Availability
| Component | Editions |
|---|---|
| Tyk Gateway | Community and Enterprise |
Introduction
Split Token Flow addresses a fundamental security concern with JWT tokens: when a JWT is stored on a client device (browser, mobile app, etc.), all of its contents can be easily decoded since JWTs are only base64-encoded, not encrypted. This means sensitive information in the payload is potentially exposed. The JWT consists of three parts: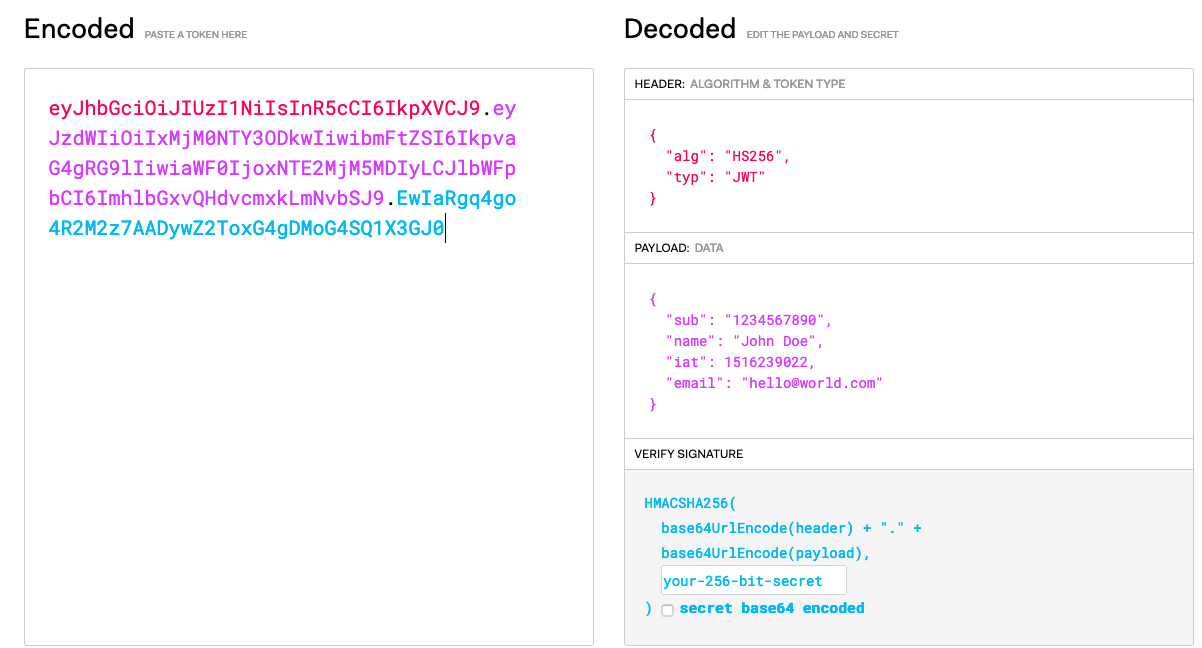
- Header:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9 - Payload:
eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyLCJlbWFpbCI6ImhlbGxvQHdvcmxkLmNvbSJ9 - Signature:
EwIaRgq4go4R2M2z7AADywZ2ToxG4gDMoG4SQ1X3GJ0
- Separating the JWT into its three component parts: header, payload, and signature
- Storing only the signature on the client side (which by itself is meaningless)
- Keeping the header and payload securely on the server side (in Tyk)
- Reconstructing the complete JWT when needed for authentication
When to Use Split Token Flow
Consider using Split Token Flow when:- Your JWT payload contains sensitive information that shouldn’t be exposed to clients
- You want to prevent token inspection by malicious actors
- You need the flexibility of JWT while maintaining higher security
- You’re implementing systems that must meet strict security compliance requirements
How Split Token Flow Works
Here’s how the process works with Tyk Gateway:-
Token Issuance:
- A
/tokenendpoint is configured on Tyk from which the client should request the access token - Tyk requests an access token from an authorization server (e.g., Keycloak) on behalf of the client
- The authorization server returns a complete JWT
- Tyk intercepts this response through a Virtual Endpoint
- Tyk splits the JWT into its components and stores the header and payload in its Redis database
- Only the signature portion is returned to the client as an “opaque” token
- A
-
Token Usage:
- The client makes API requests using only the signature as their access token
- Tyk receives the request and looks up the stored header and payload using the signature
- Tyk reconstructs the complete JWT and validates it
- If valid, Tyk forwards the request to the upstream API with the full JWT
-
Security Benefits:
- The client never possesses the complete JWT, only a meaningless signature
- Token contents cannot be inspected by client-side code or malicious actors
- Token validation still occurs using standard JWT verification
Implementing Split Token Flow
-
Create a Virtual Endpoint for Token Issuance
First, create a virtual endpoint in Tyk that will:
- Receive authentication requests from clients
- Forward these requests to your authorization server
- Split the returned JWT
- Store the header and payload in Tyk’s storage
- Return only the signature to the client
- Here’s a simplified implementation:
Note that this example includes some level of abstraction for clarity and so is not a full implementation. -
Configure Custom Pre-Auth Plugin
Next, create a custom pre-auth plugin that reconstructs the JWT before it reaches the standard Tyk JWT Auth middleware:
-
Test the Implementation
To test your Split Token Flow:
Request a token from your Tyk virtual endpoint:
You’ll receive a response with only the signature as the access token, for example:Use this token to access your JWT Auth protected API where you have configured the custom pre-auth plugin and JWT Auth: