Introduction
Tyk Self-Managed is a full-featured API management platform that you deploy and control on-premise, within your own infrastructure. This page will guide you through setting up and exploring your Self-Managed Tyk environment.What’s included in your trial
Your Tyk Self-Managed trial includes:- Tyk Gateway: The core API Gateway that handles all your API traffic
- Tyk Dashboard: A REST API with a web interface for managing your APIs, policies, and monitoring
- Developer Portal: A customizable API portal to securely publish and manage API access for your consumers.
- Monitoring: Detailed insights into API usage and performance
- Sample APIs: Pre-configured APIs to help you explore Tyk’s capabilities
System Requirements
- Docker: Docker Engine 20.10.0 or newer
- CPU & Memory: Minimum 2 GB RAM and 2 CPU cores
- License Key: A valid Tyk Self-Managed license key. You can quickly get started with a self-managed trial license by completing the registration on our website. After registering, you’ll receive an email containing your license key. If you’d rather have guided assistance, we recommend checking out our Tyk Technical PoC Guide.
Trial Duration and Limitations
Your trial license is valid for 14 days from activation. During this period, you have access to all Enterprise features. After the trial period, you’ll need to purchase a license to continue using Tyk Self-Managed. To continue using Tyk Self-Managed after your trial, please contact our team to discuss licensing options. Contact usQuick Setup
This section provides a step-by-step guide to quickly set up Tyk Self-Managed using Docker.Prerequisites
- Install Docker on your system
- Install the following CLI tools:
- Tyk Self-Managed license key (from your trial email)
- If you are having issues with your trial license, please contact info@tyk.io
Installation
-
Clone the repository:
-
Create a
.envfile at the root of your installation Create a file named.envin the root directory of your cloned repository and add your license key:You can use the included.env.examplefile as a reference or starting point.Note: Files starting with a dot (like
.env) are hidden by default in Unix-based systems. Use thels -acommand to view them in your terminal. -
Start the Tyk stack:
This command will download and start all the necessary containers:
- Tyk Gateway
- Tyk Dashboard
- Developer Portal
- Redis (Gateway dependency for caching)
- PostgreSQL (Dashboard and Portal dependency for data storage)
- Tyk Pump (for analytics)
- Sample API service (httpbin)
-
Once all containers are running, you can verify their status with:
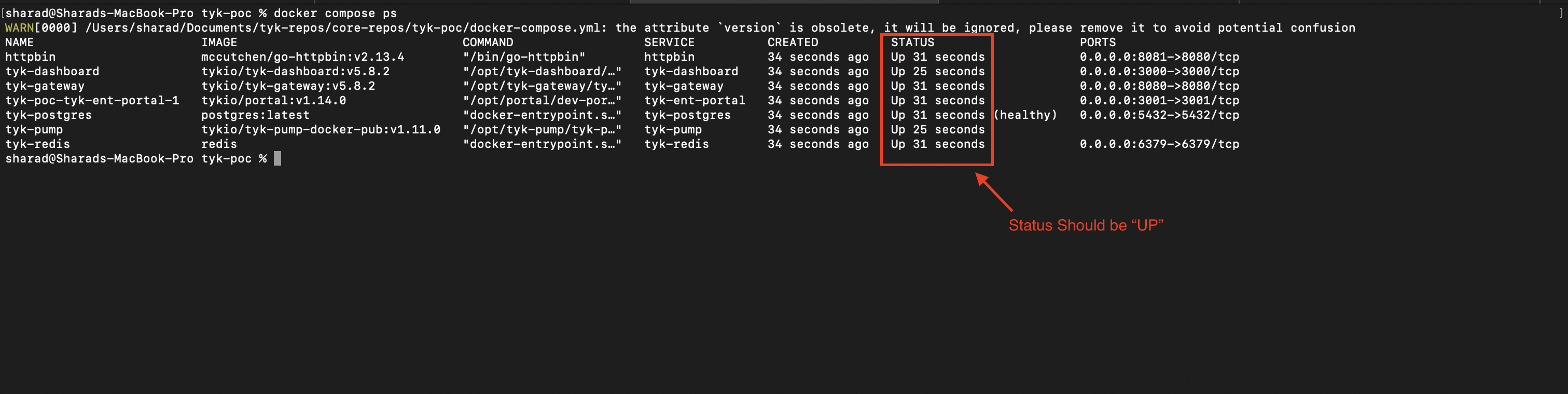
Default Credentials and Access Points
Once the installation is complete, you can access the following components:Verifying Your Installation
-
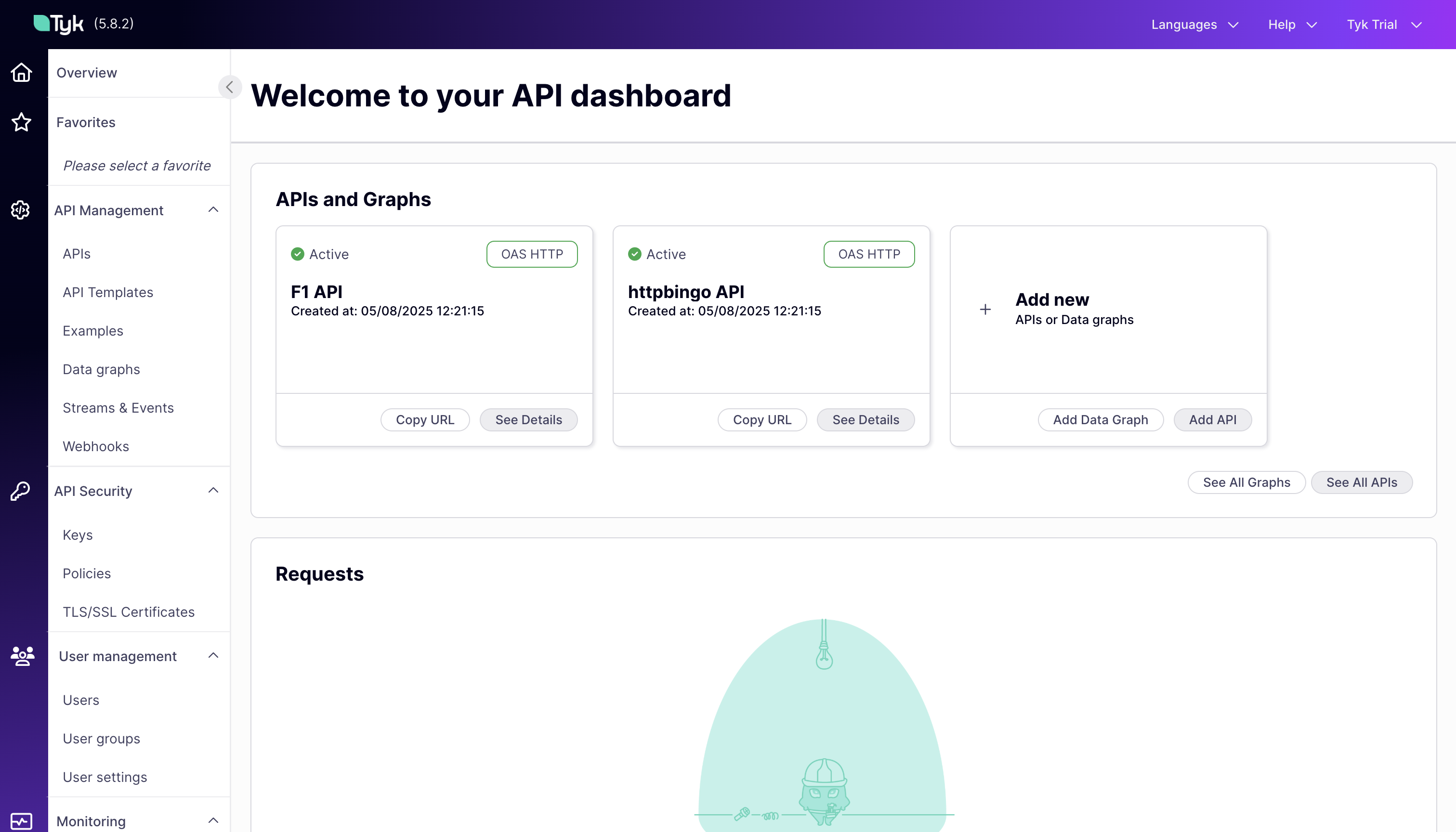
Verify Dashboard Access:
- Open your browser and navigate to
http://localhost:3000 - Log in with the default credentials (developer@tyk.io / specialpassword)
- You should see the Tyk Dashboard with pre-configured APIs and monitoring
- Open your browser and navigate to
-
Verify Gateway Access:
- Open a terminal and run:
- You should receive a JSON response from the API, confirming that the Tyk Gateway is functioning correctly.
-
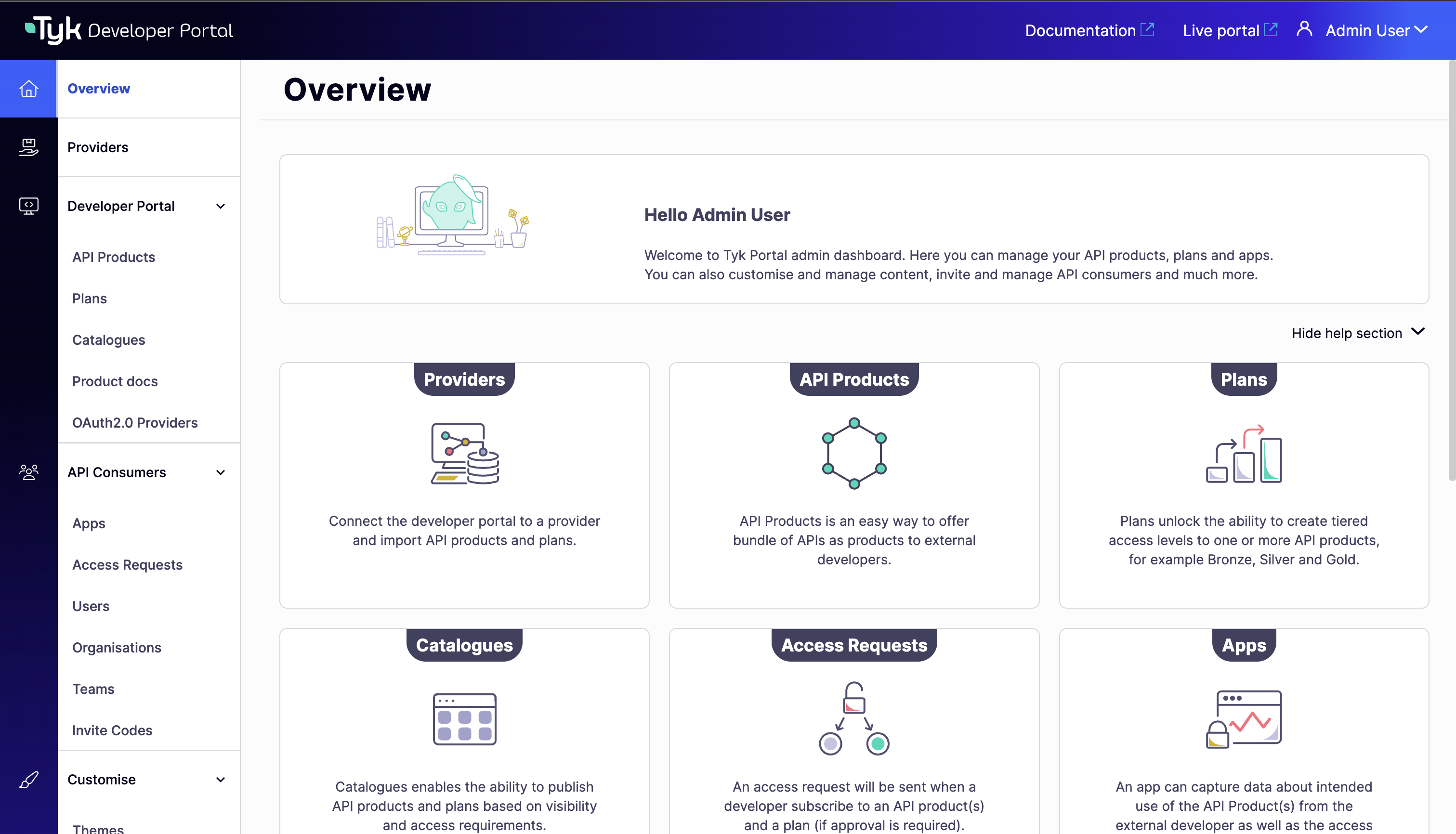
Verify Developer Portal Access:
- Open your browser and navigate to
http://localhost:3001 - Log in with the default credentials (portaladmin@tyk.io / specialpassword)
- You should see the
Overviewsection of the Developer Portal.
- Open your browser and navigate to
Exploring Your Pre-Configured Environment
When you run the Docker Compose command in the previous section, several interconnected components are deployed to create a complete Tyk API Management ecosystem. Let’s explore what’s installed and how these components work together. The following diagram illustrates the components of your Tyk Self-Managed installation and how they interact: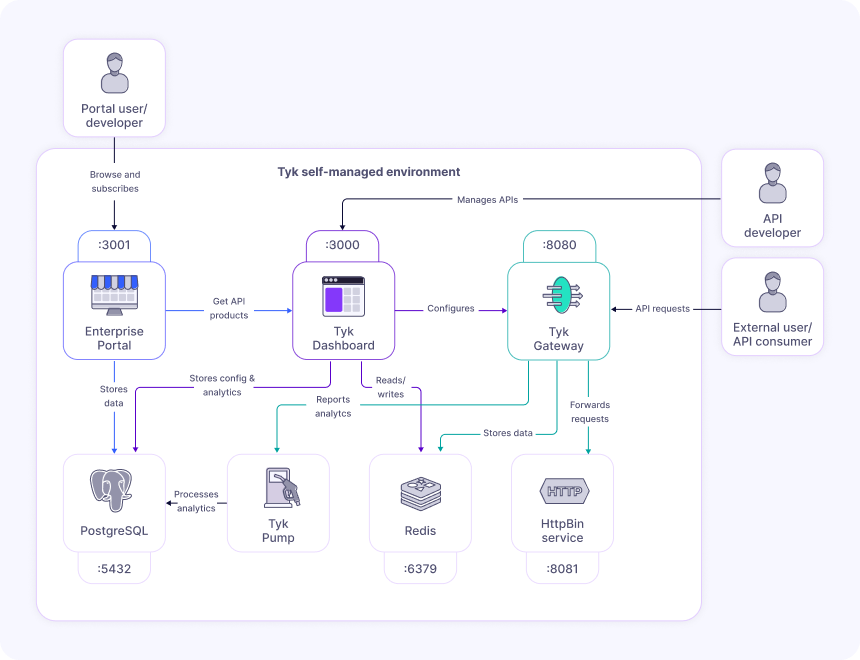
- Tyk Gateway (tyk-gateway): The core API Gateway that processes all API requests, applies policies, and enforces security. Exposed on port 8080.
- Tyk Dashboard (tyk-dashboard): The management interface for configuring APIs, policies, and viewing monitoring data. Exposed on port 3000.
- Developer Portal (tyk-ent-portal): A customizable portal for API consumers to discover, test, and subscribe to APIs. Exposed on port 3001.
- Redis (tyk-redis): Used for caching, session management, and real-time communication between components. Exposed on port 6379.
- PostgreSQL (tyk-postgres): Stores configuration data, user information, and analytics. Exposed on port 5432.
- Tyk Pump (tyk-pump): Processes and transfers analytics data from the Gateway to the database for reporting.
- HttpBin (httpbin): A sample API service that provides various endpoints for testing. Exposed on port 8081.
Dashboard Tour
The Tyk Dashboard is your central hub for managing APIs, monitoring performance, and configuring security settings.
Navigating the Tyk Dashboard
Dashboard is organized into a few key categories:- API Management: In API Management, you can access and edit all your APIs, create data graphs, and add webhooks.
- API Security: In API Security, you can manage keys, policies, and certificates to customize your security settings.
- User Management: In User Management, you can control permissions and access for users and user groups. You can also create profiles that help you manage third party identity providers for specific Tyk actions like signing into the portal or logging into the dashboard.
- Monitoring: In Monitoring, you can view activity reports, logs, and analytics related to your APIs.
- System Management: In System Management, you can affect OPA rules that define fine-grained access control for managing and enforcing permissions on various actions and resources in Tyk’s API management system.
- Classic Portal: In Classic Portal, you can affect permissions and configurations related to your developer portal. The Tyk Developer Portal is a platform that enables you to publish, manage, and promote your APIs to external developers.
Understanding the Pre-loaded APIs
Your trial environment comes with pre-configured sample APIs to help you explore Tyk’s capabilities: 1. httpbingo API Overview:- Purpose: A test API with various endpoints for exploring API management features
- Base URL:
http://localhost:8080/httpbingo - Authentication: API Key authentication (via Authorization header)
- Rate Limiting: Configured through policies (Sandbox and Production plans)
/get: Returns request data (headers, query parameters)/headers: Shows all request headers/ip: Returns the client’s IP address/xml: Demonstrates response transformation (XML to JSON)/status/{code}: Returns specified HTTP status code/mock: Returns a mock response generated by Tyk
- Purpose: Demonstrates JWT authentication with a real-world API providing Formula 1 racing data
-
Base URL:
http://localhost:8080/f1-api(proxies to https://f1api.dev/api/) -
Authentication: JWT HMAC authentication
JWT Authentication Details:
- Shared Secret:
topspecial256sharedbitlongsecret - JWT Generation: You can use jwt.io to generate valid tokens
- Header Format:
Authorization: Bearer <your_jwt_token>
- Shared Secret:
- Rate Limiting: 4 requests per 15 seconds (configured through policy)
/drivers: Information about F1 drivers/seasons: Data about F1 racing seasons/circuits: Details about F1 racing circuits/teams: Information about F1 teams
- In the Dashboard, go to the “APIs” section
- Click on either “httpbingo API” or “F1 API”
- Navigate through the tabs to see the various configuration options
- Pay special attention to the
Endpointstab to see how individual endpoints are configured
Developer Portal Preview
The Developer Portal provides a dedicated space for API consumers to discover, learn about, and subscribe to your APIs. It bridges the gap between API providers and consumers.
Exploring Available API Products and Catalogs
Login into the portal as an Admin user with credentials provided in the previous section to explore the resources created in the portal. The Developer Portal organizes APIs into a structured hierarchy: Products, Plans, and Catalogs:- Products: API offerings that developers can consume. In your trial, there’s a pre-configured product for the httpbingo API.
-
Plans: Subscription tiers with different access levels and rate limits. Your trial includes:
- Sandbox Plan: Limited rate (3 requests per 10 seconds) for testing and development
- Production Plan: Higher capacity (100 requests per 60 seconds) for production use
- Catalogs: Collections of products and plans that can be made available to different audiences. Your trial has a public catalog containing the httpbingo API product and both plans.
Understanding the developer experience
To experience the portal from a developer’s perspective:- You can access the live portal using the admin account. This is the public-facing interface for API consumers.
- From here the API consumer can:
- Browse the API catalog to see available products
- View the API documentation, which is automatically generated from the API definition
- Create apps and then Subscribe to a plan to get access credentials
- Test the API using the provided examples and your credentials
Core API Management Capabilities
In this section, we will explore the core API management capabilities of Tyk Self-Managed using the pre-configured APIs. We will explore how to your secure APIs, manage API traffic, and monitor your API usage. The following sections will guide you through the key features of Tyk API Management platform.API Security in Action
API security is an important aspect of API management. Tyk provides multiple authentication methods to secure your APIs and control access. In this section, we’ll explore the security features available in your trial environment.Exploring Authentication Methods
Tyk supports various authentication methods including Auth Token, JWT, OAuth 2.0, and more. In your trial environment, the httpbingo API is pre-configured with Auth Token authentication. Auth Tokens are the simplest form of authentication. They’re easy to implement and understand, making them perfect for your first exploration of Tyk.-
Create an API Key:
- In the Dashboard, navigate to the “Keys” section in the left menu
-
Click the “ADD KEY” button
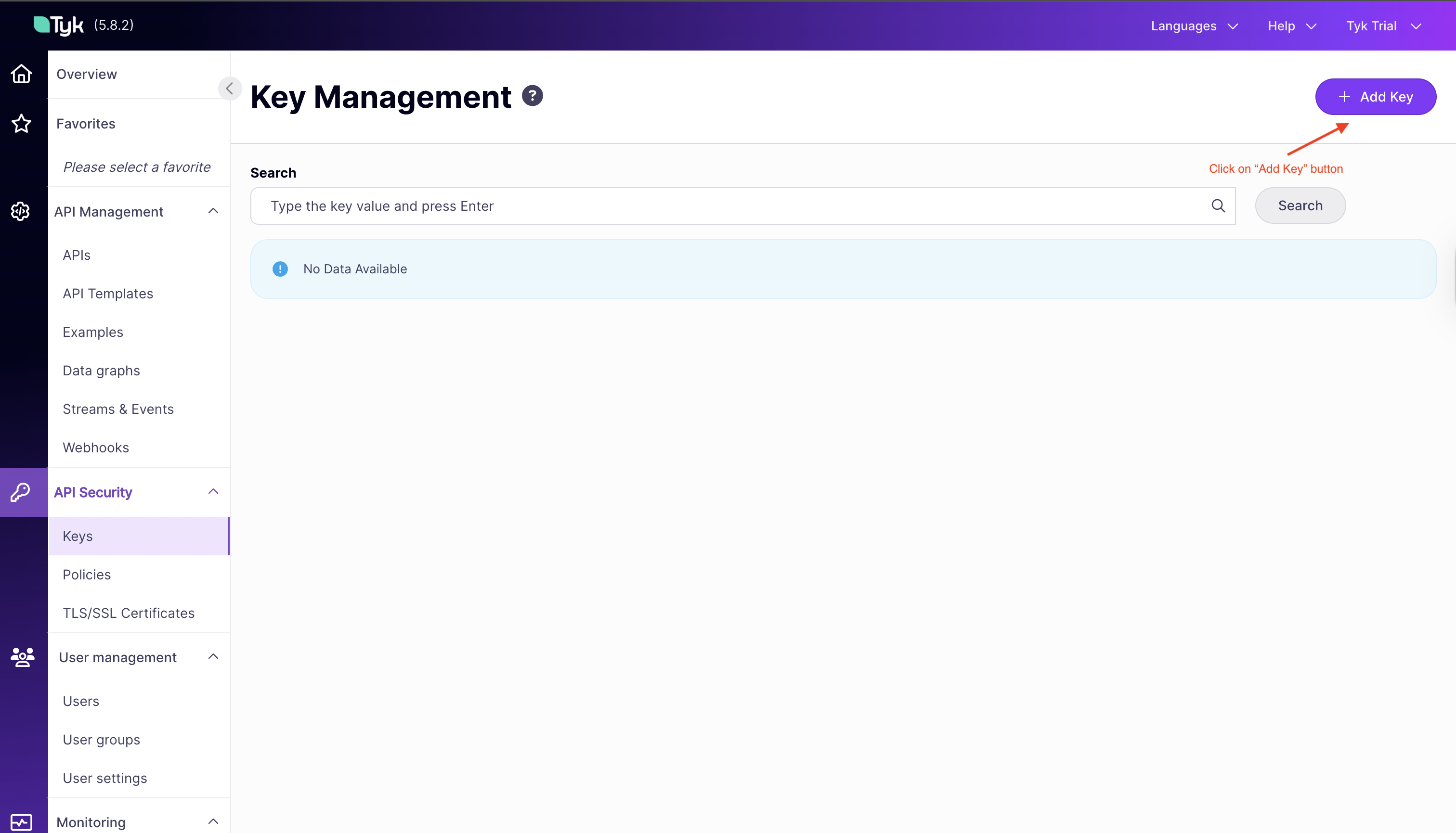
-
Under “Access Rights,” select the
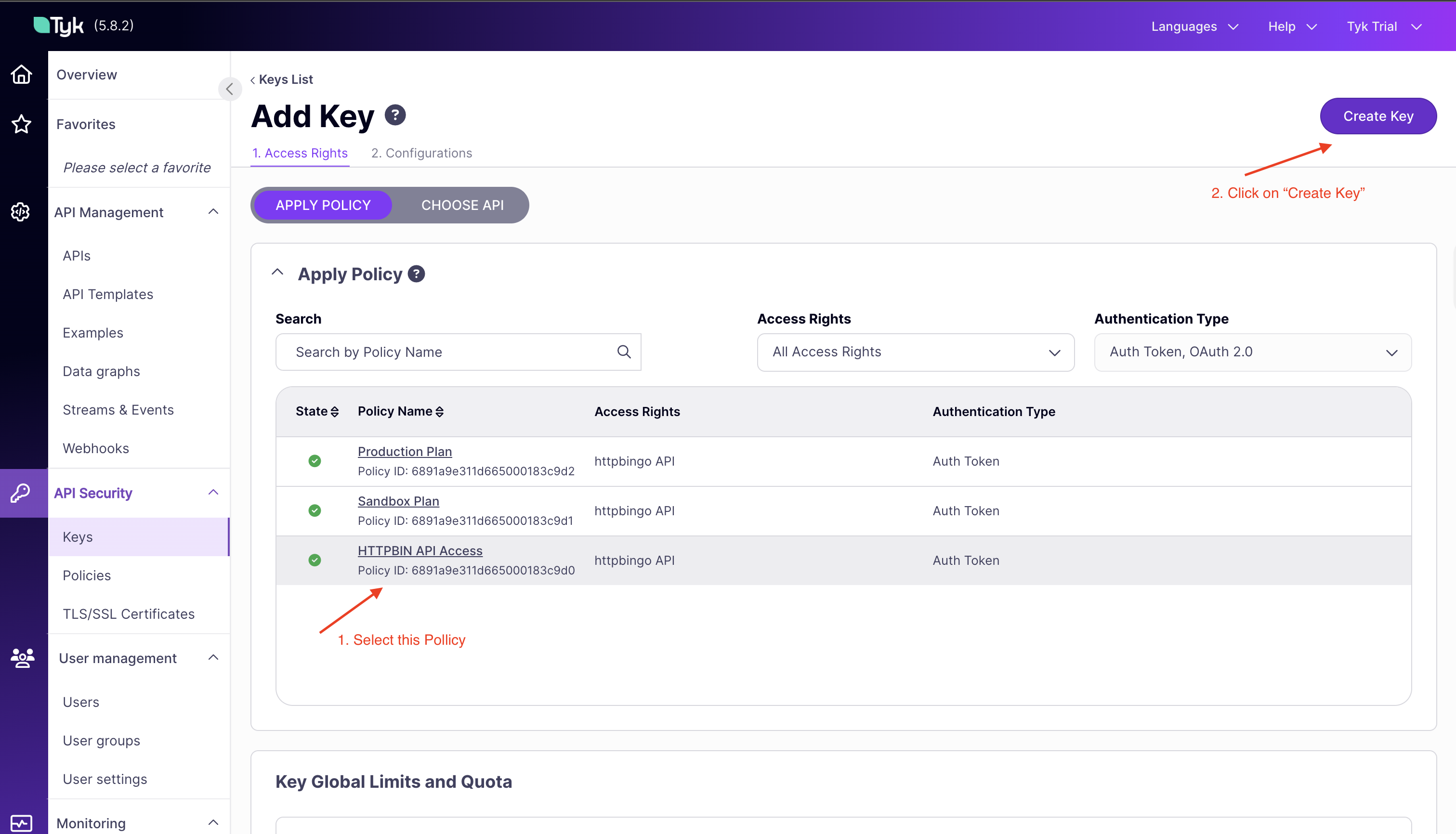
HTTPBIN API Accesspolicy -
Now under the “Configuration” tab, add an alias
httpbin -
Click “Create Key” to generate your API key
-
Copy the displayed API
key IDfor testingNote: This key will be used in the upcoming sections to authenticate requests to the httpbingo API.
-
Test API Access with Your Key:
- Open a terminal or API client like Postman
-
Make a request to the API including your key in the Authorization header:
-
You should receive a successful response with details about your request
-
Try Without Authentication:
-
Make the same request without the Authorization header:
-
You should receive an error, confirming that authentication is working
-
Make the same request without the Authorization header:
Rate Limiting and Quota Management
Rate limiting is a technique that allows you to control the rate at which clients can consume your APIs and is one of the fundamental aspects of managing traffic to your services. It serves as a safeguard against abuse, overloading, and denial-of-service attacks by limiting the rate at which an API can be accessed. In this section we will implement and test rate limiting in Tyk. Testing Rate Limiting:-
Create an API Key:
- In the Dashboard, navigate to the “Keys” section in the left menu
- Click the “ADD KEY” button
-
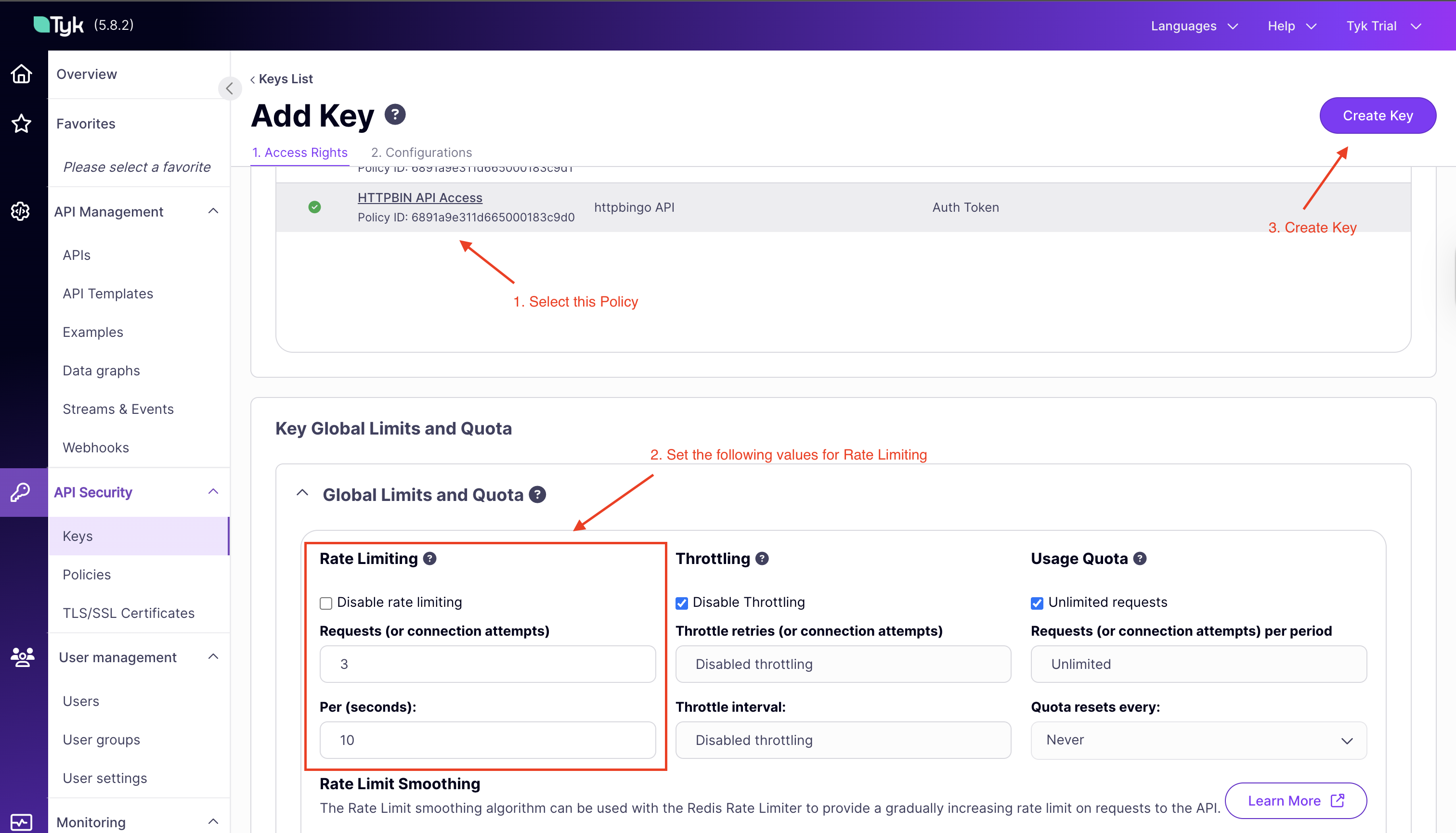
Under “Access Rights,” select the
HTTPBIN API Accesspolicy -
Under “Key Global Limits and Quota” set the following:
- Requests: 3 requests
- Per (seconds):: 10 seconds
-
Now under the “Configuration” tab, add an alias
httpbin rate limit -
Click “CREATE” to generate your API key
-
Copy the displayed API
key IDfor testing
-
Observe Rate Limiting in Action:
- Open a terminal and run multiple requests in quick succession:
- After the third request within 10 seconds, you should see a rate limit exceeded error
- Open a terminal and run multiple requests in quick succession:
-
Compare with a Higher Limit:
- Now update the
httpbin rate limitkey and set a value of100in the “requests” section of rate limiting. - Run the same test and observe that you can make more requests before hitting limits
- Now update the
-
Clean Up
-
After testing, you can delete the
httpbin rate limitAPI key from the Dashboard.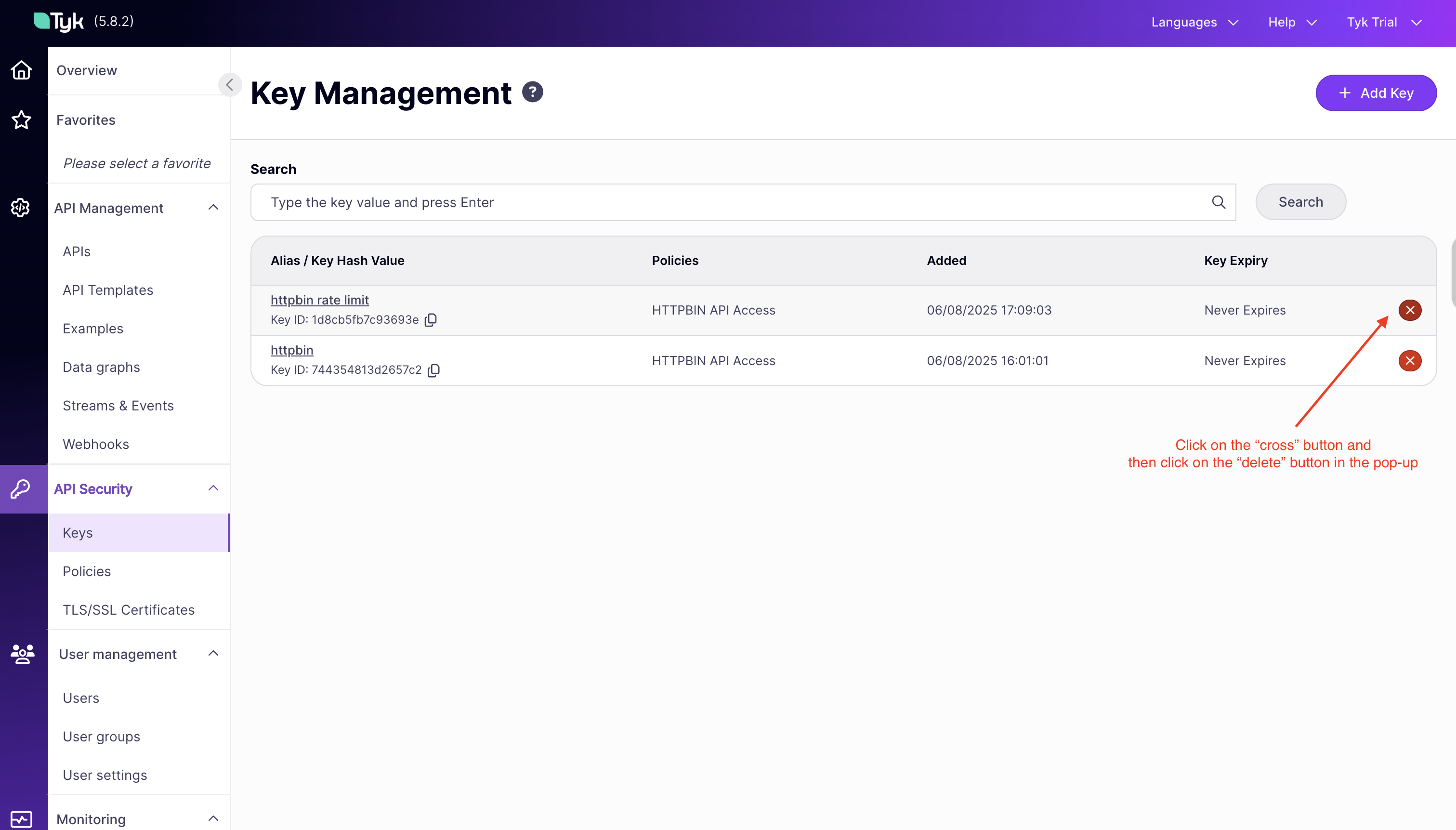
-
After testing, you can delete the
Traffic Control & Transformation
Tyk API Gateway can control and transform incoming API traffic. It provides various mechanisms to modify requests and responses, control traffic flow, and optimize performance. Let’s explore these capabilities in your trial environment.Testing Request/Response Transformations
Transformations allow you to modify API requests and responses without changing your backend services. This is useful for adapting legacy APIs, standardizing formats, or enhancing responses. The httpbingo API in your trial includes a pre-configured transformation on the/xml endpoint that converts XML responses to JSON format.
Testing the XML to JSON Transformation:
-
Access the XML Endpoint Directly:
- Before testing the transformation, you can access the XML endpoint (httpbin) directly to see the raw XML response:
- You should see an XML response from the backend service
- Before testing the transformation, you can access the XML endpoint (httpbin) directly to see the raw XML response:
-
Make a Request to the XML Endpoint:
- Using your API key from the previous section, make a request to the XML endpoint (on the Tyk Gateway):
- Notice that even though the backend returns XML, you receive a JSON response
- This transformation happens in the gateway, not in the backend service
- Using your API key from the previous section, make a request to the XML endpoint (on the Tyk Gateway):
-
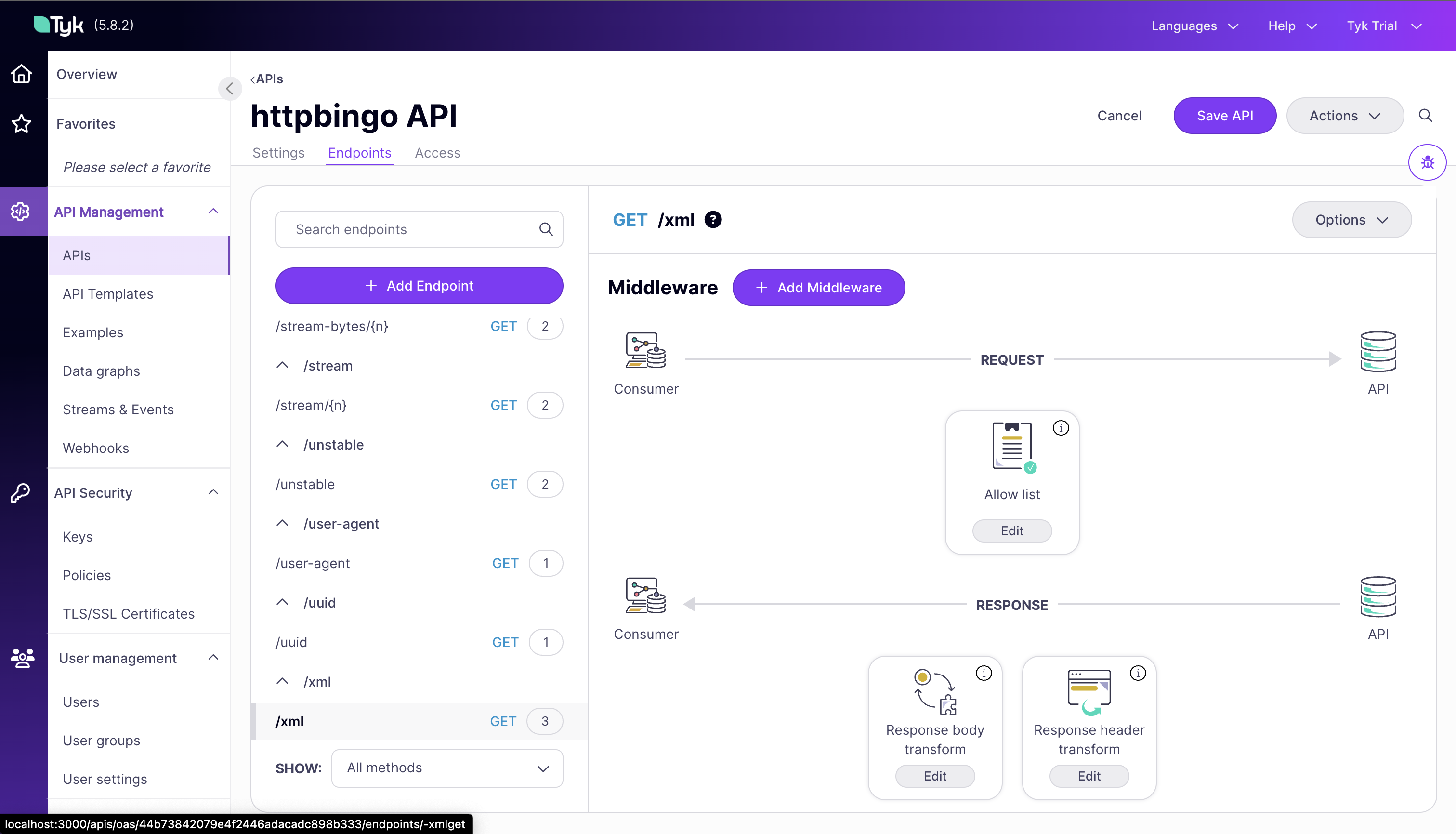
Examine the Transformation Configuration:
- In the Dashboard, go to the “APIs” section
- Click on the httpbingo API
- Navigate to the “Endpoints” tab
- Find the
/xmlpath and click on it - You’ll see the response transformation that converts XML to JSON
Exploring Caching Configurations
Caching improves API performance by storing responses and serving them without hitting your backend services for every request. This reduces latency and backend load. Understanding API Caching: The httpbingo API includes a caching example on the/get endpoint with a 10-second cache lifetime. This means that repeated requests within 10 seconds will receive the same cached response.
Testing Caching Behavior:
-
Make an Initial Request with a Unique Value:
- Using your API key, make a request to the endpoint with a unique Unique-Header:
- You’ll see the Unique-Header value in the response, for example:
- The httpbingo service echoes back the headers it receives, including your unique Unique-Header
- Using your API key, make a request to the endpoint with a unique Unique-Header:
-
Make an Immediate Second Request with a Different Header Value:
- Immediately make another request with a new unique header value:
- Notice that the Unique-Header value in the response is identical to the first request
- This confirms you’re receiving a cached response, not a new one from the backend
- Even though you sent a different header value in your request, you got back the same header value from the first request because the response was cached
- Immediately make another request with a new unique header value:
-
Wait and Test Again:
- Wait 11 seconds (just past the 10-second cache lifetime)
-
Make another request with a new unique value
- You should see a different Unique-Header value in the response, matching your new request
- This indicates the cache has expired and you’re getting a fresh response from the backend
Note: You can also check the
X-Tyk-Cached-Responseheader in the response to confirm whether the response was served from cache or not.
API Monitoring
Understanding how your APIs are performing is important for optimizing performance, planning capacity, and ensuring security. Tyk provides comprehensive monitoring capabilities to give you visibility into your API traffic.Generating Test Traffic
To explore Tyk’s monitoring capabilities, you’ll need to generate some API traffic that simulates real-world usage patterns and populates the monitoring dashboard. Creating Test Traffic:-
Using Command Line Tools:
- You can use simple bash loops to generate multiple requests:
- This sends 20 requests with a half-second delay between each
- You can use simple bash loops to generate multiple requests:
-
Generating Diverse Traffic:
-
Try accessing different endpoints to create a more realistic traffic pattern:
-
Include some errors by attempting to exceed rate limits or access without authentication
-
Try accessing different endpoints to create a more realistic traffic pattern:
Exploring Real-time Analytics
Once you’ve generated some traffic, you can explore Tyk’s analytics capabilities to gain insights into API usage. Accessing Monitoring Dashboard:-
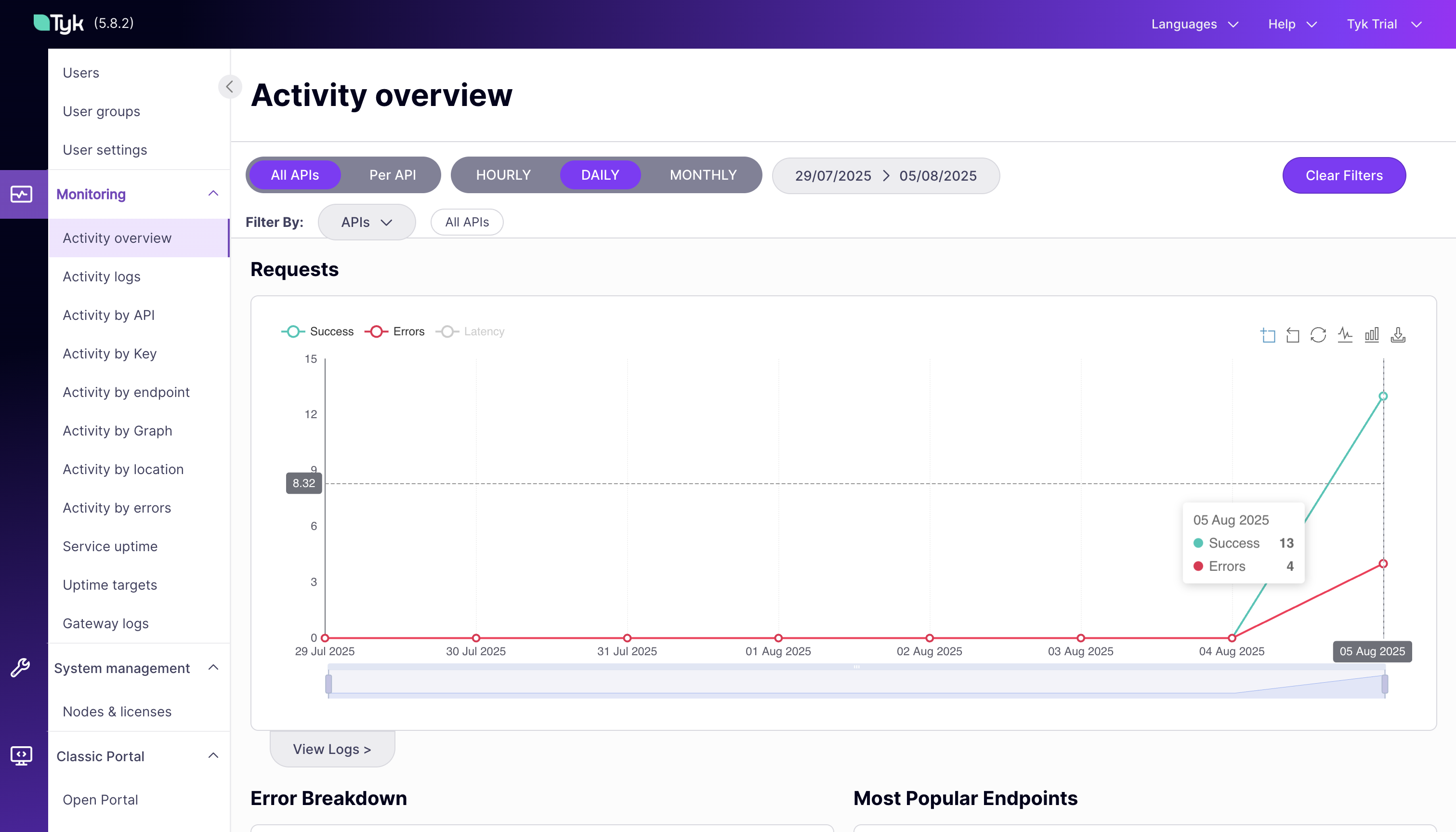
View the Main Dashboard:
- In the Tyk Dashboard, go to the Activity Overview section under “Monitoring”
- This provides an overview of API usage, errors, and performance metrics
-
The dashboard updates in near real-time as new requests are processed
-
Explore Key Metrics:
- Request Volume: See how many requests are being processed
- Error Rates: Monitor authentication failures and other errors
- Response Times: Track API performance and identify slow endpoints
-
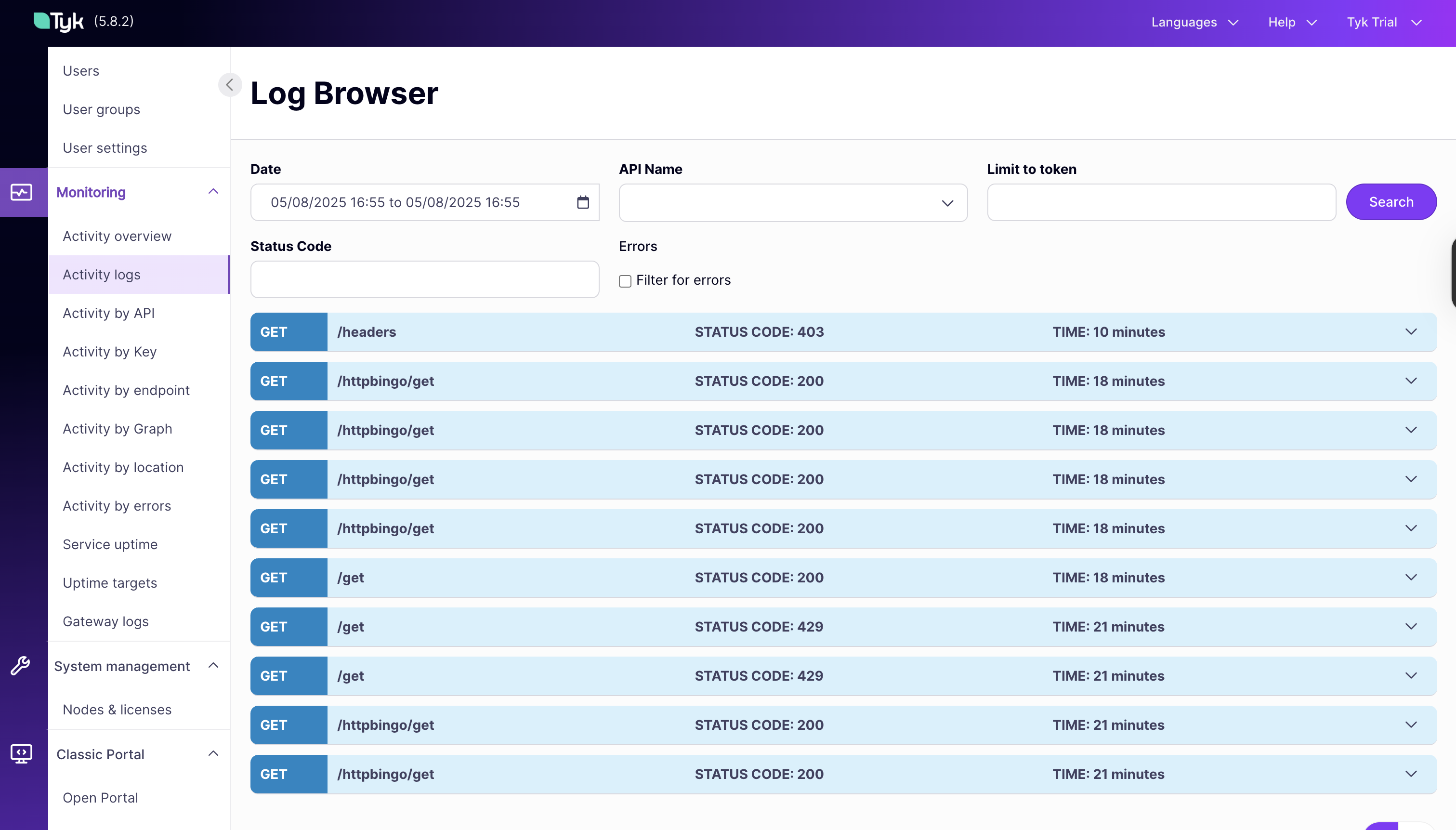
View Detailed Logs:
- In the Activity Logs section, you can view detailed logs of all API requests
- Filter by API, status code, or time range to focus on specific events
-
This is useful for troubleshooting and understanding user behavior
-
Multiple Analytics Views:
Tyk provides multiple views to analyze API traffic:
- By API: See metrics for individual APIs
- By Endpoint: Analyze performance and usage of specific endpoints
- By Key: Understand how different API keys are being used
- By Error: Identify common errors and their causes
- Which endpoints are most popular?
- Are there performance bottlenecks?
- Are users experiencing errors?
- How is usage changing over time?