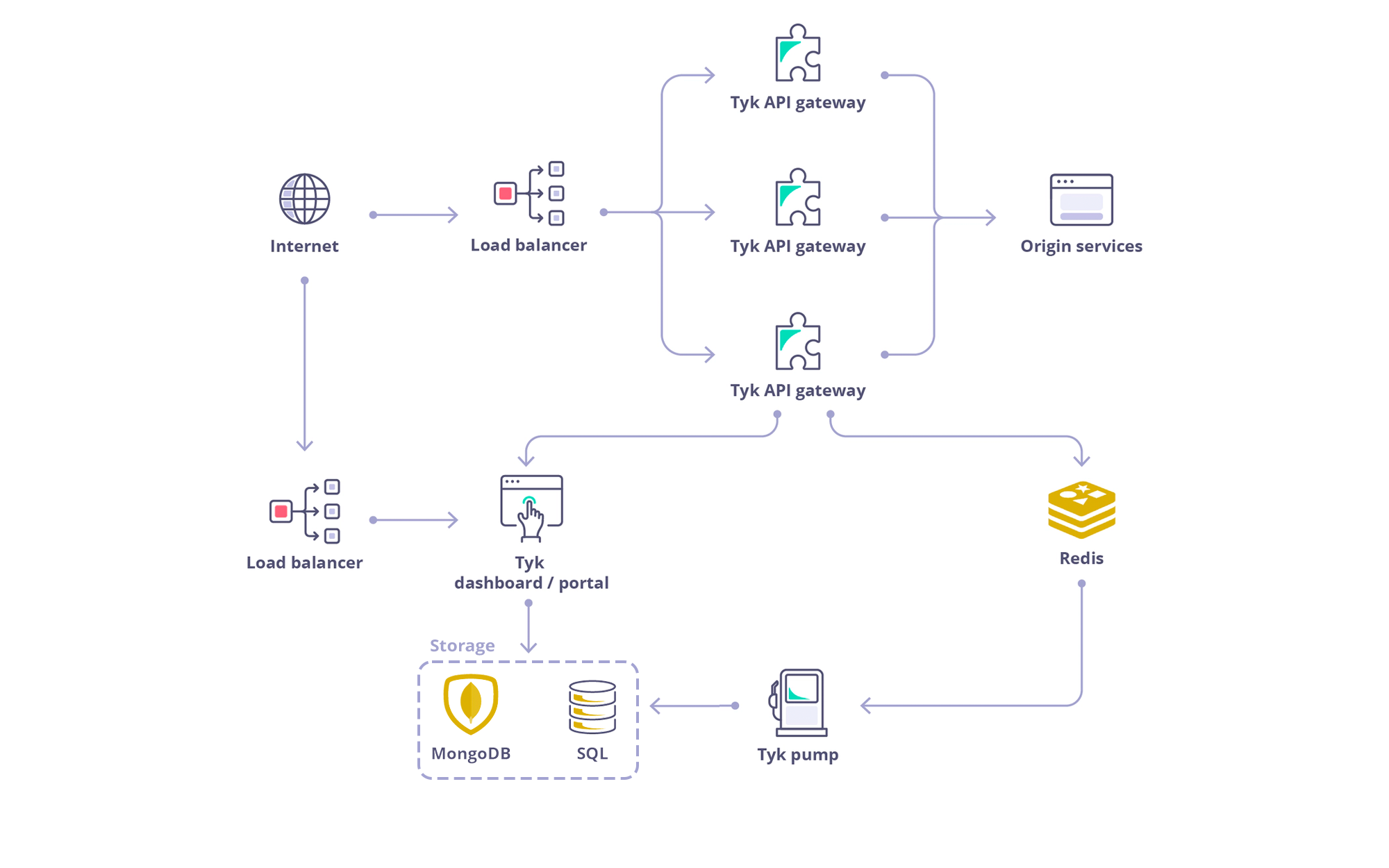
What is Tyk Self-Managed
Tyk Self-Managed allows you to easily install our Full Lifecycle API Management solution in your own infrastructure. There is no calling home, and there are no usage limits. You have full control.What Does Tyk Self-Managed Include?
The full Tyk Self-Managed system consists of:- Tyk Gateway: Tyk Gateway is provided ‘Batteries-included’, with no feature lockout. It is an open source enterprise API Gateway, supporting REST, GraphQL, TCP and gRPC protocols, that protects, secures and processes your APIs.
- Tyk Dashboard: The management Dashboard and integration API manage a cluster of Tyk Gateways and also show analytics and features of the Developer portal. The Dashboard also provides the API Developer Portal, a customizable developer portal for your API documentation, developer auto-enrollment and usage tracking.
- Developer Portal: A customizable API portal to securely publish and manage API access for your consumers.
- Tyk Pump: Tyk Pump handles moving analytics data between your gateways and your Dashboard (amongst other data sinks). The Tyk Pump is an open source analytics purger that moves the data generated by your Tyk nodes to any back-end.
- Tyk Identity Broker (Optional): Tyk Identify Broker handles integrations with third-party IDP’s. It (TIB) is a component providing a bridge between various Identity Management Systems such as LDAP, Social OAuth (e.g. GPlus, Twitter, GitHub) or Basic Authentication providers, to your Tyk installation.
- Tyk Multi-Data Center Bridge (Optional, add-on): Tyk Multi-Data Center Bridge allows for the configuration of a Tyk ecosystem that spans many data centers and clouds. It also (MDCB) acts as a broker between Tyk Gateway Instances that are isolated from one another and typically have their own Redis DB.