As well as protecting their own APIs, organisations should also protect traffic going to external third-party APIs. Doing so prevents accidentally leaking OAuth tokens obtained for third-party APIs, such as those used to integrate with Salesforce, Google’s GSuite, Twitter and others.
The power of reverse gateways: leveraging third-party APIs
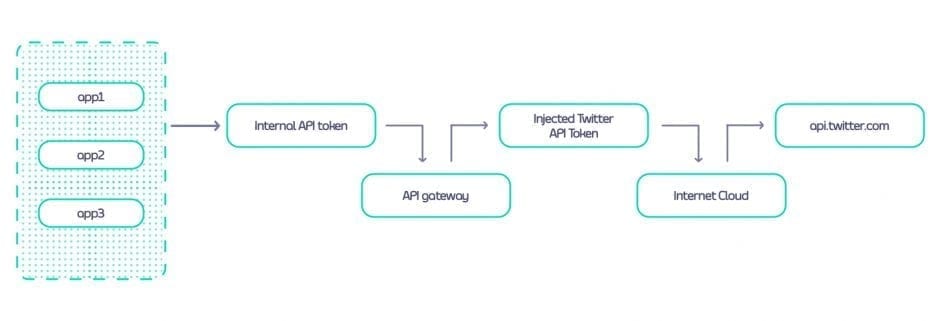
A reverse gateway acts as both a proxy to external third-party APIs and also as a token manager. Each managed third-party API is given a specific URL within the API manager, for example /twitter, and is routed through the API gateway rather than directly to the API.
Internally, developers are onboarded and assigned a token on their own API gateway, often called a sub-token, to work with the third-party API. The sub-token represents the application that will be making calls to the third-party API.
Whenever API requests are sent to this internal URL using the sub-token, the internal API management layer asserts the sub-token and then forwards the request, injecting the actual OAuth token for the service in the process.
Benefits and drawbacks of using reverse gateways
Using a reverse gateway offers several advantages in terms of security, access control and centralised management. These include:
- Restricting access to sensitive third-party APIs, with the reverse gateway ensuring that only authorised and property authenticated requests are forwarded
- Using access control and authorisation policies for fine-grained control
- Managing quotas centrally through API sub-tokens for better traffic and usage control
- Centralising procurement processes when multiple teams need to utilise a third-party API
- Determining API monthly usage for charge-back to a specific team
- Optimising performance through caching, load balancing and other performance enhancement functionality
These benefits are significant. However, there can also be drawbacks to using a reverse gateway. Adding a reverse gateway can bring increased complexity and performance overhead, for example. The reverse gateway could also become a bottleneck due to high traffic volume or inadequate resources – or even a single point of failure within the API communication flow.
Keeping secrets safe: best practices for managing API tokens
API token leaks are becoming more common. Many vendors, including GitHub, have implemented detection systems to avoid API tokens from being included in source code or configuration files stored in a code repository. Vault-based solutions are being used to manage API tokens, ensuring they are injected into an application at deploy time, or perhaps requiring applications to request the values at runtime via an internal secrets API.
Reverse gateways centralise third-party API tokens, substituting sub-tokens in their place. While proper token management is still required, the monitoring and management capabilities of an API gateway limit the impact to an application’s sub-token, introducing the possibility of reduced risk of exposure.
Understanding secrets management and its importance
API management solutions that incorporate a reverse gateway require an understanding of the role and importance of secrets management.
Secrets management is all about securely storing and managing sensitive data (tokens, keys, passwords and the like), with strict controls in place for access. These secrets grant access to valuable resources, so managing them securely is imperative; the potential for damage if they fall into the wrong hands is significant.
Practical tips for securely storing and managing API tokens
Effective secrets management includes putting practices in place and using the right API management tools to securely store and manage API tokens. Approaching this from a practical perspective means considering several elements: secure storage, access control, rotation and revocation and auditing and monitoring.
Secure storage means using encrypted and protected environments for API token management, while role-based access control can ensure access is locked down appropriately. Regular rotation, meanwhile, can minimise the potential for token compromises. You can also ensure that any suspected breaches are quickly dealt with by revoking existing tokens and generating new ones.
As with all areas of API management, implementing auditing and monitoring for token management makes it easier to track access, detect any suspicious activity and take action accordingly. Other practical steps you can take include avoiding hardcoding API tokens into source code or configuration files, encrypting them both at rest and in transit and enforcing best practices by educating your developers and administrators on all aspects of protecting tokens.
The cost of third-party APIs: strategies for effective budget management
While there are a variety of solutions to handle secrets management now, they fail to manage the relationship between third-party APIs and the application using them. Each time a new application needs to use a third-party API, the developers establish a relationship with the external organisation. In a large organisation, this might mean tens to hundreds of individual relationships that include contracts and subscription costs.
Reverse gateways enable this to be centrally managed to optimise both cost and time-to-production with these third-party APIs.
Common pitfalls to avoid when managing third-party API costs
Using an API management platform to implement a reverse gateway means that you can avoid some of the common pitfalls associated with managing third-party API costs.
One example of such a pitfall is a lack of visibility into the usage and costs associated with third-party APIs when no centralised API management service is in place. This can lead to spending inefficiencies and difficulties in optimising costs. This lack of visibility into usage can also lead to over-provisioning, with teams paying for more API resources or subscribing to higher tiers than they actually need.
Other pitfalls to avoid include poor contract negotiation with third-party API providers and inefficient resource allocation, including duplication of resources and costs. Again, these can be avoided with an API gateway and management solution that enables a centralised, more efficient approach.
Cost optimisation techniques for effective API management
If you’re looking to API management software to help optimise your costs, choose a solution with robust usage monitoring and analysis capabilities. The visibility that these enable can underpin a range of cost efficiencies.
Close teamwork with your procurement department also comes into play here. Working with procurement departments, a team can consolidate multiple subscriptions and ensure they are the right size, negotiate rates and adjust future contracts based on internal developer demand. As with any business solution, it also doesn’t hurt to evaluate alternatives from time to time, to ensure you are still getting value for money from your current services. This can support robust discussions at contract review and renewal time, at the very least!
Treating third-party APIs like your own: the importance of active management
It is important to consider third-party APIs like your own. They should be monitored, managed and reported on just like the APIs you produce for your organisation. Using an API gateway as a reverse gateway provides a consistent method of managing third-party APIs while optimising their usage.
Strategies for building strong relationships with third-party API providers
There are various steps you can take to build solid relationships with third-party API providers. You could, for example, consider dedicating a team to managing some or all of your third-party APIs. This team can use your API management reports to provide insights and negotiating tactics when possible.
Good communication and information sharing practices will also help, just as they will with any business relationship. Being clear, helpful and responsive is always a winner. Keeping in touch regularly can also help nurture your relationships with third-party API providers and means that, if an issue arises, communication channels are already open.
Best practices for monitoring and maintaining third-party APIs to ensure optimal performance
We’ll just share a few final tips, before leaving you to progress your third-party API management successfully. Choosing the right APIs, providers, API management gateway, API gateway microservices and so on is, of course, essential. As such, don’t rush into anything – do your research to ensure you’re building the right relationships from the outset.
Next, be sure to understand the process of API gateway integration with third-party APIs in full. Diving deep into third-party API documentation can help with this. Doing so will mean you can ensure optimal performance from the outset, including while setting up a reverse gateway, managing secrets securely and more.
Focus on monitoring from the outset too. You can set up performance baselines as part of this, to ensure you understand what normal behaviour looks like, along with alert thresholds in line with your expectations around optimal performance. Conduct regular performance testing in line with this.
Finally, remember that you’ll need to allow for third-party providers’ versioning and change management practices. Communication is critical here if you want to avoid last-minute surprises, disruption and breaking changes.
For more insight into managing third-party APIs, take a look at Tyk’s cloud native API management whitepaper, which you can download for free.
