Introduction
Hash-Based Message Authentication Code (HMAC) Signing is an access token method that adds another level of security by forcing the requesting client to also send along a signature that identifies the request temporally to ensure that the request is from the requesting user, using a secret key that is never broadcast over the wire. Tyk currently implements the latest draft of the HMAC Request Signing standard. HMAC Signing is a good way to secure an API if message reliability is paramount, it goes without saying that all requests should go via TLS/SSL to ensure that MITM attacks can be minimized. There are many ways of managing HMAC, and because of the additional encryption processing overhead requests will be marginally slower than more standard access methods. An HMAC signature is essentially some additional data sent along with a request to identify the end-user using a hashed value, in our case we encode the ‘date’ header of a request, the algorithm would look like:Authorization header, and uses set, stripped comma-delimited fields to identify the user, from the draft proposal:
hmac.allowedAlgorithms (Tyk Classic: hmac_allowed_algorithms) field in your API definition, like this: "hmac_allowed_algorithms": ["hmac-sha256", "hmac-sha512"].
The date format for an encoded string is:
How Tyk validates the signature of incoming requests
When an HMAC-signed request comes into Tyk, the key is extracted from theAuthorization header, and retrieved from Redis. If a key exists then Tyk will generate its own signature based on the request’s “date” header, if this generated signature matches the signature in the Authorization header the request is passed.
Supported headers
Tyk API Gateway supports full header signing through the use of theheaders HMAC signature field. This includes the request method and path using the(request-target) value. For body signature verification, HTTP Digest headers should be included in the request and in the header field value.
All headers should be in lowercase.
Date header not allowed for legacy .Net
Older versions of some programming frameworks do not allow the Date header to be set, which can causes problems with implementing HMAC, therefore, if Tyk detects ax-aux-date header, it will use this to replace the Date header.
Clock Skew
Tyk also implements the recommended clock-skew from the specification to prevent against replay attacks, a minimum lag of 300ms is allowed on either side of the date stamp, any more or less and the request will be rejected. This means that requesting machines need to be synchronised with NTP if possible. You can edit the length of the clock skew in the API Definition by setting thehmac.allowedClockSkew (Tyk Classic: hmac_allowed_clock_skew) value. This value will default to 0, which deactivates clock skew checks.
Setting up HMAC using the Dashboard
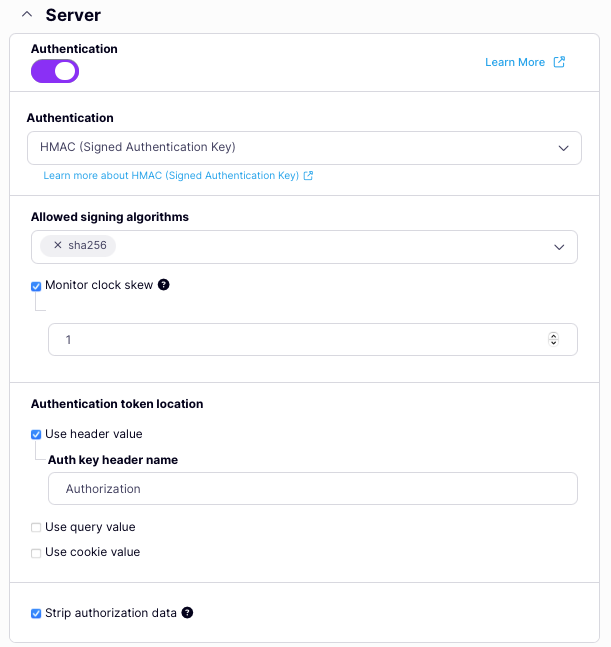
To enable the use of HMAC Signing in your API from the Dashboard:- Scroll to the Authentication options
- Select HMAC (Signed Authentication Key) from the drop-down list
- Configure your HMAC Request Signing settings.
- Select Strip Authorization Data to strip any authorization data from your API requests.
- Select the location of the signature in the request.
Configuring your API to use HMAC Request Signing
HMAC request signing is configured within the Tyk Vendor Extension by adding thehmac object within the server.authentication section and enabling authentication.
You must indicate where Tyk should look for the request signature (header, query or cookie) and which algorithm will be used to encrypt the secret to create the signature. You can also optionally configure a limit for the allowedClockSkew between the timestamp in the signature and the current time as measured by Tyk.
authentication.stripAuthorizationData field (Tyk Classic: strip_auth_data).
Using Tyk Classic
As noted in the Tyk Classic API documentation, you can select HMAC Request Signing using theenable_signature_checking option.
Registering an HMAC user with Tyk
When using HMAC request signing, you need to provide Tyk with sufficient information to verify the client’s identity from the signature in the request. You do this by creating and registering HMAC user session objects with Tyk. When these are created, a matching HMAC secret is also generated, which must be used by the client when signing their requests. The way that this is implemented is through the creation of a key that grants access to the API (as you would for an API protected by auth token) and indicating that the key is to be used for HMAC signed requests by settinghmac_enabled to true. Tyk will return the HMAC secret in the response confirming creation of the key.
When calling the API, the client would never use the key itself as a token, instead they must sign requests using the provided secret.