Introduction
Tyk provides flexible multi-authentication capabilities, allowing you to combine various authentication methods using different logical approaches:- AND logic: All configured authentication methods must succeed before granting access
- OR logic: Any one of the configured authentication methods can grant access (Tyk OAS APIs only)
Use Cases
- Multi-tenant APIs: Different tenants using different identity providers
- Migration scenarios: Supporting both legacy and modern auth during transitions
- Partner integrations: External partners use mTLS while internal users use JWT
- Mobile + Web: Different auth methods for different client types
Understanding Authentication Modes
Tyk OAS offers two modes for configuring multiple authentication methods:- Legacy Mode (Default): Maintains backward compatibility with existing Tyk implementations using AND logic only
-
Compliant Mode: Introduced in 5.10.0, provides enhanced flexibility by supporting both AND and OR logic between authentication methods
Tyk Classic APIs and pre-5.10 Tyk OAS APIs only support the legacy mode.
Legacy Mode
The Legacy mode is the traditional implementation of multi-auth, supported by Tyk Classic APIs and Tyk OAS APIs prior to Tyk 5.10. In this mode, all configured authentication methods must be satisfied in the request (i.e., they are combined using AND logic). How does the operation differ between Tyk Classic and Tyk OAS APIs?- Tyk Classic API: All configured authentication methods must be satisfied in the request
-
Tyk OAS API: Only the first security requirement object in the OpenAPI description’s
securityarray is processed. All the authentication methods in the first object must be satisfied in the request, together with any proprietary auth methodsenabledin the Tyk Vendor Extension.
Session Object Handling
In Legacy mode, thebaseIdentityProvider setting determines which authentication method provides the session object. This setting must be configured to one of auth methods in the logical rule using the following mapping:
auth_token- for token-based authenticationjwt_claim- for JWT authenticationbasic_auth_user- for Basic Authenticationhmac_key- for HMAC authenticationcustom_auth- for custom authentication plugin
Compliant Mode
The Compliant mode is named as such because Tyk complies with the security requirements declared in the OpenAPI description, combining different authentication methods using AND and OR logic as required.OpenAPI Security Requirements
In OpenAPI, security is defined using Security Requirement Objects in thesecurity section:
- Each security requirement object in the OAS
securityarray represents an alternative, these are evaluated with OR logic. - Within a single security requirement object, multiple security schemes can be declared and will combined using AND logic (i.e., all listed schemes must succeed together).
- A request is authorized if any one of the defined security requirement objects is successfully validated.
- The session object is determined dynamically based on which security requirement is satisfied
- This structure enables multi-auth configurations, supporting both combined (AND) and alternative (OR) authentication methods.
How OR Logic Works
When using Compliant mode with multiple security requirements:- Tyk attempts each authentication method in sequence
- If any method succeeds, the request is authorized
- If all methods fail, the request is rejected with the error from the last attempted method
How AND Logic Works
Within a single security requirement object that contains multiple schemes:- All schemes within that security requirement must be satisfied (AND logic)
- The request is only authorized if all schemes are valid
- If any scheme fails, the entire security requirement fails, and Tyk moves to the next one
- This allows for combining different authentication methods that must all be present
Examples
Here’s an examplesecurity object from an OpenAPI description with both AND and OR logic:
security object should contain references to security schemes that you’ve defined in the components.securitySchemes section of the OpenAPI description.
In this example, the request will be authorized if either:
scheme1is provided (first security requirement)- OR
- Both
scheme2ANDscheme3are provided (second security requirement with AND logic)
Session Object Handling
The session object (determining rate limits, quotas, and access rights) comes from the successful authentication method. This allows different auth methods to have different associated policies and permissions. When using Compliant mode, the session object handling is more dynamic:- Between different security requirement objects (OR logic): The first security requirement that successfully authenticates will provide the session object.
- Within a single security requirement object (AND logic): When multiple authentication methods are specified in the same requirement object (as in your example below), all methods must pass, and the last successfully processed authentication method will provide the session object.
- Tyk OAuth 2.0
- External OAuth ((deprecated)
- Basic Auth
- HMAC
- JWT
- OpenID Connect (deprecated)
- Custom Plugin Auth
- Bearer / Auth Token (API Key)
Choosing the Right Mode
Use Legacy Mode when:- Migrating from or using Tyk Classic APIs
- You need the session metadata to be taken from an auth method earlier in the middleware processing order
- You need alternative auth methods (OR logic)
- Supporting multiple client types or identity providers
- For APIs that need to serve diverse client bases with different security requirements
- Building new APIs with flexible authentication requirements
Configuration Options
Security Processing Mode
ThesecurityProcessingMode option in the Tyk Vendor Extension allows you to specify which mode to use when processing the security configuration in your API. This controls how Tyk will interpret the authentication settings in the OpenAPI description and the Vendor Extension.
Basic Example: API with Multiple Auth Methods
Here’s a simple example of an OpenAPI description that declares JWT and API Key security schemes:- If the
securityProcessingModein the Tyk Vendor Extension is set tocompliant, Tyk will check incoming requests against eachsecurityoption in turn, authenticating requests using Option 1 or Option 2. - If the
securityProcessingModeis set tolegacy(or is omitted), Tyk will check requests only against the firstsecurityoption (Option 1).
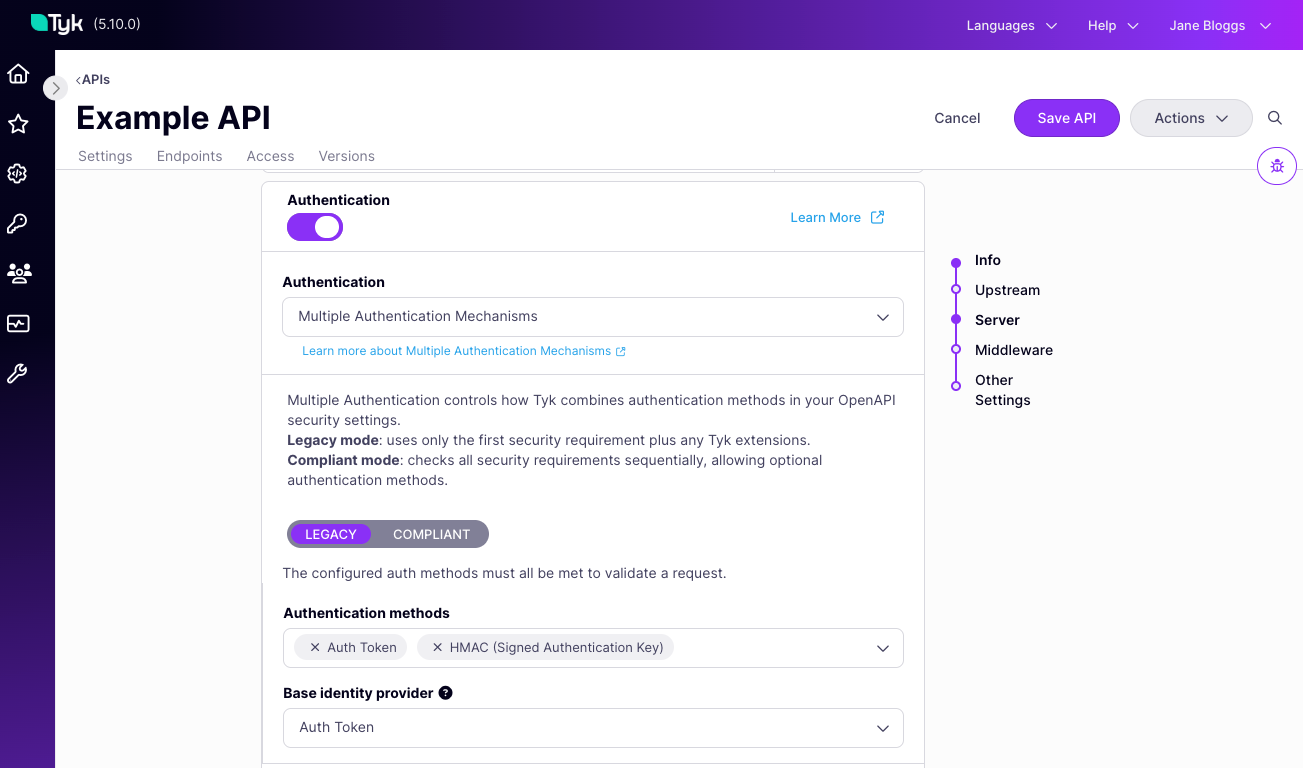
Configuring Multiple Auth Methods in the API Designer
You can configure chained authentication by following these steps:- Enable Authentication in the Servers section
- Select the Multiple Authentication Mechanisms option from the drop-down list.
-
Select the Authentication Mode that you wish to use: Compliant or Legacy
- Compliant mode
- Legacy mode
Select Compliant mode for full interpretation of the security requirements declared in the OpenAPI description, allowing for fully flexible authentication of your API clients: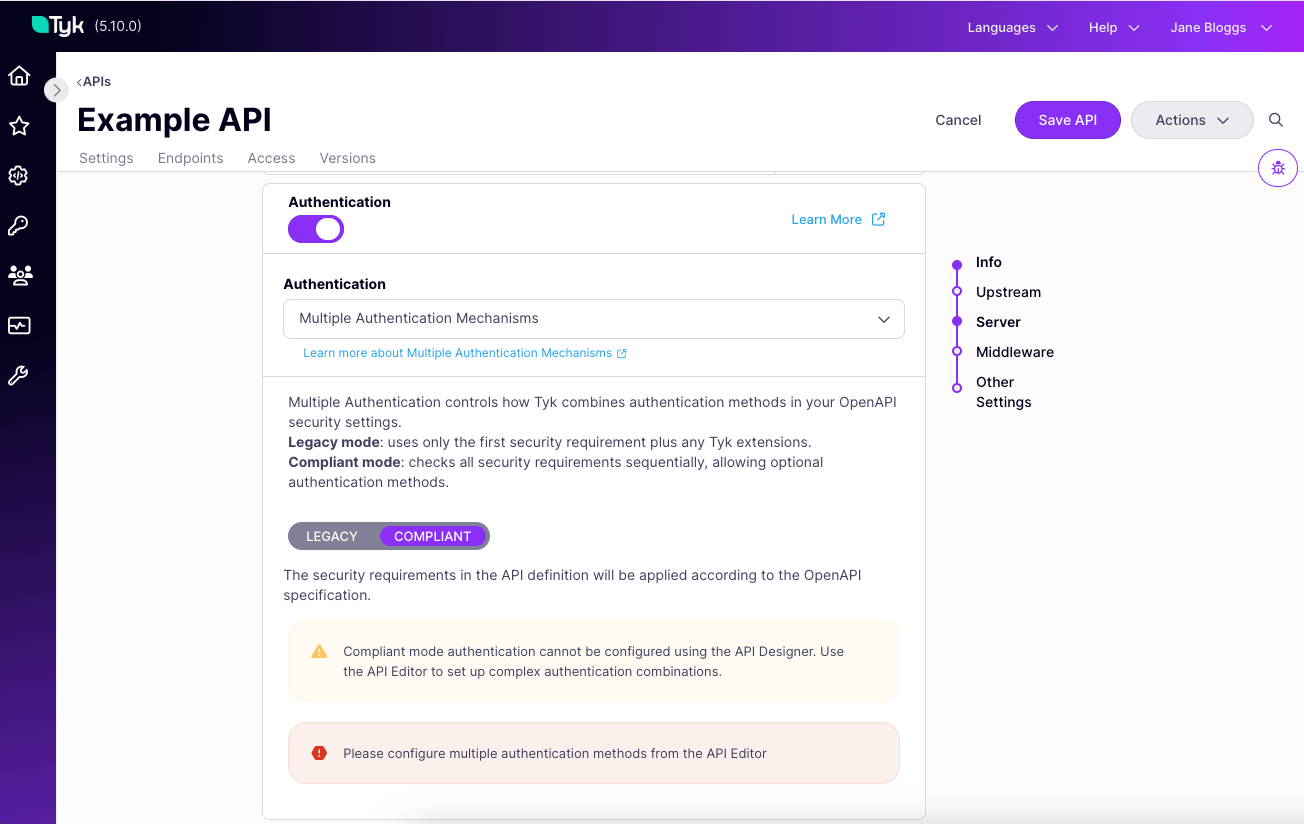
Advanced Configuration
Using Proprietary Auth Methods
Compliant mode allows you to combine standard OpenAPI security schemes with Tyk’s proprietary authentication methods by extending the OpenAPIsecurity section into the Tyk Vendor Extension:
x-tyk-api-gateway.server.authentication.security) are concatenated onto the requirements declared in the OpenAPI description. This configuration allows three authentication methods: JWT, API Key with HMAC, and Custom Auth.
Migration Considerations
Moving from Legacy to Compliant Mode
If you change the security processing mode for an existing API from the Dashboard’s API Designer, Tyk will add the
securityProcessingMode field to your Vendor Extension, but will not make any other changes to the API’s configuration. You may need to make adjustments to the OpenAPI description or Vendor Extension to ensure that the authentication rules are set correctly.- Review your API’s authentication configuration
- Ensure all required security schemes are properly defined, for example any use of Tyk proprietary auth methods (HMAC, custom authentication) will need to be reflected with creation of new security requirements within the Vendor Extension’s
securitysection and removal of requirements from the OpenAPI description’ssecuritysection - Test thoroughly, as authentication behavior will change
- Be aware that the session object may come from different sources depending on which auth method succeeds
Backward Compatibility
Legacy mode ensures backward compatibility with existing Tyk implementations. If you’re unsure which mode to use, start with Legacy mode and migrate to Compliant mode when ready.Troubleshooting
Authentication Fails Unexpectedly
Authentication Fails Unexpectedly
Problem: API returns 401 errors even with valid credentials.Possible Causes & Solutions:
-
Security schemes not properly defined
-
Security schemes not enabled in Tyk extension
-
Mixed Legacy/Compliant configuration
- Ensure you’re not mixing
baseIdentityProvider(Legacy) with complex security arrays (Compliant) - Check that
securityProcessingModematches your intended configuration
- Ensure you’re not mixing
Wrong Policies or Rate Limits Applied
Wrong Policies or Rate Limits Applied
Problem: Requests are authenticated but get unexpected rate limits or access denials.Root Cause: In Compliant mode, the session object comes from whichever authentication method succeeds first.Solutions:
-
Review security requirement order - Place most restrictive auth methods first:
-
Ensure consistent policies across auth methods:
- Verify that API keys and JWT tokens for the same user have similar access rights
- Check that rate limits align with your business logic
-
Debug session source:
Performance Issues
Performance Issues
Problem: Slower response times with multiple authentication methods.Expected Behavior: Some performance impact is normal due to additional processing.Optimization:
-
Order security requirements by likelihood:
-
Monitor authentication attempts:
Debugging Tips
Debugging Tips
Enable detailed logging in your Tyk Gateway to see which authentication methods are being attempted and which one succeeds:Look for these log entries:
Processing multiple security requirements (OR conditions)- Confirms Compliant mode is active
OR wrapperentries- In Compliant mode, this shows which auth methods are being tried
BaseIdentityProvider set to- In Legacy mode, this shows which auth method succeeded