Portal Concepts
Last updated:
Attention:
You’ve reached a page related to the Tyk Classic Portal. If you were searching for API documentation of the new Tyk Developer Portal please use the latest Postman collection page. Future deprecation of Tyk Classic Portal
This product is no longer actively developed as it has been superseded by the new Tyk Developer Portal. Please note that the Tyk Classic Portal now has limited support and maintenance. Please contact us at [email protected]if you have any questions.
API Catalog
The API Catalog is a list of APIs that you have published to your portal.
The API Catalog entry is not a one-to-one map between an API you manage in Tyk, since you might want to compose multiple managed services into a single public-facing API Facade, a catalog entry is actually an entry that maps against a security policy.
From the API Catalog, a user can either:
- View the documentation for the API
- Request for a token to the API
When a developer requests a token, a new Auth token is generated on the linked policy, instead of the actual API, since you may wish to publish multi-tier access to the same API (E.g. Bronze / Silver / Gold).
Key Requests
A key request is a record that is generated when a developer requests an access token for an API published in the API Catalog. The Key request encompasses the following information:
Read more about them in the Key Request section
Multiple APIs for a single Key Request
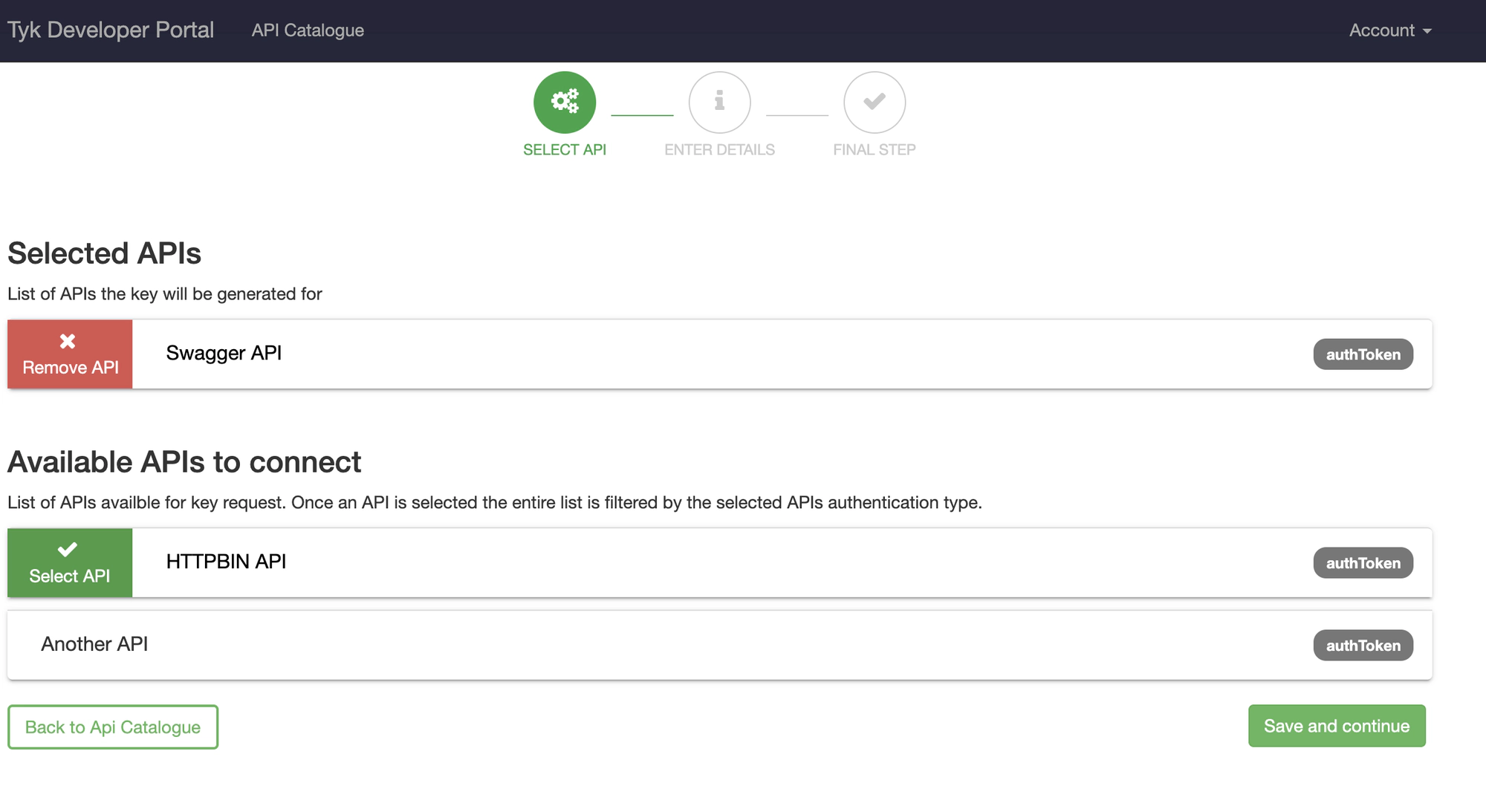
New for v1.9, a developer can now request access to multiple APIs with a single key request. The APIs you group together via a single key should all be of the same authentication type.
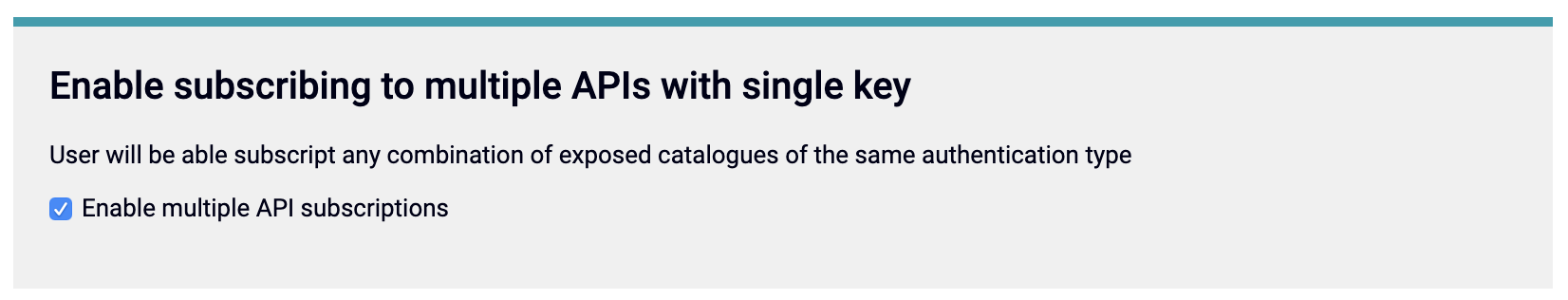
To enable this functionality, select Enable subscribing to multiple APIs with a single key from the Portal Management Settings.
Edit APIs associated with a single Key Request
New for v1.9.4, if you have Enable subscribing to multiple APIs with a single key selected you can edit the APIs associated with the Key. You can perform the following:
- Remove access to existing APIs
- Subscribe to new APIs (of the same authentication type as the existing ones).
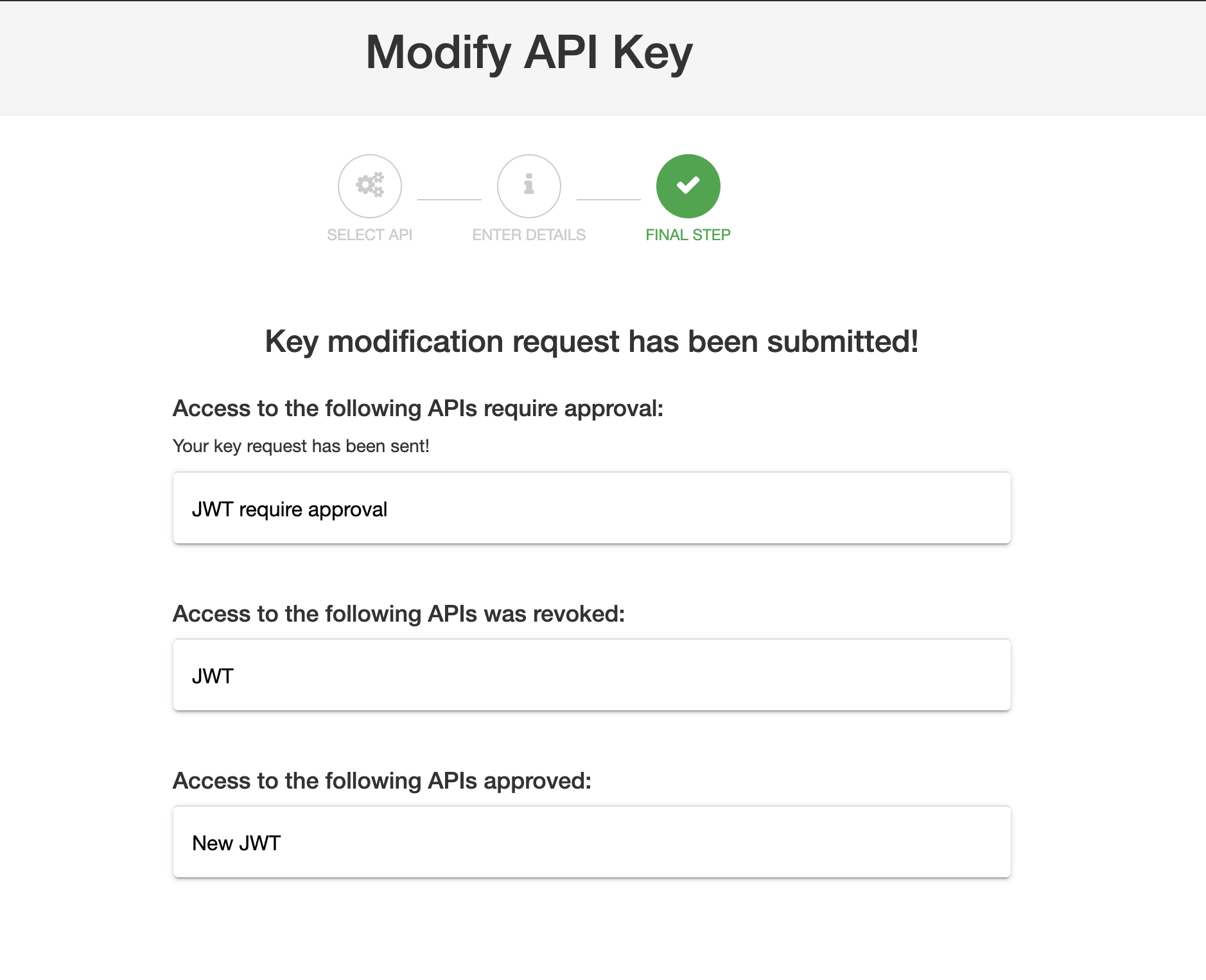
If a new API requires key approval, the new key request will be generated, and access to this API will be granted after your admin approves it.
Policies
In the context of the developer portal, a security policy is the main “element” being exposed to public access. The policy is the same as a standard policy, and the policy forms the baseline template that gets used when the portal generates a token for the developer.
Security policies are used instead of a one-to-one mapping because they encapsulate all the information needed for a public API program:
- Rate limits
- Quota
- Access Lists (What APIs and which versions are permitted)
- Granular access (Which methods and paths are allowed, e.g. you may want to only expose read-only access to the portal, so only GET requests are allowed)
- Multi-policy-management (With a Key, you can assign more than one policy to an APIs and each policy will have it’s own counter).
Within the developer portal admin area, under a developer record, you will see their subscriptions. Those subscriptions represent the tokens they have and their policy level access. It is possible to then “upgrade” or “downgrade” a developers access without actually managing their token, but just assigning a new policy to that token.
Documentation
Within the portal, documentation is what a developer can use to learn how to access and use your APIs.
The developer portal supports two types of documentation, and will render them differently:
- API Blueprint - this is rendered to HTML templates using Jade and Aglio.
- Swagger/OpenAPI (OpenAPI 2.0 and 3.0 are supported) - either by pasting your Swagger JSON or YAML content into the code editor, or by linking to any public facing Swagger URL. The URL version can be rendered using Swagger UI which offers a sandbox environment where developers can interact with your API from the browser.
Note
Support for API Blueprint is being deprecated. See Importing APIs for more details.
Within an API Catalog entry, documentation must be attached to the catalog entry for it to be published.
Developers
Within the developer portal, a developer is an end-user that has access to the developer portal section of the portal website. This user is completely separate from Tyk Dashboard users and they do not ever intersect (they are also stored separately).
A developer record consists of some basic sign-up information and a set of admin-definable fields that get attached to the developer as metadata.
Within the developer view of the Tyk Dashboard, it is possible to manage all access of a developer, including the access levels of their tokens.