API Catalog
The API Catalog is a list of APIs that you have published to your portal. The API Catalog entry is not a one-to-one map between an API you manage in Tyk, since you might want to compose multiple managed services into a single public-facing API Facade, a catalog entry is actually an entry that maps against a security policy. From the API Catalog, a user can either:- View the documentation for the API
- Request for a token to the API
Key Requests
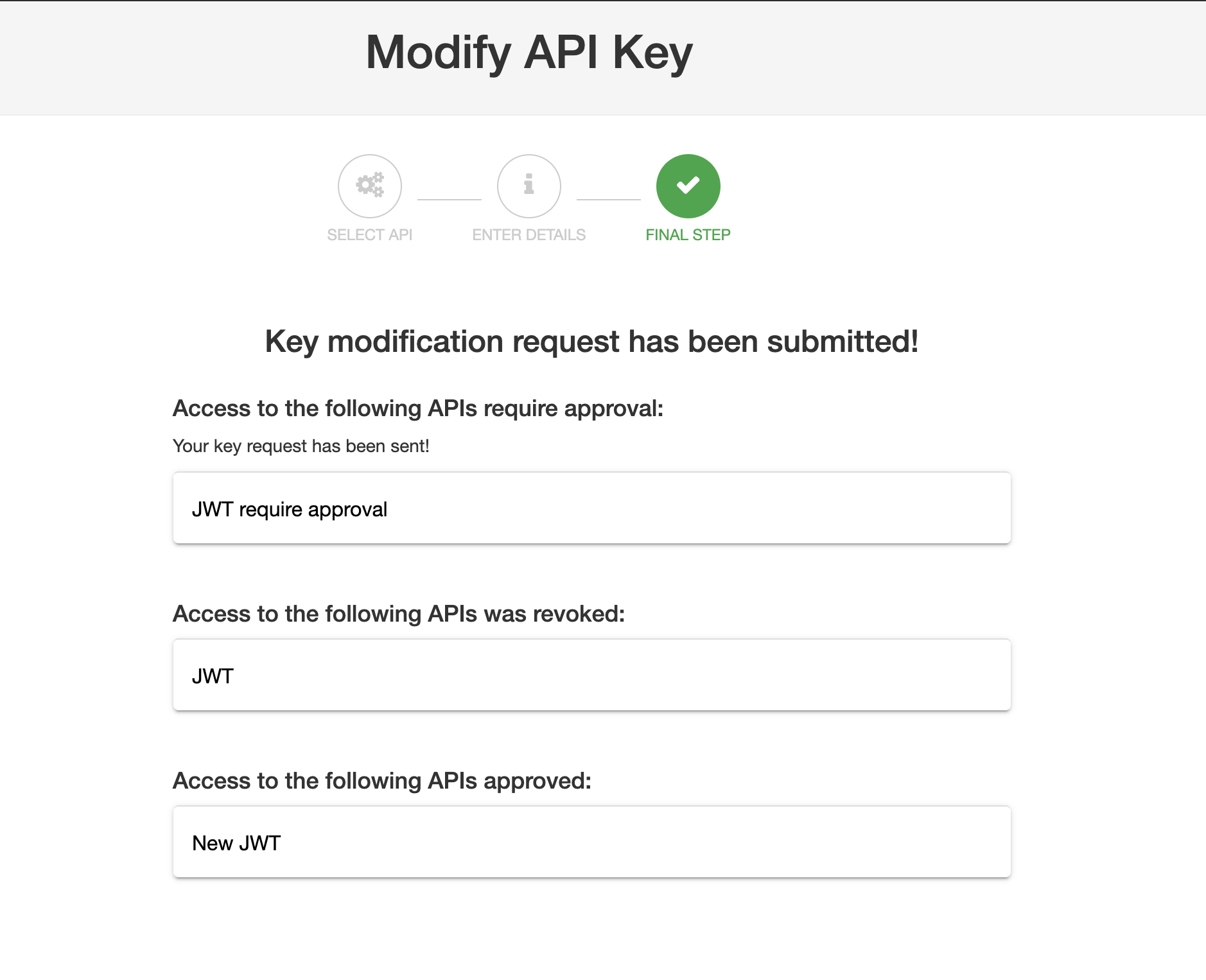
A key request is a record that is generated when a developer requests an access token for an API published in the API Catalog. The Key request encompasses the following information: Read more about them in the Key Request sectionMultiple APIs for a single Key Request
New for v1.9, a developer can now request access to multiple APIs with a single key request. The APIs you group together via a single key should all be of the same authentication type.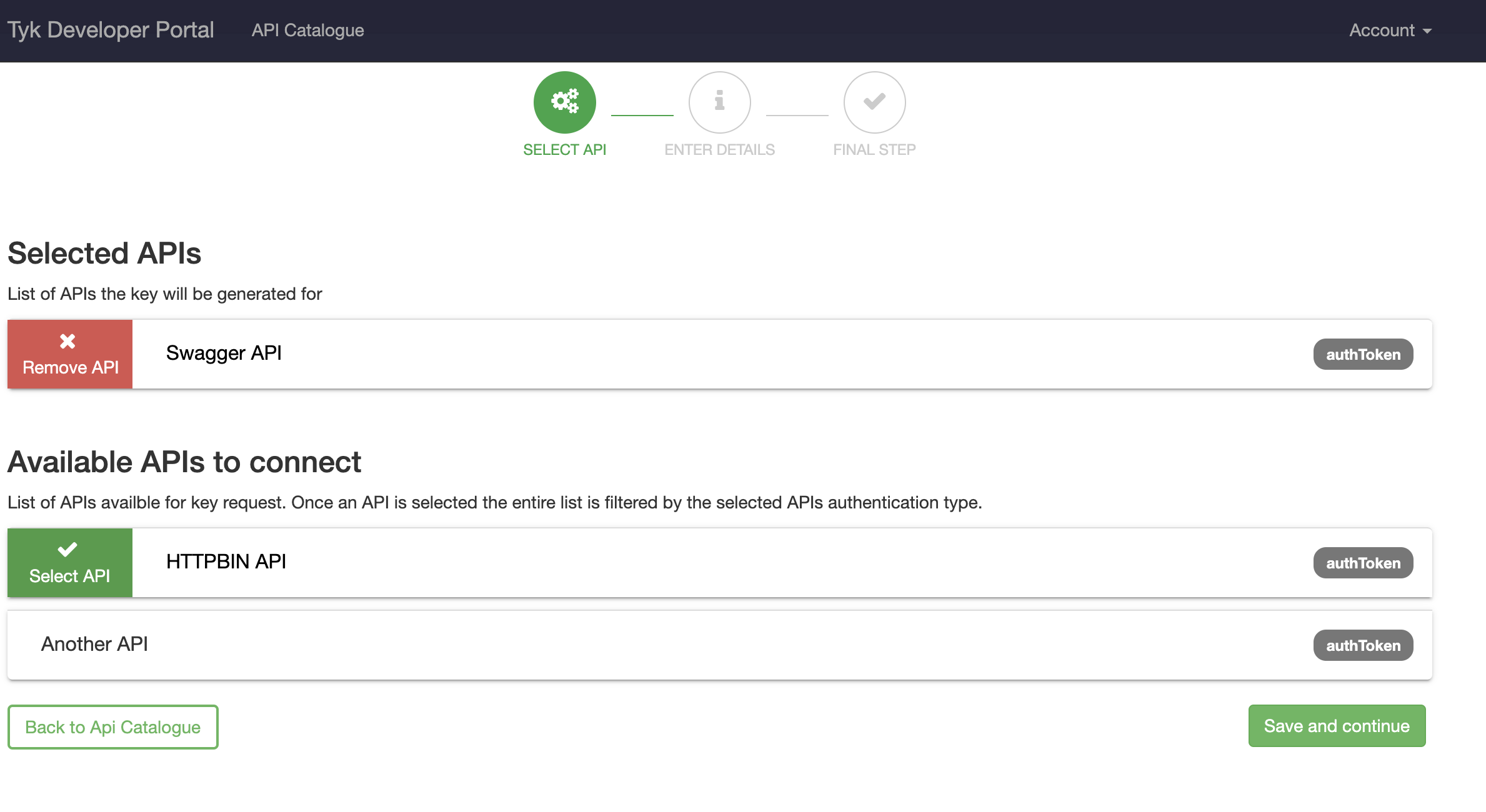
Edit APIs associated with a single Key Request
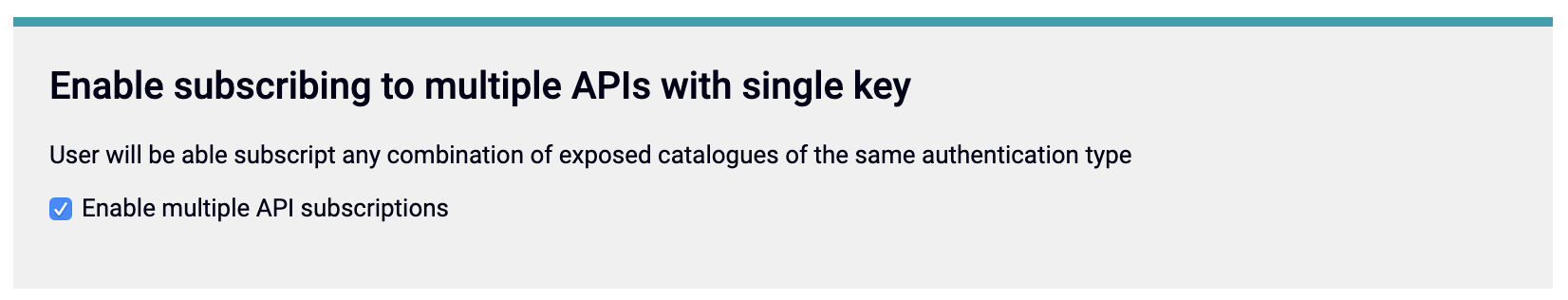
New for v1.9.4, if you have Enable subscribing to multiple APIs with a single key selected you can edit the APIs associated with the Key. You can perform the following:- Remove access to existing APIs
- Subscribe to new APIs (of the same authentication type as the existing ones).
Policies
In the context of the developer portal, a security policy is the main “element” being exposed to public access. The policy is the same as a standard policy, and the policy forms the baseline template that gets used when the portal generates a token for the developer. Security policies are used instead of a one-to-one mapping because they encapsulate all the information needed for a public API program:- Rate limits
- Quota
- Access Lists (What APIs and which versions are permitted)
- Granular access (Which methods and paths are allowed, e.g. you may want to only expose read-only access to the portal, so only GET requests are allowed)
- Multi-policy-management (With a Key, you can assign more than one policy to an APIs and each policy will have it’s own counter).
Documentation
Within the portal, documentation is what a developer can use to learn how to access and use your APIs. The developer portal supports two types of documentation, and will render them differently:- API Blueprint - this is rendered to HTML templates using Jade and Aglio.
-
Swagger/OpenAPI (OpenAPI 2.0 and 3.0 are supported) - either by pasting your Swagger JSON or YAML content into the code editor, or by linking to any public facing Swagger URL. The URL version can be rendered using Swagger UI which offers a sandbox environment where developers can interact with your API from the browser.
Support for API Blueprint is being deprecated. See Importing APIs for more details.