What is Tyk Open Source
Open source is at the heart of what we do. Anything that is API Gateway-related lives in the Gateway, or is critical for the Gateway to work is open and freely available via our Github. The Tyk Gateway is fully open-source. It’s all the same Gateway that’s used by you (the community!), by our enterprise products, as well as our SaaS. Our commitment to open source also delivers a host of benefits for our users: sign up for free with Tyk, receive securely packaged open source packages, get started guides, access to our community and all of the latest open source information.Tyk OSS, Tyk Open Source, Tyk Gateway, Tyk CE
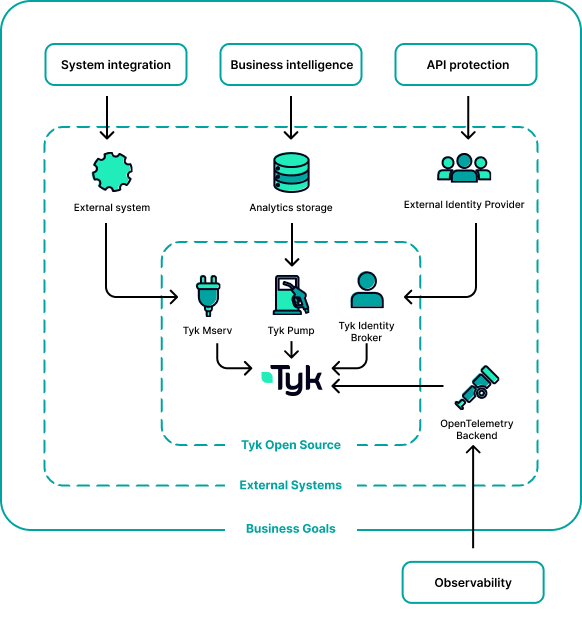
What Does Tyk Open Source Include?
The Tyk Team has created and maintains the following components, which are fully Open Source and available under Mozilla Public License 2.0 (MPL). Star the Tyk components you use by clicking the appropriate button:Tyk Gateway
Fully fledged API Gateway.Learn more
Tyk Pump
Send API analytics data to your chosen backend.Learn more
Tyk Identity Broker
Connect your third-party IdP systems.Learn more
Tyk Helm Chart
Deploy Tyk in K8S.Learn more