Introduction
Modern web applications require secure communication to protect sensitive data from eavesdropping and tampering. Transport Layer Security (TLS) is the foundation of secure internet communication, and Tyk provides comprehensive TLS support for both client-facing APIs and backend service communication.Understanding Secure Communication
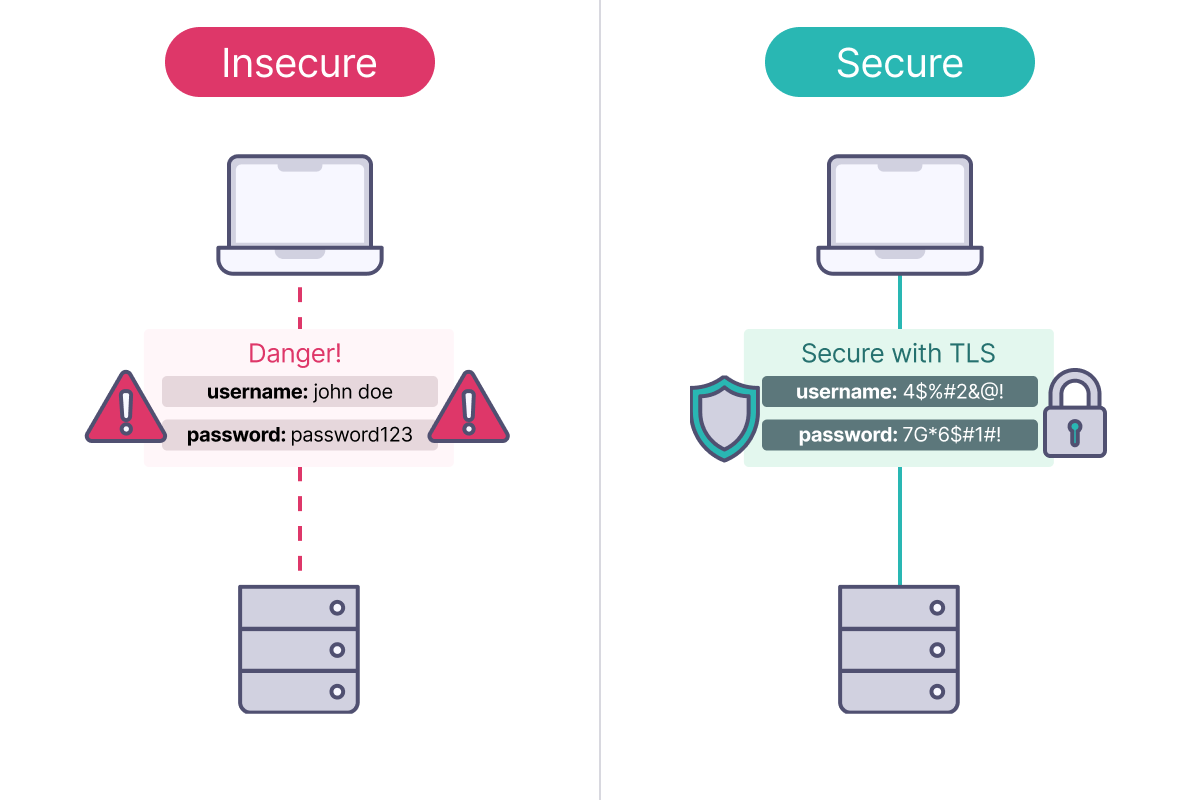
The Problem: Insecure Communication
Without encryption, network communication faces several risks:- Eavesdropping: Anyone can read your data as it travels across networks
- Tampering: Attackers can modify data in transit without detection
- Impersonation: Malicious actors can pretend to be legitimate servers or clients
The Solution: Transport Layer Security (TLS)
TLS (Transport Layer Security) is a cryptographic protocol that solves these problems by providing:- Confidentiality: Encrypts data so only intended recipients can read it
- Integrity: Ensures data hasn’t been modified during transmission
- Authentication: Verifies the identity of communicating parties
TLS or SSL
SSL (Secure Sockets Layer) is the older version of TLS, which is now the standard for secure web communication. TLS uses stronger encryption and better key management. All SSL and earlier TLS versions (1.0, 1.1) are deprecated. Today, “SSL” usually refers to TLS, especially versions 1.2 and 1.3, which are secure.Fundamentals of Public Key Cryptography
Transport Layer Security uses public key cryptography. This is an asymmetric method in which each communicating party possesses a unique key pair: a private key for decryption and a public key for encryption, enabling secure communication.Encryption Keys
A key is a specific value used within a cryptographic algorithm to encrypt data into an unreadable format and decrypt it back to its original state with the correct key using a defined algorithm. With public key cryptography, there are two different keys:- the private key is held by the originator of the message and is kept private
- the public key is shared with the recipient of the message
Digital Certificates
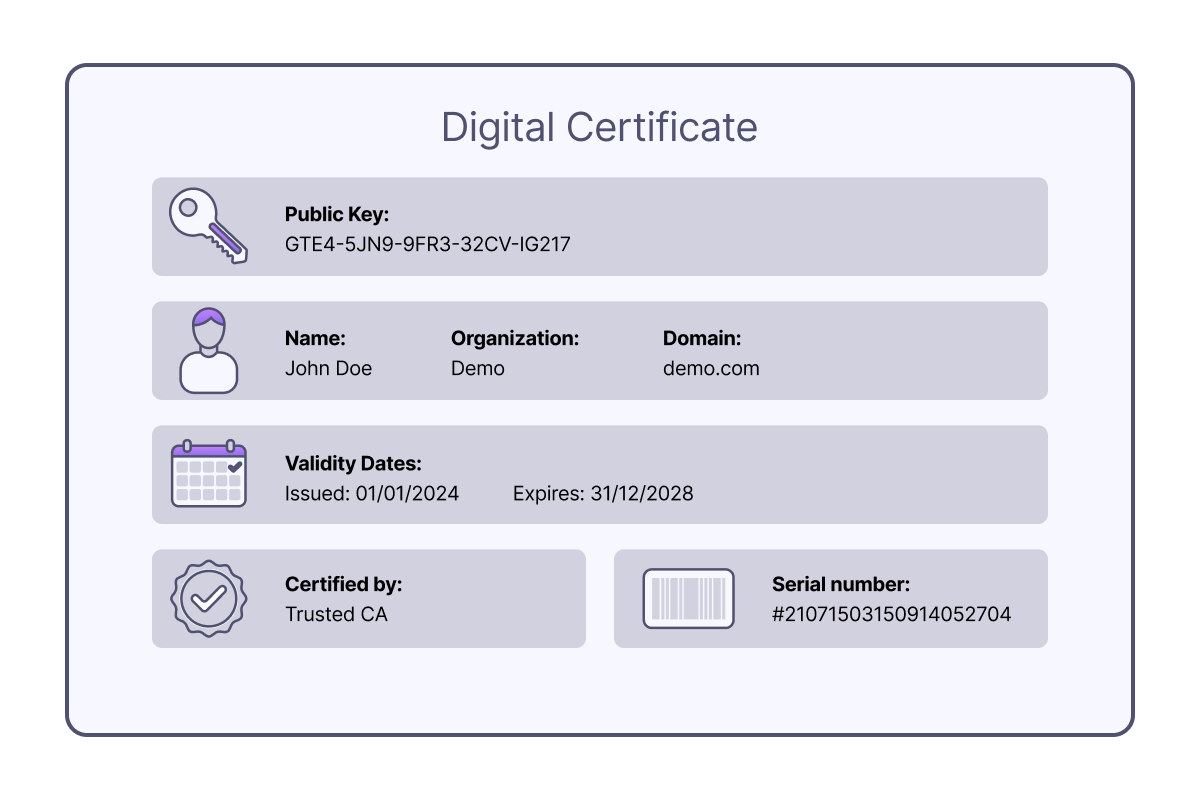
Various signature algorithms are available for signing certificates. The chosen algorithm can affect performance, as some are easier for Tyk to verify than others. Generally, elliptic curve algorithms offer better performance on average, but actual results may vary depending on CPU architecture. It is recommended to test and determine the most suitable balance between security and performance for specific needs.
Certificate Authorities (CAs)
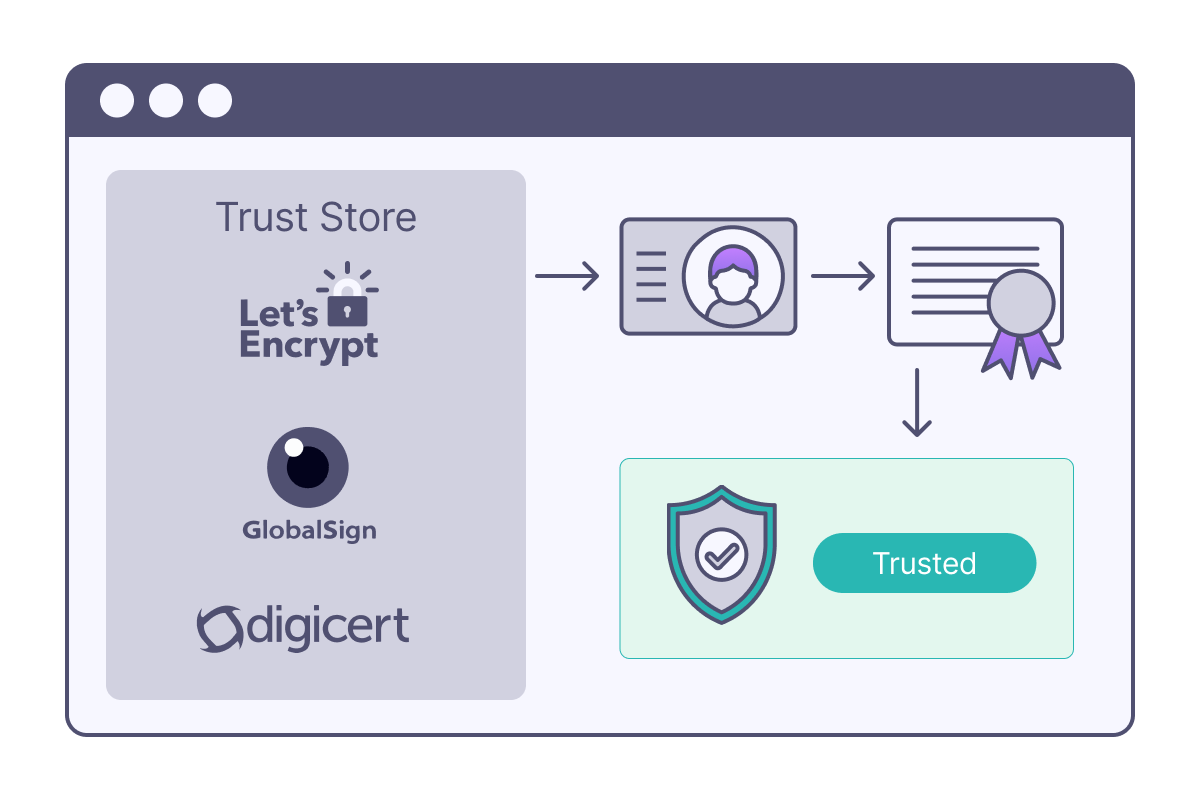
- Let’s Encrypt: Free, automated certificates
- DigiCert: Enterprise-grade certificates
- GlobalSign: International CA with global presence
- Internal CAs: Organizations can run their own CAs for internal use (self-signed certificates)
Certificate Chains and Trust
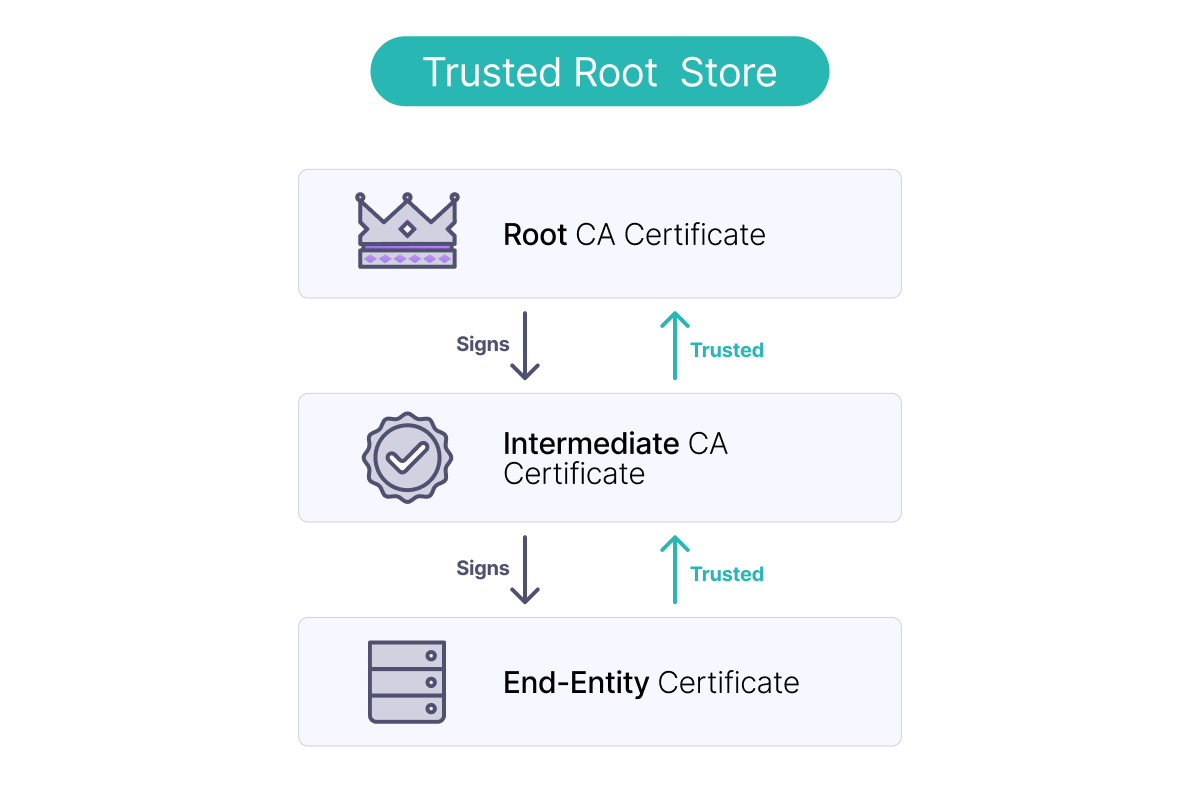
Fundamentals of Transport Layer Security
Standard TLS: Server Authentication
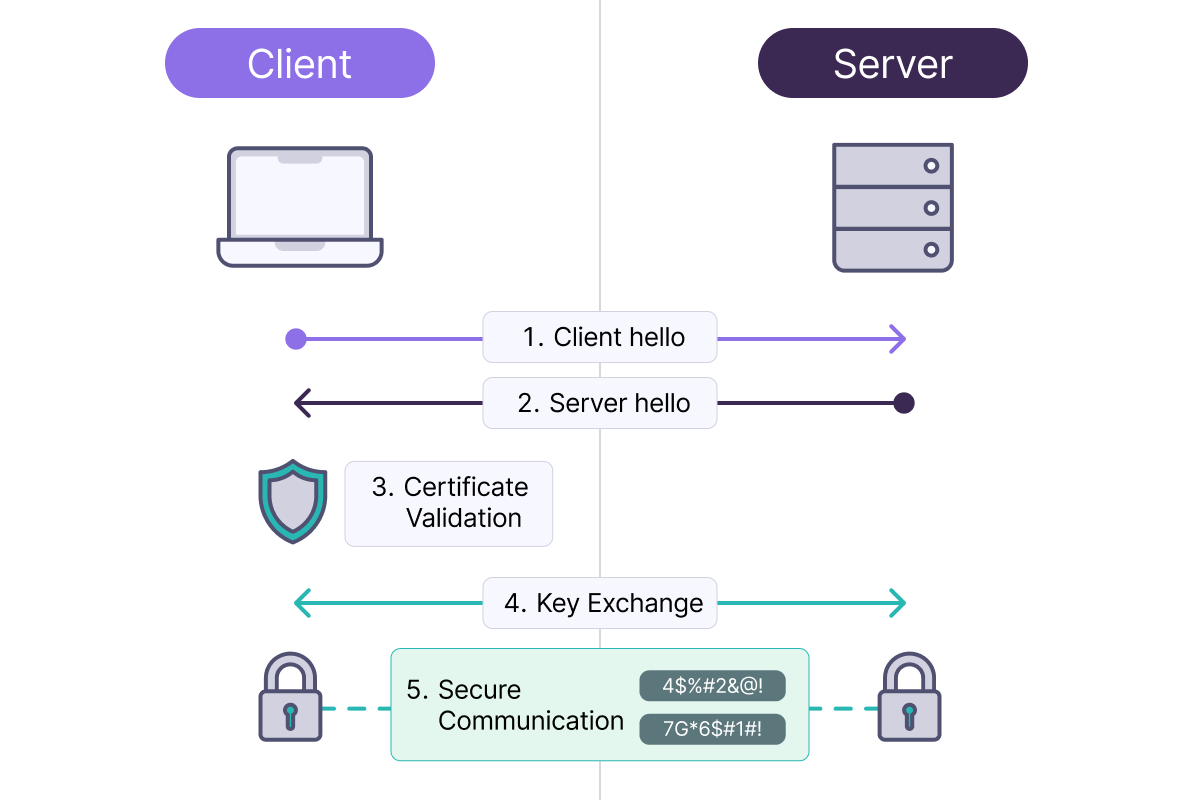
Mutual TLS (mTLS): Two-Way Authentication
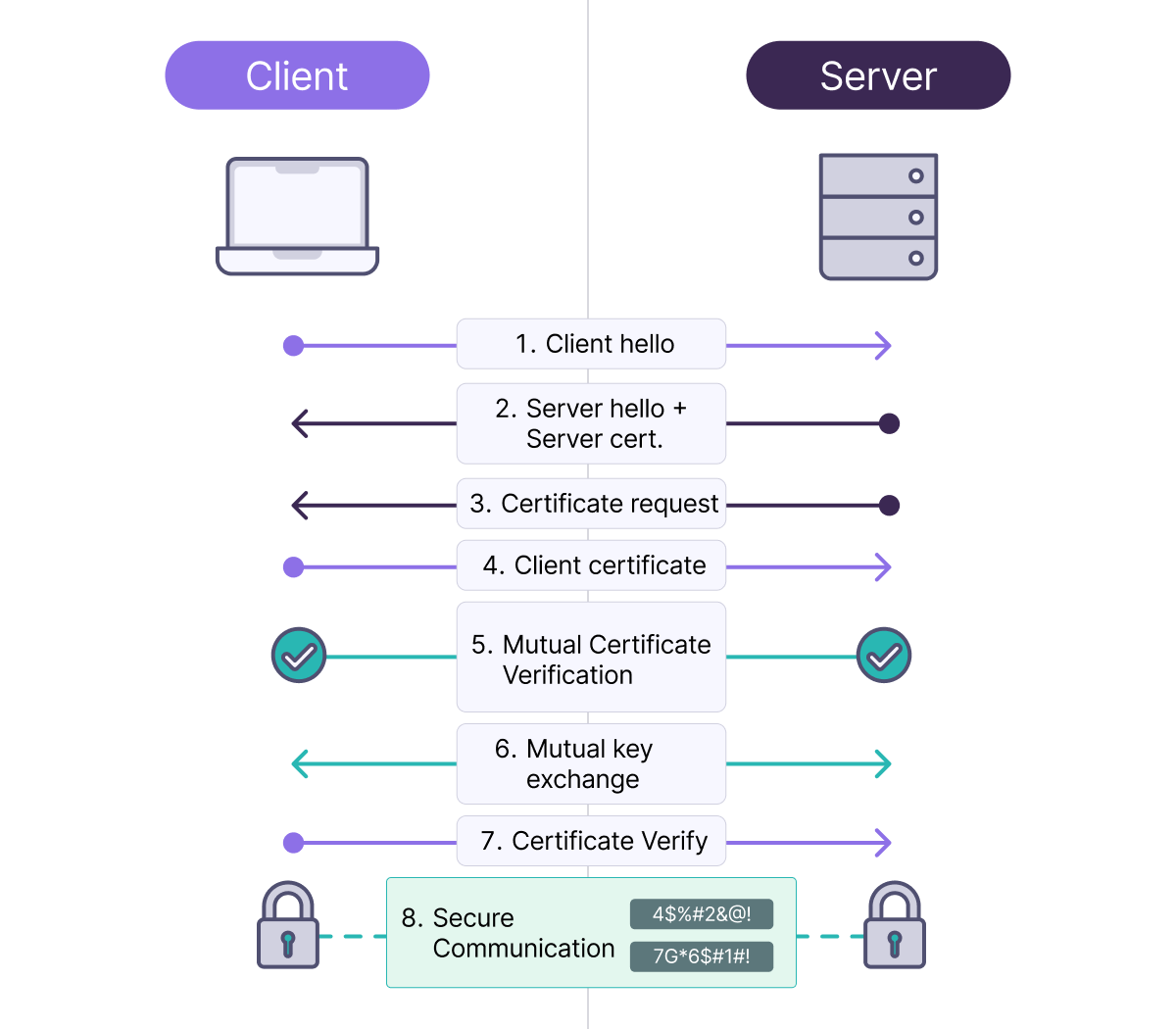
- The server knows that the client is who they claim to be
- The client knows that the server is legitimate
- Both parties are cryptographically verified
Certificate Management
The Tyk Dashboard offers a Certificate Management API to register certificates for Gateway use with unique IDs for reference in configurations. For Tyk OSS users, the Tyk Gateway also exposes a basic Certificate Management API. A legacy approach allows using local file-system certificates as long as the Gateway can read the files anywhere in the system. When using the file-system, references to certificates are made using the path to the certificate’s.pem file.
Tyk Certificate Store
The Tyk Certificate Store centralizes certificates within Tyk’s data layer for use by multiple APIs, managed through the Dashboard API. In licensed Tyk installations, the Dashboard manages certificates, storing them in the Control Plane Redis and syncing them to the Data Plane Redis for the Gateway. In a Tyk OSS installation, there is no Dashboard/Control Plane. The Gateway manages the certificates directly, storing them in Redis.Certificate ID and Redis key
When a certificate is added, it gets a unique certificate ID, used to refer to it, such as when linking to an API. This ID combines theorgID and the certificate’s SHA-256 hash. In Redis, it is stored under cert-raw- plus the certificate ID.
This means that certificate IDs are predictable and can be calculated if you know the Organisation ID and have the certificate file. You can generate the SHA256 fingerprint using the following command:
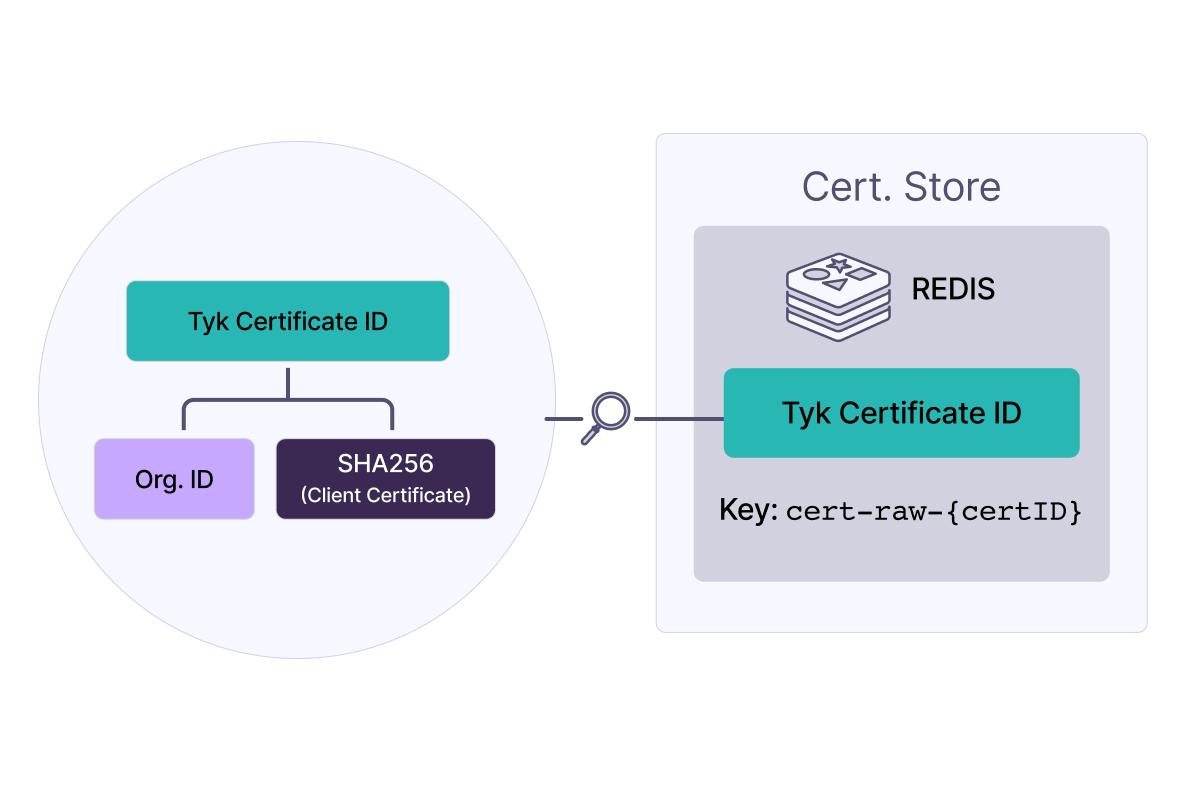
Notice that you can’t retrieve the raw certificate from just the certificate ID and that this is a unique identifier.
Certificate data
The data stored against a certificateID is the PEM-encoded certificate chain data, comprising:- The Certificate(s):
- The primary X.509 certificate
- Any intermediate certificates in the chain
- Encrypted Private Key (if provided):
- If a private key was included with the certificate, it’s encrypted using AES-256
- The encryption uses the
private_certificate_encoding_secretfrom your Tyk configuration - The encrypted key is appended to the certificate chain with the header
ENCRYPTED PRIVATE KEY
Encryption of the Private Key
If the private key was provided in the imported PEM file, it will be encrypted using the AES-256 algorithm with an encryption key that you must set in the Gateway, Dashboard, and MDCB configurations (if used).- Gateway:
TYK_GW_SECURITY_PRIVATECERTIFICATEENCODINGSECRET - Dashboard:
TYK_DB_SECURITY_PRIVATECERTIFICATEENCODINGSECRET - MDCB:
TYK_MDCB_SECURITY_PRIVATECERTIFICATEENCODINGSECRET
It is important to keep the shared secret secure.
Standalone Public Key
Stand-alone public keys (not contained within a certificate) are sometimes used for upstream certificate pinning or JWT verification. If only the public key were provided, rather than the certificate containing that key, then just the PEM-encoded public key would be stored against the certificateID, for example:Monitoring Certificate Expiry
X.509 certificates have a validity period with both start and end timestamps outside which they will not be accepted in the TLS handshake. Tyk Gateway checks the validity of each certificate when it is used in an API request and will generate both an error log and a Gateway event if an attempt is made to use an expired certificate (after itsnotAfter timestamp).
An optional warning can be configured to generate a log and Gateway event if a certificate is used within a configurable window before the notAfter timestamp.
CertificateExpired: an expired certificate has been used in a requestCertificateExpiringSoon: a certificate has been used within the expiry threshold window
security.certificate_expiry_monitor section of the Gateway configuration (or equivalent environment variables):
| Field | Effect |
|---|---|
warning_threshold_days | The number of days before certificate expiry that the Gateway will start generating CertificateExpiringSoon events when the certificate is used |
check_cooldown_seconds | A cool-off period after checking a certificate’s expiry before another check is made, to avoid unnecessary log generation when an API is called repeatedly |
event_cooldown_seconds | A cool-off period after generating CertificateExpired or CertificateExpiringSoon for a certificate, to avoid unnecessary event generation when an API is called repeatedly |
Tyk Certificate Store API
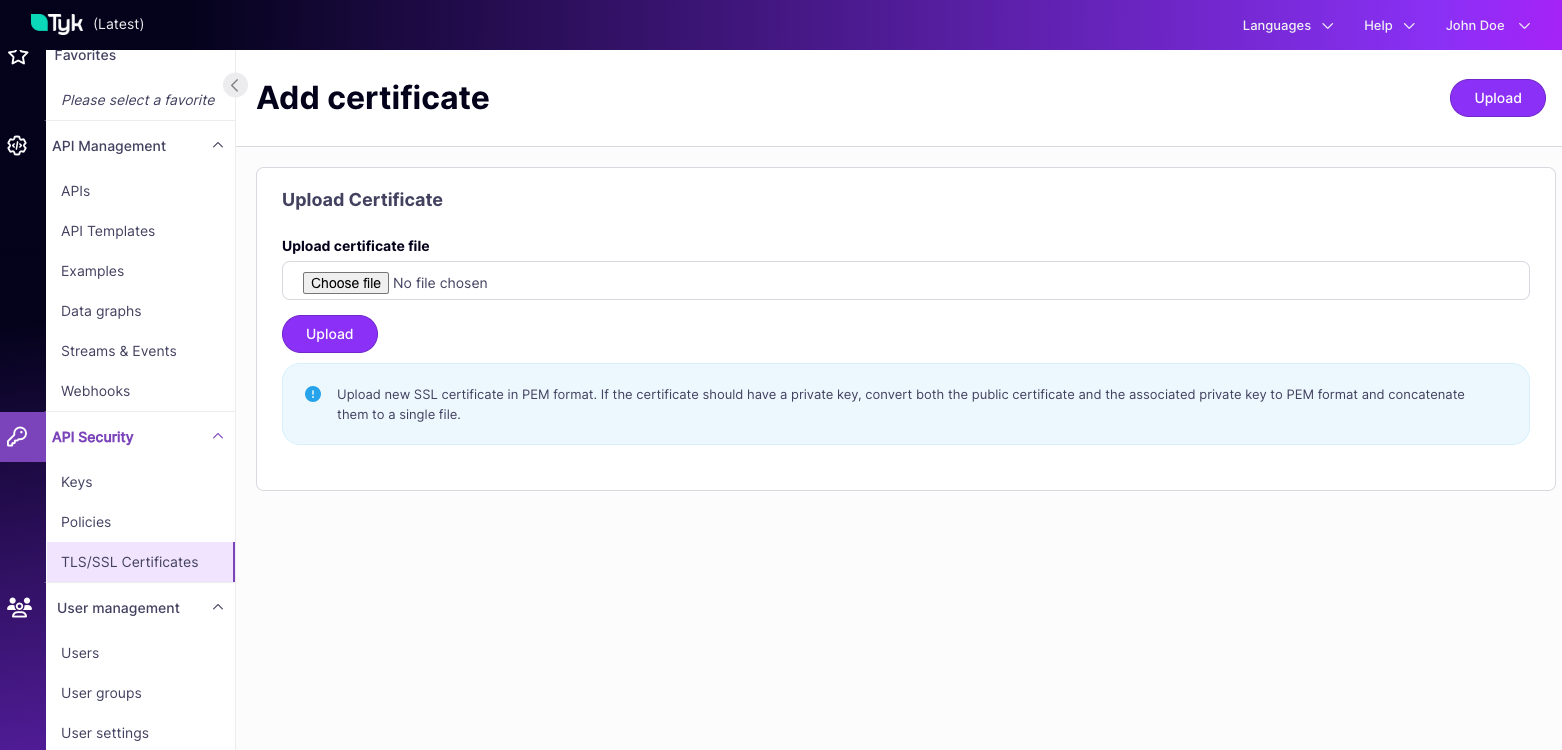
The Tyk Dashboard API exposes endpoints to manage the Tyk Certificate Store allowing you to:- Register a new certificate with the store
- provide either a PEM-encoded certificate (optionally concatenated with PEM-encoded private key) or a PEM-encoded public key
- This returns the assigned certificate ID
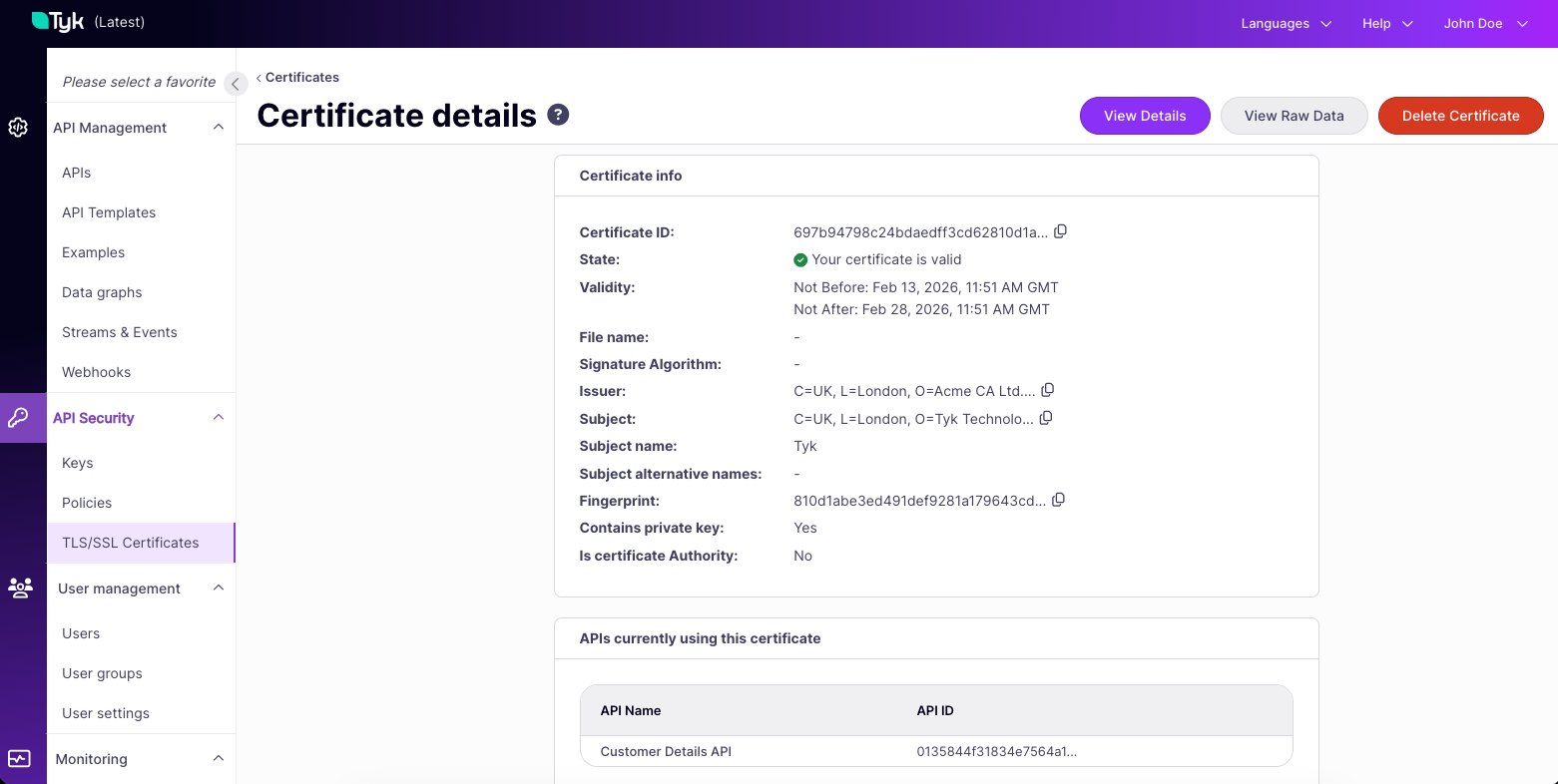
- Retrieve details of a specific entry in the store
- provide a certificate ID
- This returns metadata including the certificate issuer, whether there is a private key and the certificate fingerprint (SHA256 hash of the certificate)
- Retrieve a list of all certificates in the store
- Delete a certificate from the store
- Retrieve a list of APIs that are using a certificate
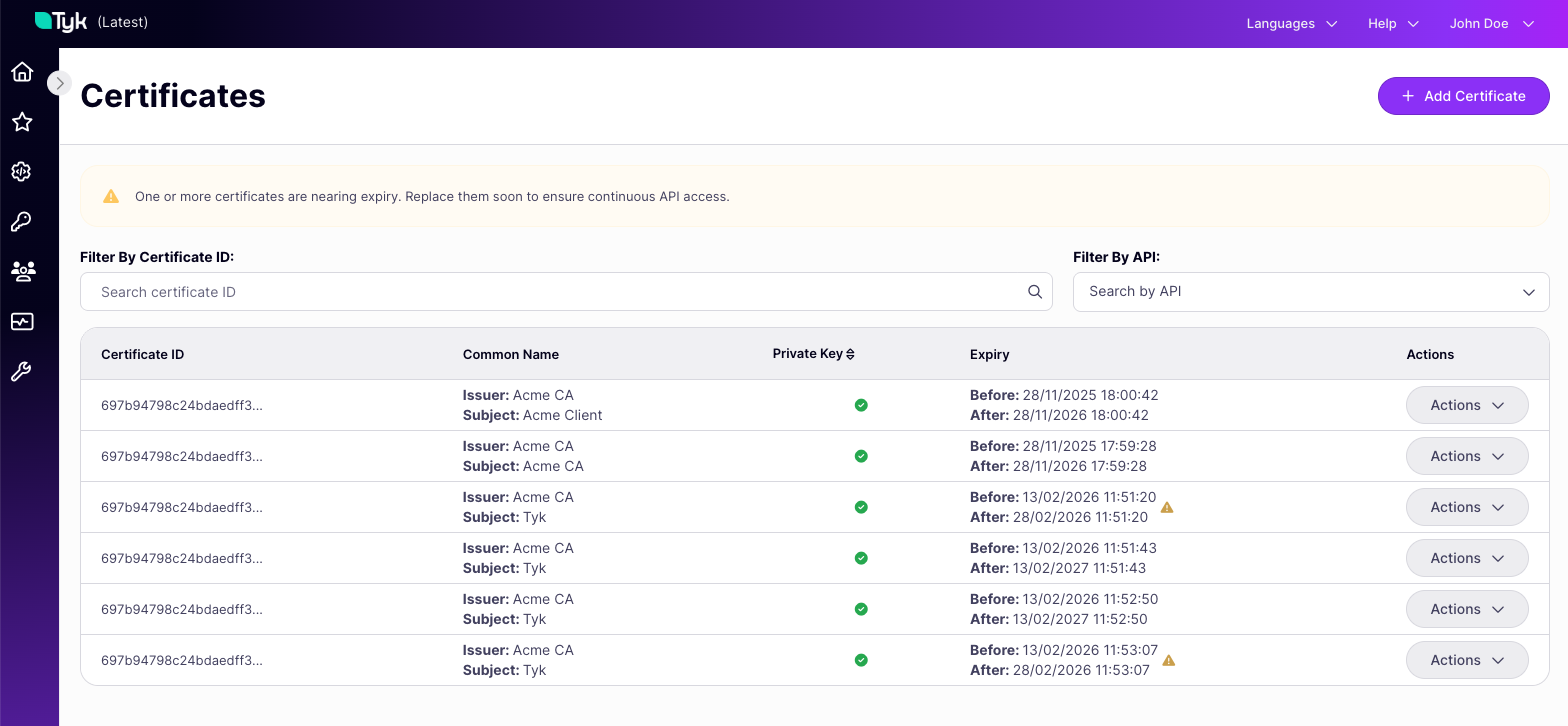
Managing Certificates using the Dashboard UI
The Tyk Dashboard provides a visual interface to the Tyk Certificate Store via the API Security > TLS/SSL Certificates screen.