JWT and Auth0 with Tyk
Overview
This will walk you through securing your APIs with JWTs via Auth0. We also have the following video that will walk you through the process.
Prerequisites
- A free account with Auth0
- A Tyk Self-Managed or Cloud installation
Create an application in Auth0
- Log in to your Auth0 account.
- Select APIs from the Applications menu.
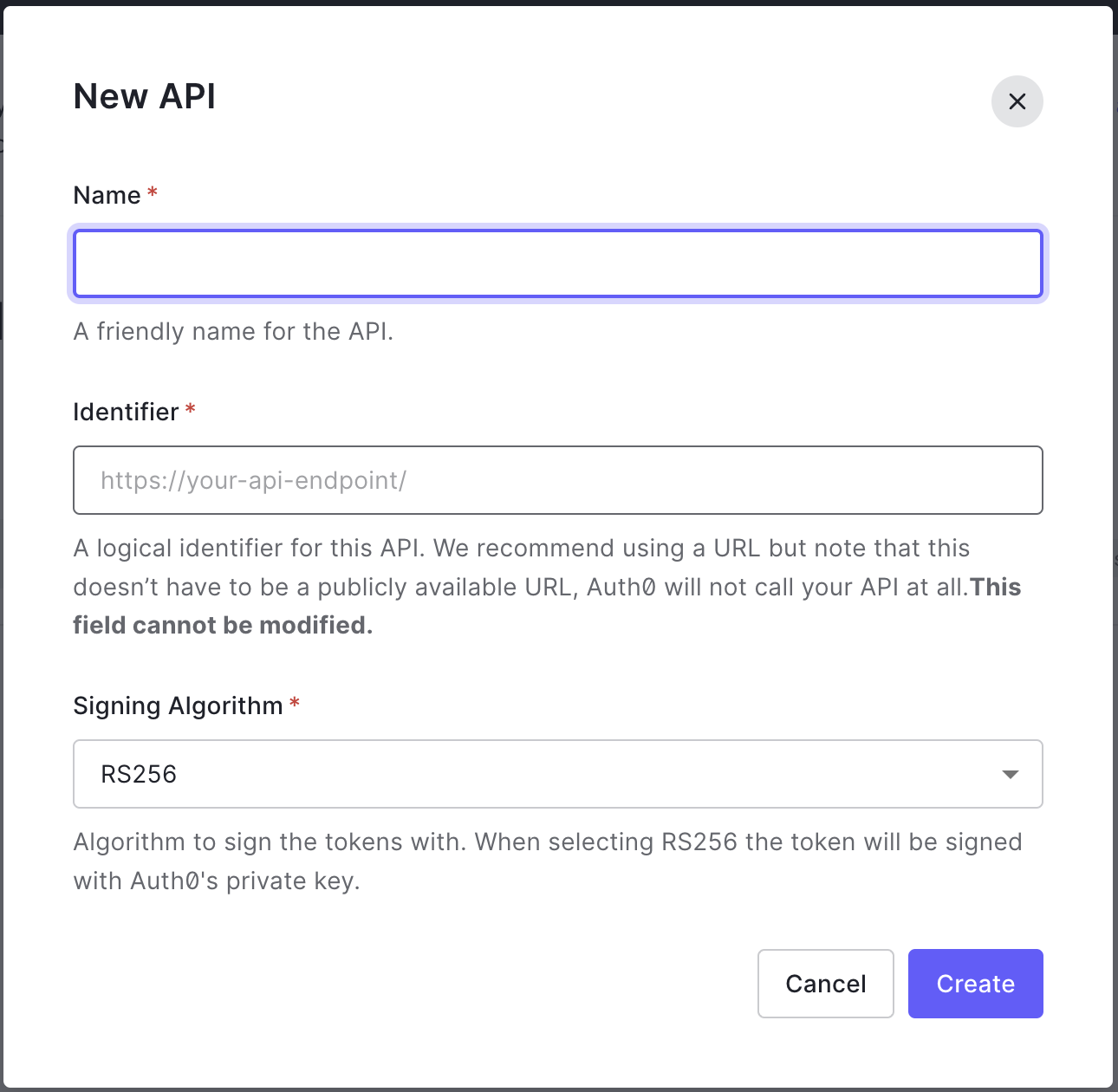
- Click Create API and enter a name and identifier for your API.
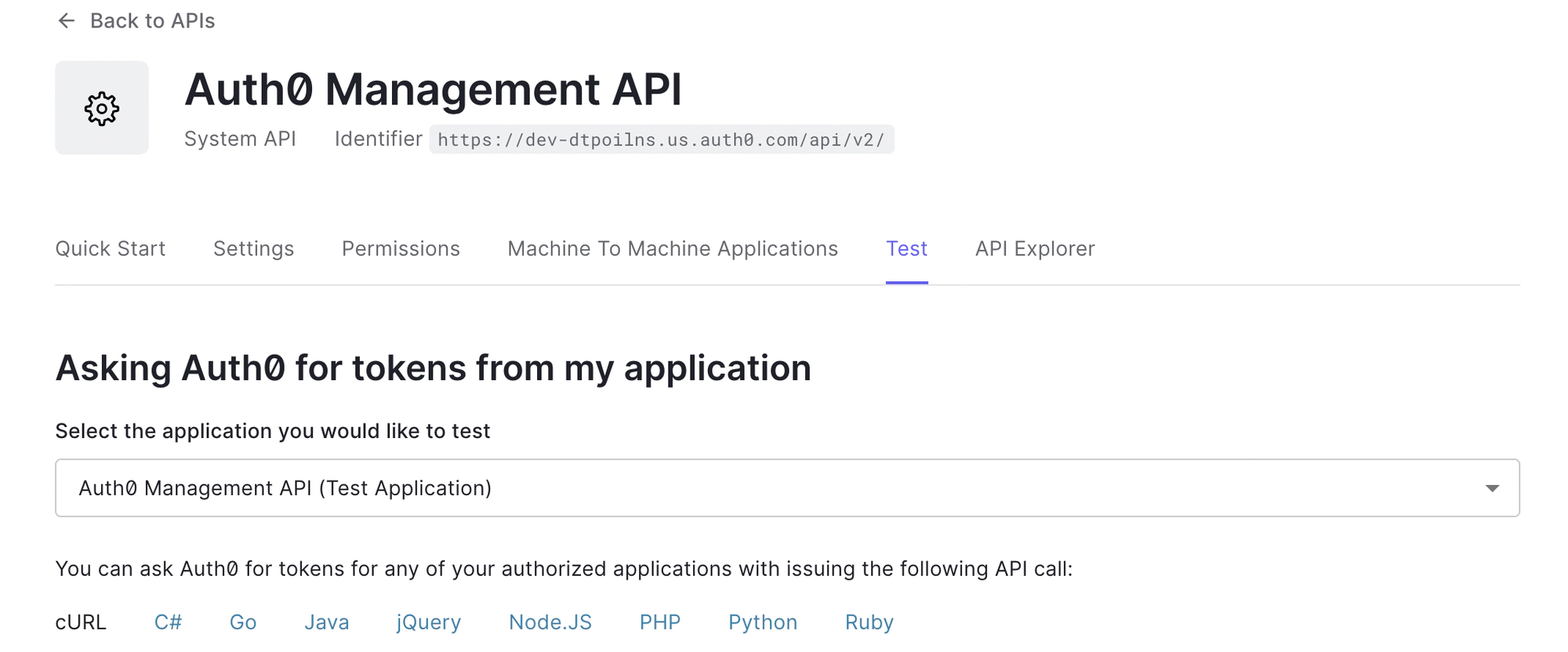
- From the Test tab, follow the instructions on how to get an access token.
- From the cURL tab copy the token request command.
curl --request POST \
--url https://dev-yjd8e8u5.us.auth0.com/oauth/token \
--header 'content-type: application/json' \
--data '{"client_id":{CLIENT_ID},"client_secret":{CLIENT_SECRET},"audience":{AUDIENCE},"grant_type":"client_credentials"}'
- Paste the command in a terminal window to generate your token. Save this token locally.
{
"access_token": "xxxxxxxxxxx",
"token_type": "Bearer"
}
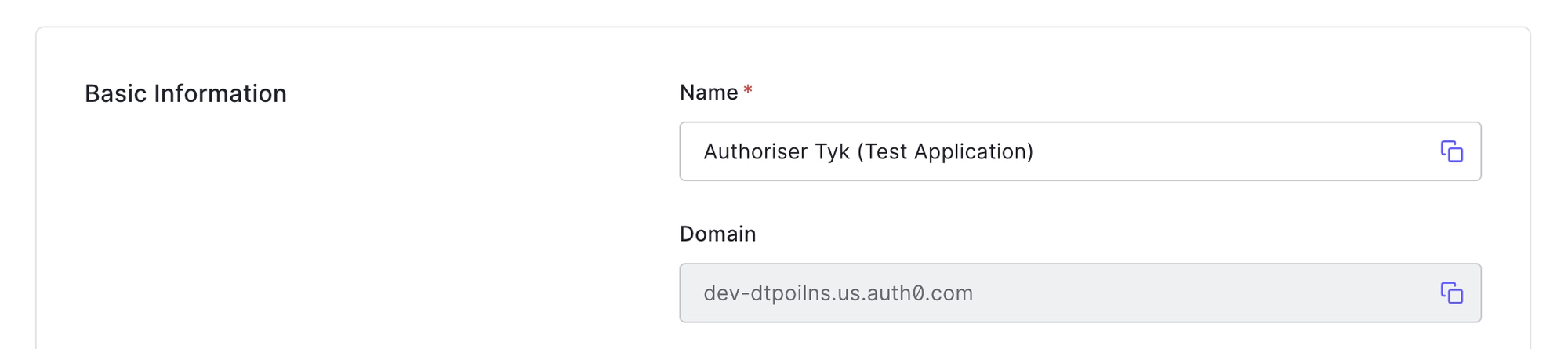
- After creating your API, a new Auth0 Application will be created. Go to the Applications section to view it.
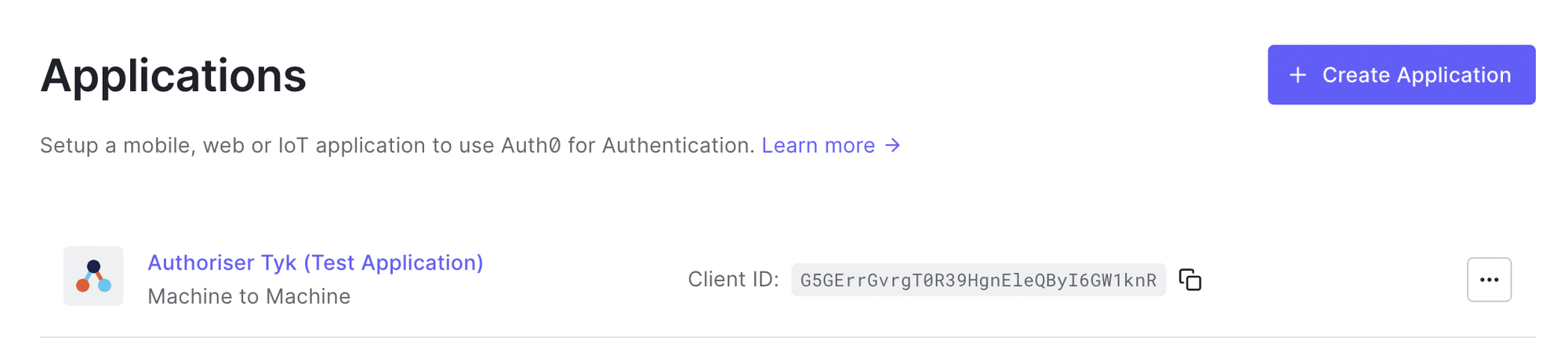
- Copy the Domain from the Basic Information. You will use this when adding an API to Tyk.
Create your API in Tyk
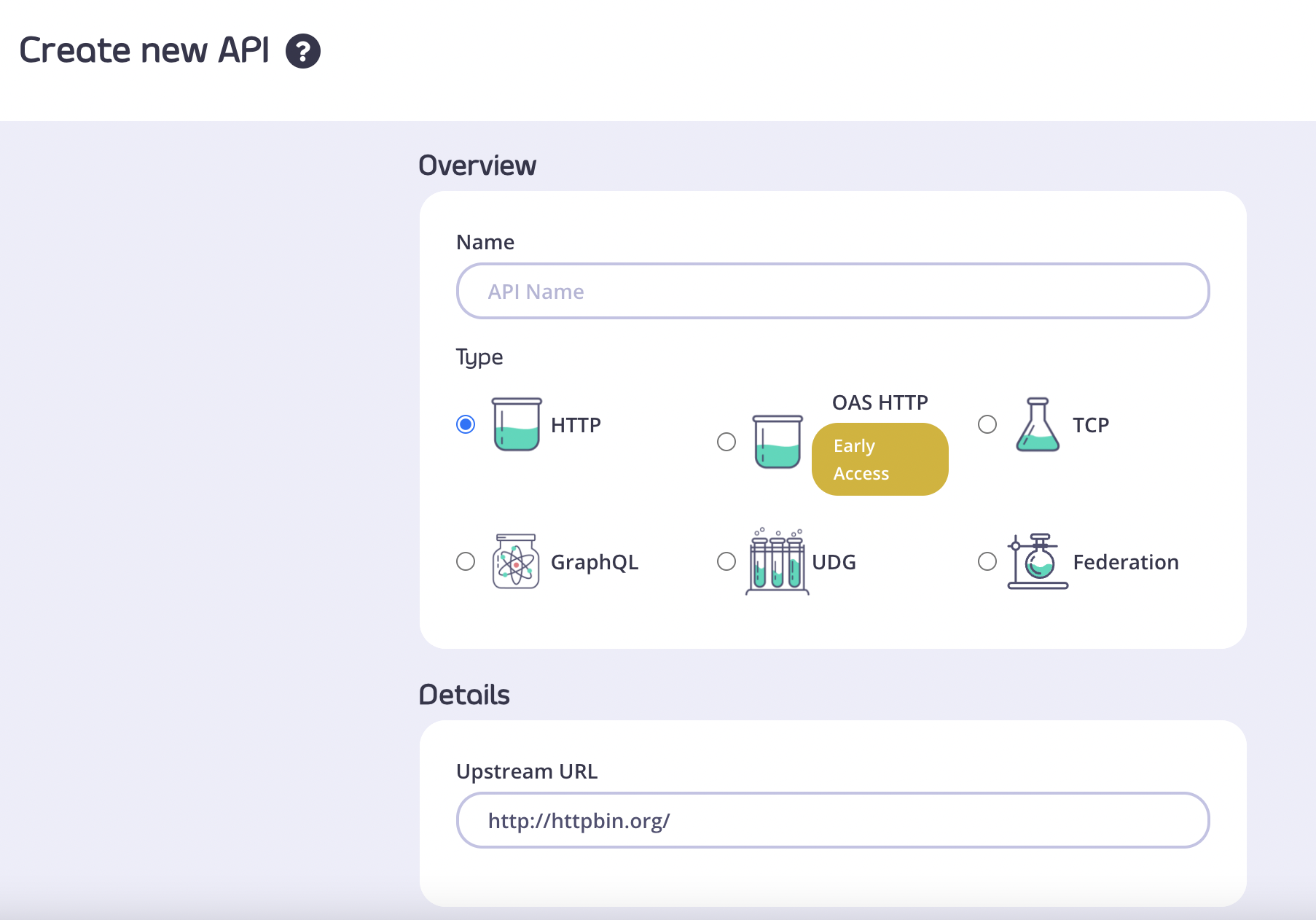
- Log in to your Tyk Dashboard
- Create a new HTTP API (the default http://httpbin.org upstream URL is fine)
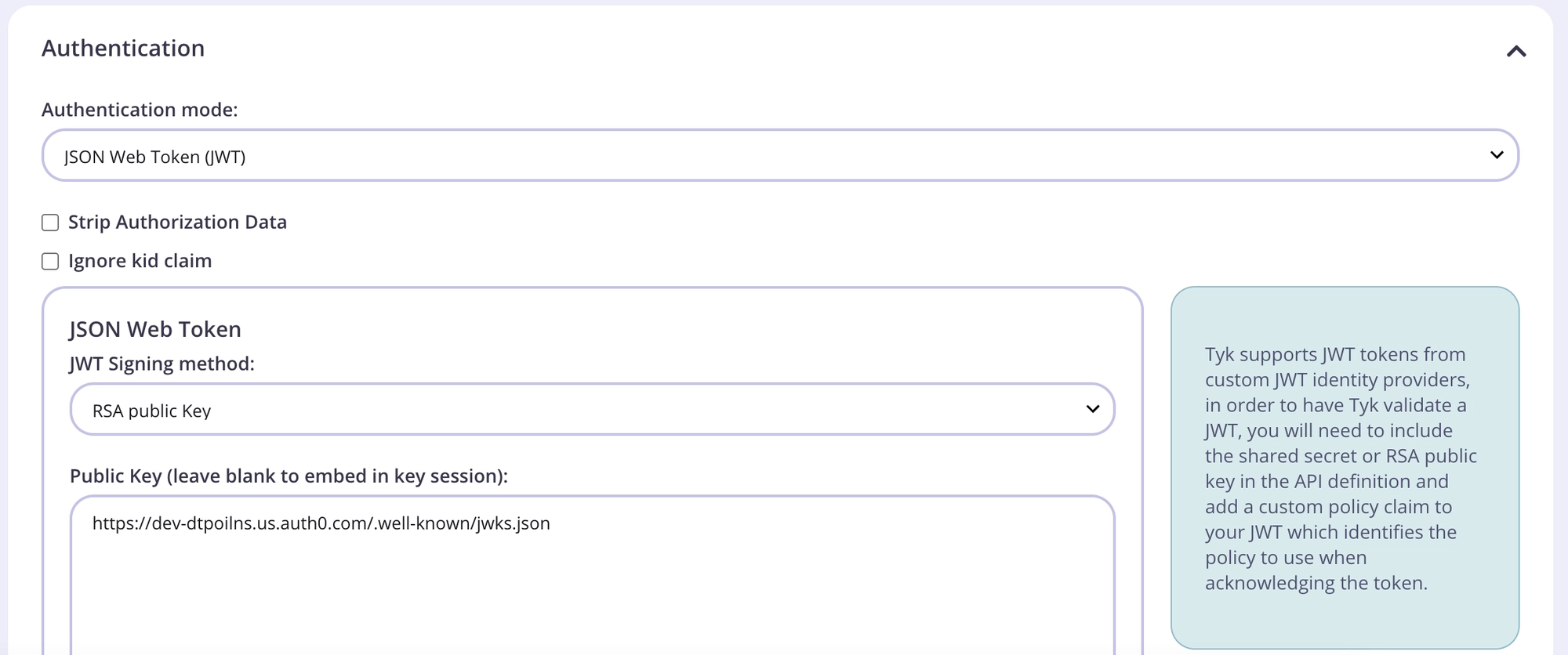
- From the Authentication section, select JSON Web Token (JWT) as your authentication mode.
- Select RSA public Key as the JWT signing method.
- Enter your Auth0 Application Domain from Step 8 above to complete the
jwks_uriend pointhttps://<<your-auth0-domain>>/.well-known/jwks.json - Copy your
jwks_uriin to the Public Key field.
- Add an Identity Source and Policy Field Name. The defaults of
subandpolare fine. - Save your API.
- From the System Management section, select Policies
- Click Add Policy
- Select your Auth0 API
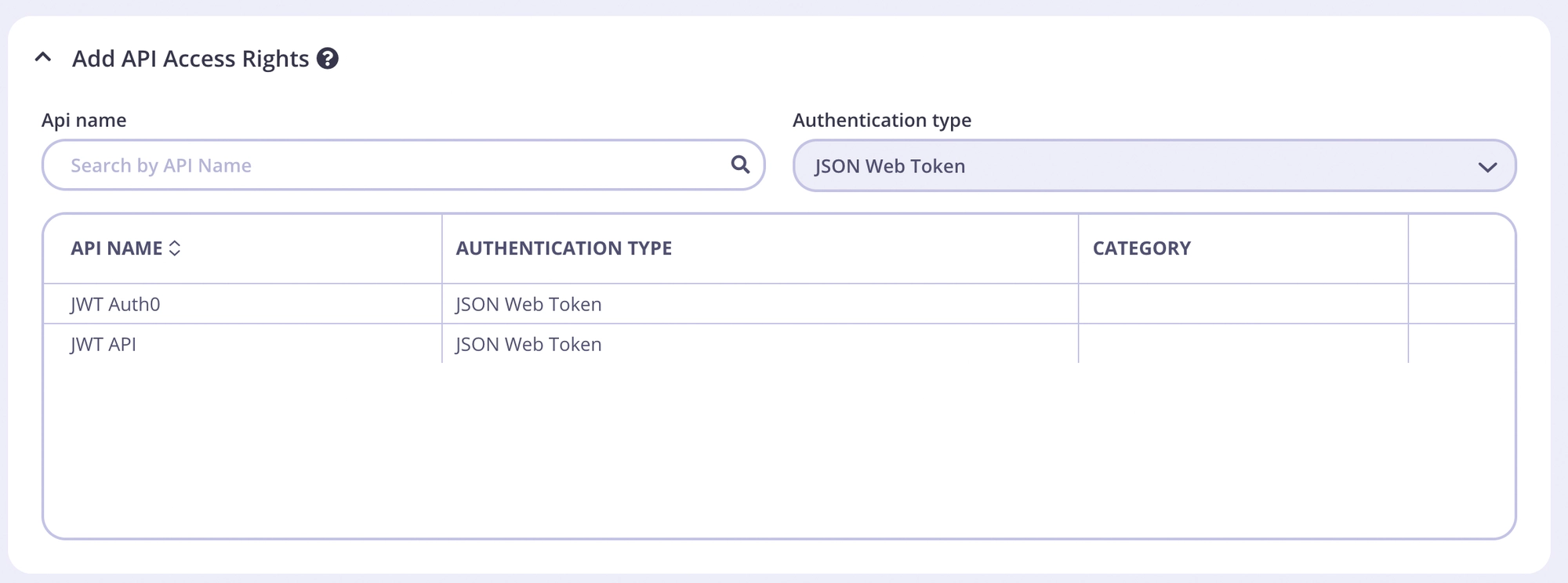
- You can keep the rest of the access rights at the defaults.
- Click the Configurations tab and enter a Policy Name and a Keys Expiry after period.
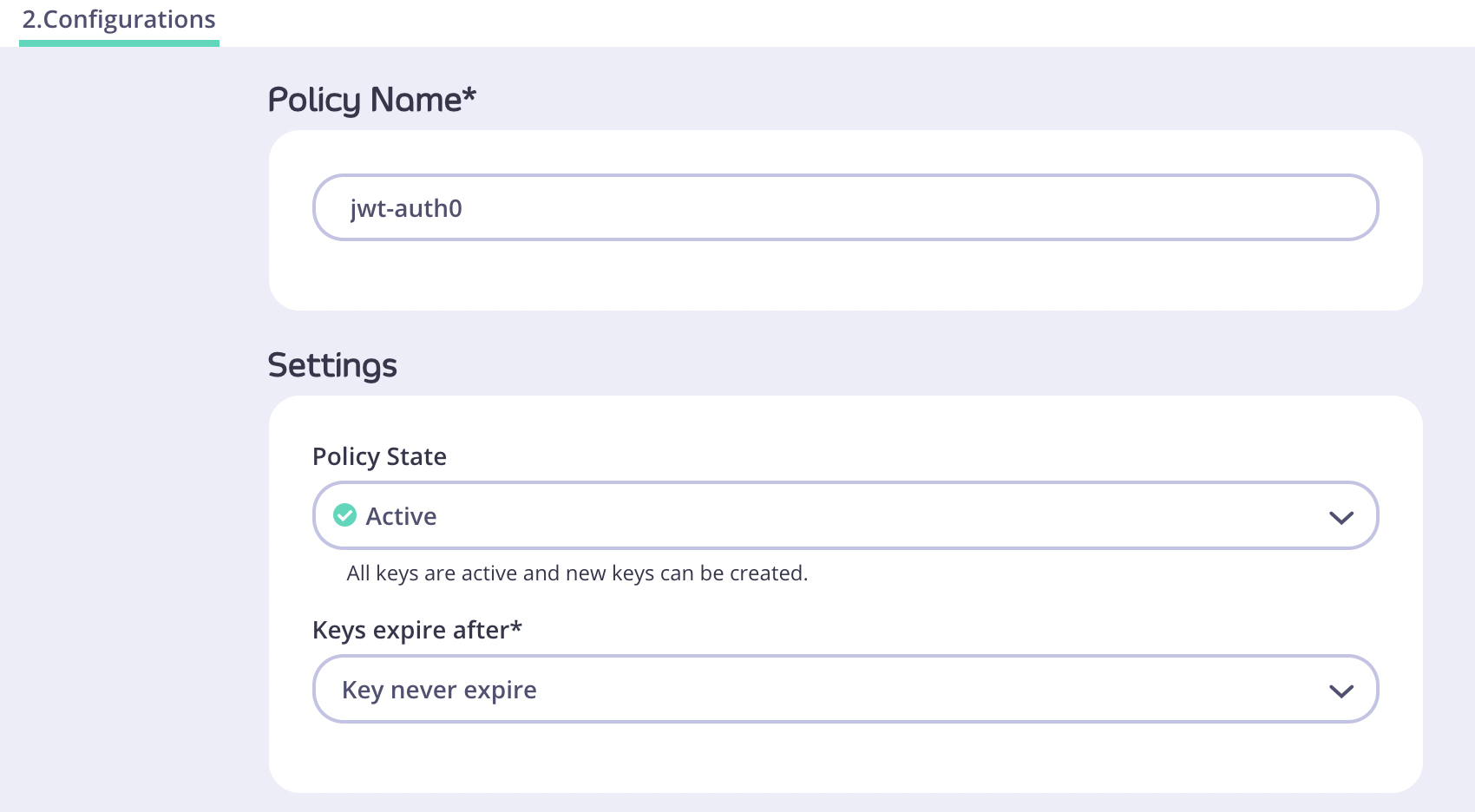
- Click Create Policy.
- Edit your JWT Auth0 API and add the policy you created as the Default Policy from the Authentication section.
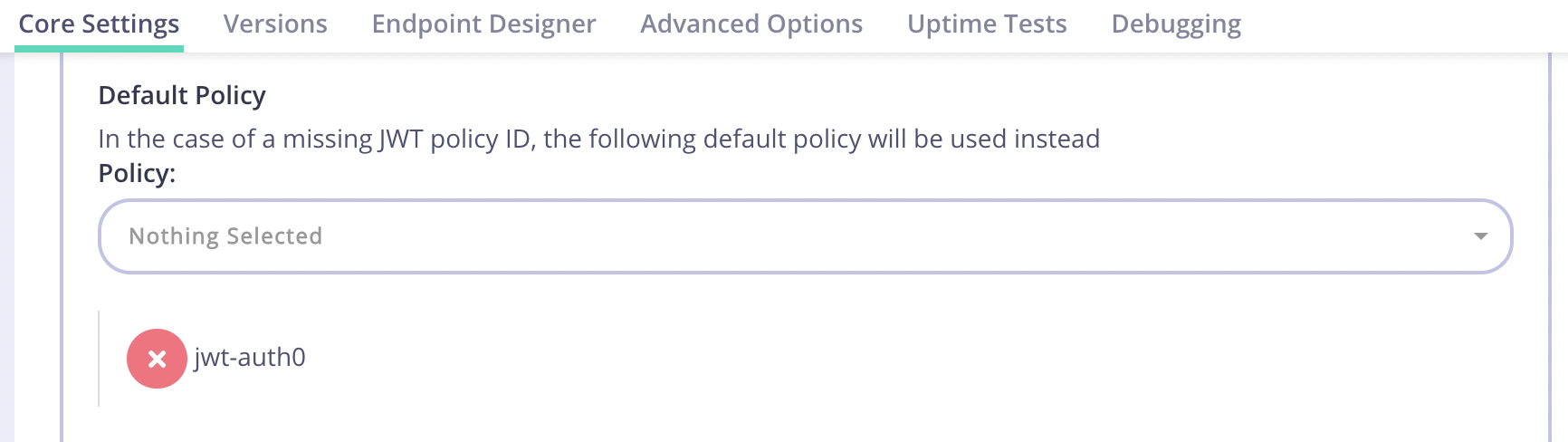
- From the top of the API copy the API URL
- From a terminal window using the API URL and the Auth0 generated token.
curl -X GET {API URL} -H "Accept: application/json" -H "Authorization: Bearer {token}"
- If using the httpbin upstream URL as in the example Tyk API, you should see the HTML returned for the httpbin service in your terminal.
- If there is an error with the request, you will see the following error message.
{
"error": "Key not authorized:Unexpected signing method."
}
