Dashboard SSO with LDAP
The Tyk Dashboard is the command and control center of your Tyk installation. It allows users to manage APIs, policies, keys, etc. All of this data is stored in the Dashboard’s MonogDB database, including the user accounts. This works well in a lot of situations as it allows Tyk to be self-contained, but if you already have a centralised system for managing users then you may prefer to use that instead of a separate Tyk-specific database. Tyk Dashboard uses the Tyk Identity Broker (TIB) to integrate Tyk authentication with 3rd party identity providers (IDPs). You can use this to enable your Dashboard to authenticate users with your LDAP-powered identity providers such as Active Directory.To activate SSO on the Dashboard or Developer portal, there’s no requirement to install TIB separately; it is integrated into the Dashboard and Developer Portal. You have two configurations for SSO within the dashboard:
- Using Embedded TIB: No need to install it separately.
- Using External TIB: If you are using a previous version of the Dashboard or Portal, you can still use SSO with TIB installed as a separate application.
Dashboard SSO with Embedded TIB
Configuring SSO with Embedded TIB is a two-step process:Create Profile
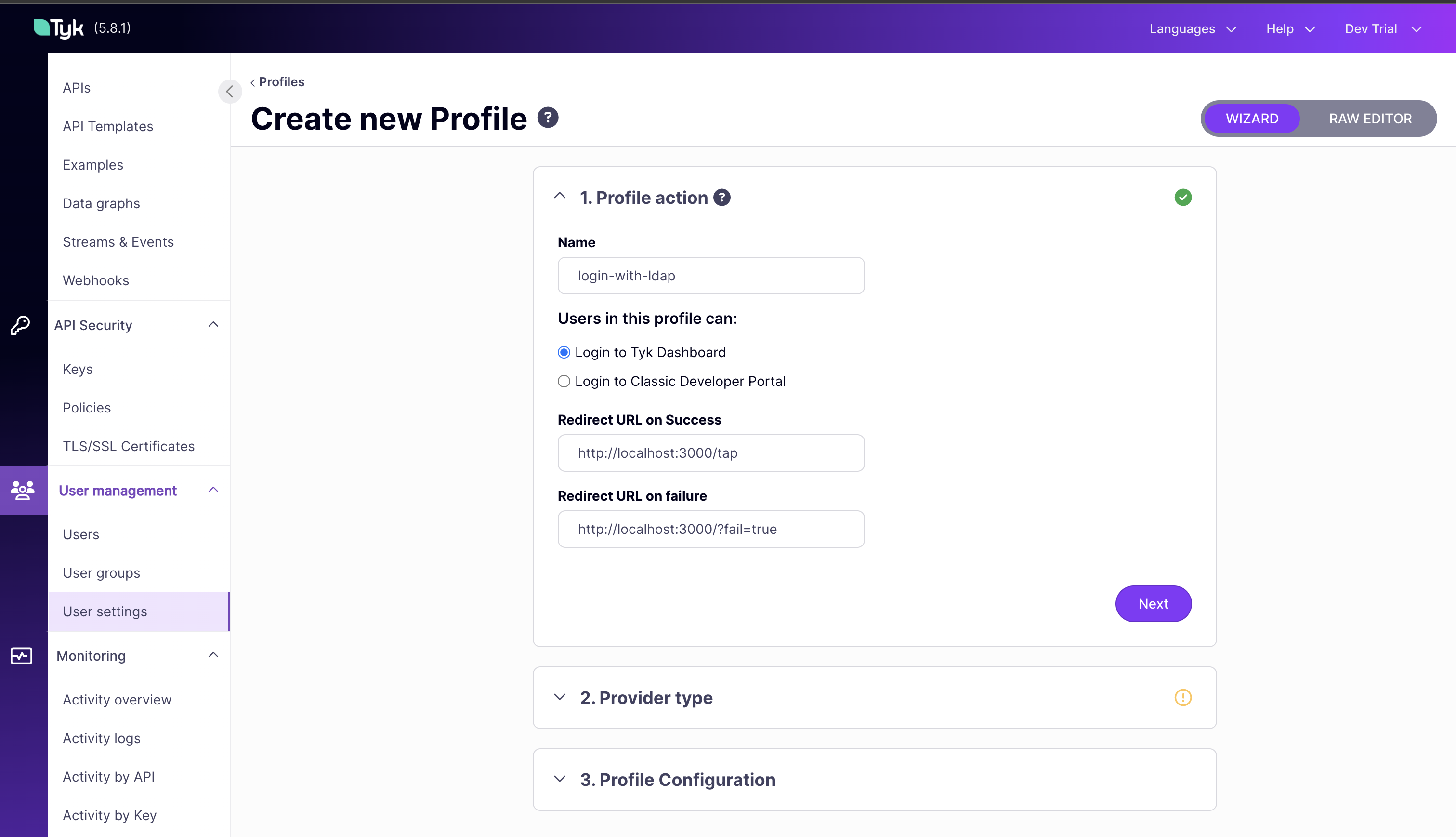
- Log in to your Tyk Dashboard.
- Navigate to User management > User Settings in the Tyk Dashboard sidebar.
- Click the Create Profile button.
- Under the 1. Profile action section:
- In the Name field, enter a descriptive name for your profile (e.g.,
login-with-ldap). - For Users in this profile can:, ensure
Login to Tyk Dashboardis selected. - In the Redirect URL on Success field, enter the URL where users will be redirected after a successful login (e.g.,
http://localhost:3000/tap). - In the Redirect URL on failure field, enter the URL where users will be redirected after a failed login (e.g.,
http://localhost:3000/?fail=true). - Click the Next button.
- In the Name field, enter a descriptive name for your profile (e.g.,
- Under the 2. Provider type section:
- Select
LDAP. - Click the Next button.
- Select
- Under the 3. Profile Configuration section (this will become active/focused after the previous step):
- In the Server field, enter the hostname or IP address of your LDAP server (e.g.,
ldap.forumsys.com). - In the Port field, enter the port number for your LDAP server (e.g.,
389). - In the User DN field, the distinguished name which TIB will use to identify the user - this should be updated to match your LDAP installation and must retain the
*USERNAME*token as this is replaced by the actual username at runtime (e.g.,cn=*USERNAME*,dc=example,dc=com). - (Optional) Click + Advanced Settings (optional) to configure further LDAP settings if needed.
- In the Server field, enter the hostname or IP address of your LDAP server (e.g.,
- Click the Create Profile button.
- Open the created profile and copy the login URL displayed. Save it, as it will be used later in testing. (e.g.,
http://localhost:3000/auth/login-with-ldap/ADProvider)
Testing the SSO Flow
-
Create a login page
TIB works by having credentials sent to it, so a login page must be made in order to fulfill this requirement. For this example we will create a basic login form hosted by Nginx. We can’t just place the login page in our Dashboard directory as the Dashboard is not a standard web server, it only serves the pages which it has been compiled to serve. Any non-compiled page will produce a 404 response.
Install Nginx and start it:
Nginx will now serve pages out of the default web root directory
/usr/share/nginx/www. We now need to create a web page there. This command will pipe the echoed text into a file calledlogin.htmlwhich is stored in the web root:The login form contains two inputs namedusernameandpassword. TIB looks for these exact parameter names when processing the request, so if you are creating your own login page you must use these input names. Please make sure you are usingPOSTmethod in the form, to avoid browser caching. The form actionhttp://localhost:3000/auth/login-with-ldap/ADProvideris the dashboard (embedded TIB) endpoint which will start the authentication process. -
Update the Dashboard config
Update the Dashboard config so that any unauthenticated requests are redirected to your custom login page. We do this by updating the
sso_custom_login_urlproperty of the Dashboard’styk_analytics.conffile, which by default is located in the/opt/tyk-dashboarddirectory. For example (ommitting all other lines in the config file and trailing comma):Since the Dashboard runs on port 3000 by default, this URL will use the default HTTP port of 80 which will be handled by Nginx. -
Test that it works
- Open a web browser (if you’re already logged in to the Dashboard, logout now) and attempt to access the Dashboard -
http://localhost:3000 - This should be redirected to the custom login page -
http://localhost/login.html - Enter
read-only-adminas the username - Enter
passwordas the password - Submit the form
- You should now be logged in to the Dashboard
- Open a web browser (if you’re already logged in to the Dashboard, logout now) and attempt to access the Dashboard -
Dashboard SSO with External TIB
This guide assumes you already have a Tyk environment set up, with a Gateway and Dashboard. If you don’t, please follow the Tyk Self-Managed getting started guide. The environment used for this guide is, for simplicity’s sake, all contained on a single host running Ubuntu 14.04. The hostnamemy-tyk-instance.com has been set to point at 127.0.0.1. For production environments it is recommended that each component is hosted separately and appropriate security measures are used such as HTTPS to secure connections.
All commands shown are run from inside the Tyk host environment.
Setup TIB
-
Download TIB
You can download TIB from the releases page of the TIB repository on GitHub. The release names contain the architecture and version i.e.
tib-linux-<architecture>-<version>.tar.gz. This example usesamd64and0.2.1for all the commands, but you should update them to use the latest version and relevant architecture for your platform. First step is to download TIB onto the environment: -
Extract and store TIB
As the other Tyk components are installed in your
/optdirectory, we recommend you install TIB there too:TIB will now be extracted to the directorytib-0.2.1, let’s move this to/optand change to that directory: -
Configure TIB
There are two configuration files for TIB:
tib.conffor the main application configuration settingsprofiles.jsonto configure the profiles which TIB will attempt to authenticate against
Secret: The REST API secret used when configuring TIB remotelyTykAPISettings.GatewayConfig.Endpoint: The URL through which TIB can communicate with your Tyk GatewayTykAPISettings.GatewayConfig.Port: The port through which TIB can communicate with your Tyk GatewayTykAPISettings.GatewayConfig.AdminSecret: The secret required for TIB to communicate with your Tyk Gateway REST API - must match thesecretproperty in your Gateway’styk.confTykAPISettings.DashboardConfig.Endpoint: The URL through which TIB can communicate with your Tyk DashboardTykAPISettings.DashboardConfig.Port: The port through which TIB can communicate with your Tyk DashboardTykAPISettings.DashboardConfig.AdminSecret: The secret required for TIB to communicate with your Tyk Dashboard Admin REST API - must match theadmin_secretproperty in your Dashboard’styk_analytics.conf
tib.conffor this example is as follows (yours might require different values):
Create Profile
-
Set up the LDAP profile
TIB ships with a default
profiles.jsonfile which contains many example configuration for different scenarios. This guide is focused on LDAP authentication for the Dashboard, so we will updateprofiles.jsonto contain a single profile for this purpose. The key attributes for LDAP profile are:ID: The ID by which we will activate the profile by calling the appropriate TIB endpointOrgId: The organization id which the profile is connected to - make sure this is the correct id for your organization (see the Dashboard Admin API documentation for details on how to retrieve this)IdentityHandlerConfig.DashboardCredential: The Dashboard API Access credential which is used as authorization headerProviderConfig.FailureRedirect: The URL which TIB will redirect to if the authentication failsProviderConfig.LDAPPort: The port through which TIB can communicate with your LDAP serverProviderConfig.LDAPServer: The URL through which TIB can communicate with your LDAP serverProviderConfig.LDAPUserDN: The distinguished name which TIB will use to identify the user - this should be updated to match your LDAP installation and must retain the*USERNAME*token as this is replaced by the actual username at runtimeReturnURL: The URL which TIB will redirect to if the authentication succeeds - this should be the/tapendpoint of your Tyk Dashboard
profiles.jsonfor this example is as follows (again, update values for your environment):Notice that this is a JSON array object with a single element; an LDAP profile. The LDAP server referenced by this profile is the freely-available service provided forumsys.com. See their documentation for more information. You can use any OpenLDAP compatible server. -
Start TIB
Start TIB by executing the TIB binary. This will produce an output log into the console which you can use to watch TIB process requests. Since TIB looks for the config file in the local directory, you should execute the application from there too.
If all is well you should see TIB output a few messages when it starts:Start a new shell session to carry on with the remaining process.
Test the SSO Flow
-
Create a login page
TIB works by having credentials sent to it, so a login page must be made in order to fulfill this requirement. For this example we will create a basic login form hosted by Nginx. We can’t just place the login page in our Dashboard directory as the Dashboard is not a standard web server, it only serves the pages which it has been compiled to serve. Any non-compiled page will produce a 404 response.
Install Nginx and start it:
Nginx will now serve pages out of the default web root directory
/usr/share/nginx/www. We now need to create a web page there. This command will pipe the echoed text into a file calledlogin.htmlwhich is stored in the web root:The login form contains two inputs namedusernameandpassword. TIB looks for these exact parameter names when processing the request, so if you are creating your own login page you must use these input names. Please make sure you are usingPOSTmethod in the form, to avoid browser caching. The form actionhttp://my-tyk-instance.com:3010/auth/1/ldapis the TIB endpoint which will start the authentication process. The URL can be broken down as follows:http://my-tyk-instance.com: The method and hostname used to connect to TIB - you should use HTTPS to prevent confidential data from being exposed3010: The default port for TIBauth: The special TIB endpoint which accepts authentication requests1: The number of the profile which we are using - matches against theIDproperty of the profile inprofiles.jsonldap: We need to add a string to the end of the request, so we have usedldaphere
-
Update the Dashboard config
Update the Dashboard config so that any unauthenticated requests are redirected to your custom login page. We do this by updating the
sso_custom_login_urlproperty of the Dashboard’styk_analytics.conffile, which by default is located in the/opt/tyk-dashboarddirectory. For example (ommitting all other lines in the config file and trailing comma):Since the Dashboard runs on port 3000 by default, this URL will use the default HTTP port of 80 which will be handled by Nginx. -
Test that it works
Now that we have TIB installed and configured, Nginx installed and hosting our custom login page, and the Dashboard configured to redirect to that login page we can now test the solution. Remember that this example is using the LDAP provided at forumsys.com, so if you are using your own LDAP then substitute the username and password with appropriate values from your system.
- Open a web browser (if you’re already logged in to the Dashboard, logout now) and attempt to access the Dashboard -
http://my-tyk-instance.com:3000 - This should be redirected to the custom login page -
http://my-tyk-instance.com/login.html - Enter
read-only-adminas the username - Enter
passwordas the password - Submit the form
- You should now be logged in to the Dashboard
- Open a web browser (if you’re already logged in to the Dashboard, logout now) and attempt to access the Dashboard -
Advance LDAP Configuration
The LDAP Identity Provider gives you functionality to bind a user to an LDAP server based on a username and password configuration. The LDAP provider currently does not extract user data from the server to populate a user object, but will provide enough defaults to work with all handlers.Log into the Dashboard using LDAP
Below is a sample TIB profile that can be used to log a user into the Dashboard using an LDAP pass-through provider:- Two form fields called “username” and “password”
- A basic auth header using the Basic Authentication standard form
"GetAuthFromBAHeader": true to the ProviderConfig section.
The request should be a POST.
If you make this request with a valid user that can bind to the LDAP server, Tyk will redirect the user to the dashboard with a valid session. There’s no more to it, this mechanism is pass-through and is transparent to the user, with TIB acting as a direct client to the LDAP provider.
The
LDAPUserDN field MUST contain the special *USERNAME* marker in order to construct the users DN properly.Generate an OAuth token using LDAP
The configuration below will take a request that is posted to TIB, authenticate it against LDAP, if the request is valid, it will redirect to the Tyk Gateway OAuth clients’Redirect URI with the token as a URL fragment:
Log into the Developer Portal using LDAP
LDAP requires little configuration, we can use the same provider configuration that we used to log into the Dashboard to target the Portal instead - notice the change in the handler configuration and the return URL:POST request is all that is needed to validate a user via an LDAP provider.
Using advanced LDAP search
In some cases validation of a user CN is not enough, and it requires verifying if a user match some specific rules, like internal team ID. In this case TIB provides support for doing additional LDAP search check, and if result of this search returns only 1 record, it will pass the user. To make it work you need to specify 3 additional attributes in profile configuration file:LDAPBaseDN- base DN used for doing LDAP search, for examplecn=dashboard,ou=GroupLDAPFilter- filter applied to the search, should include the*USERNAME*variable. For example:((objectCategory=person)(objectClass=user)(cn=*USERNAME*))LDAPSearchScope- This specifies the portion of the target subtree that should be considered. Supported search scope values include: 0 - baseObject (often referred to as “base”), 1 - singleLevel (often referred to as “one”), 2 - wholeSubtree (often referred to as “sub”)