Tyk to communicate seamlessly with multiple Policy Decision Points (PDPs) using the AuthZEN protocol.
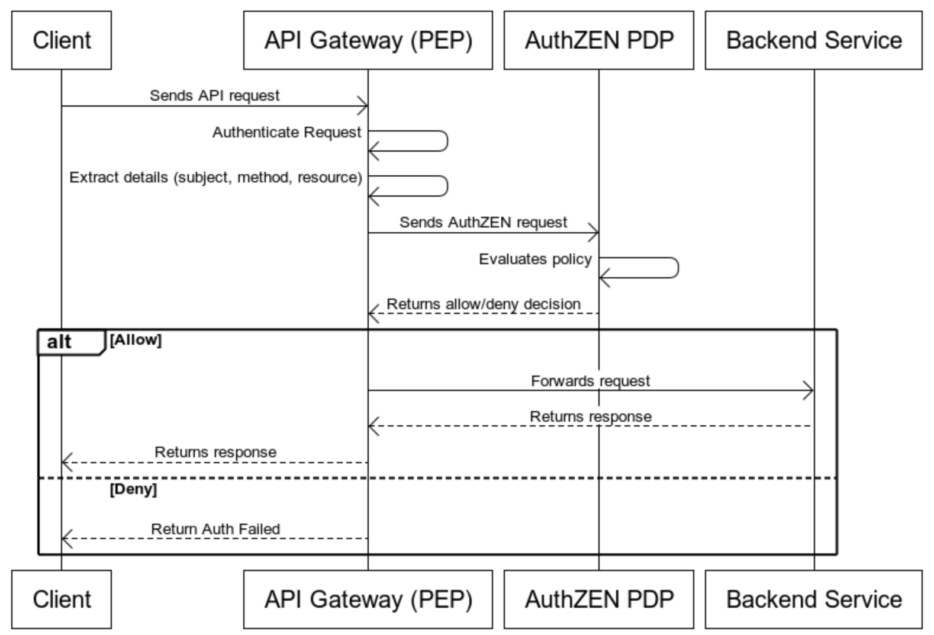
How the plugin works
When a request is received by the API gateway:
- The gateway extracts relevant request details such as the user’s identity, request method, and resource being accessed
- These details are formatted into a standardised AuthZEN request.
- The request is sent to a compatible PDP (e.g. Aserto, OPA, Cerbos, Axiomatics, Topaz and others)
- The PDP evaluates the request based on predefined policies and returns an allow/deny decision
- The gateway either forwards the request to the backend or blocks it depending on the response
If you are interested in seeing the plugin in action or using it yourself, you may access it via the OpenID Foundation’s AuthZEN repository, which contains an interop harness, containing a Rick and Morty TODO frontend, backend, AuthZEN compatible PDPs, and gateway implementations.
Conclusion
API gateways are the ideal place to enforce medium-grained authorisation, ensuring secure and efficient access control.
By leveraging an AuthZEN-compliant PDP, organisations can build scalable and secure APIs without embedding complex decision-making logic within their microservices, building too much logic into the API Gateway, or locking themselves into a specific authorisation provider.
Using AuthZEN simplifies policy enforcement by providing a standardised framework for communicating with different PDPs. This ensures consistent access control across all APIs, reducing operational overhead while maintaining flexibility and interoperability.
If you are interested in taking Tyk with AuthZEN for a test drive, get in touch!
References
- https://openid.net/wg/authzen/specifications/
- https://github.com/asoorm/tyk-go-plugins/tree/master/authorize_opa
- https://www.aserto.com/blog/openid-authzen-implementers-draft-why-it-matters
- https://github.com/openid/authzen/
- https://tyk.io/blog/res-owasp-api-security-1-broken-object-level-authorization/
- https://tyk.io/docs/api-management/traffic-transformation/#request-validation-using-tyk-oas
- https://github.com/openid/authzen/tree/main/interop/authzen-api-gateways/tyk-gateway