Step by step guide using Gluu
We are going walk you through a basic integration of Tyk with Gluu using the OpenID Connect Dynamic Client Registration protocol. Our current implementation provides support for the client credentials flow with support for JWT JSON Web Tokens .
The user journey is as follow:
-
A developer signs up and creates a Dynamic Client Registration provider using your Developer Portal.
-
Tyk sends the Dynamic Client Registration call to your IDPIdentity Provider . The IDP replies with the client ID and secret.
-
Using that information, the developer (or the application) triggers a call to the token endpoint of the IDP.
-
Your developer (or the application) then triggers a call to Tyk, using the token that was generated by the IDP. Tyk validates this token using the JWKSJSON Web Key Sets provided by the IDP.
Requirements
- A Gluu installation, more details here.
- A Tyk Self Managed installation (Gateway + Dashboard).
Getting started with Gluu
In order to get started with Dynamic Client Registration you’ll need to get the OpenID Connect registration endpoint. Open your Gluu dashboard and select the “Configuration” section. Select “JSON Configuration” and toggle the “OxAuth Configuration” tab.
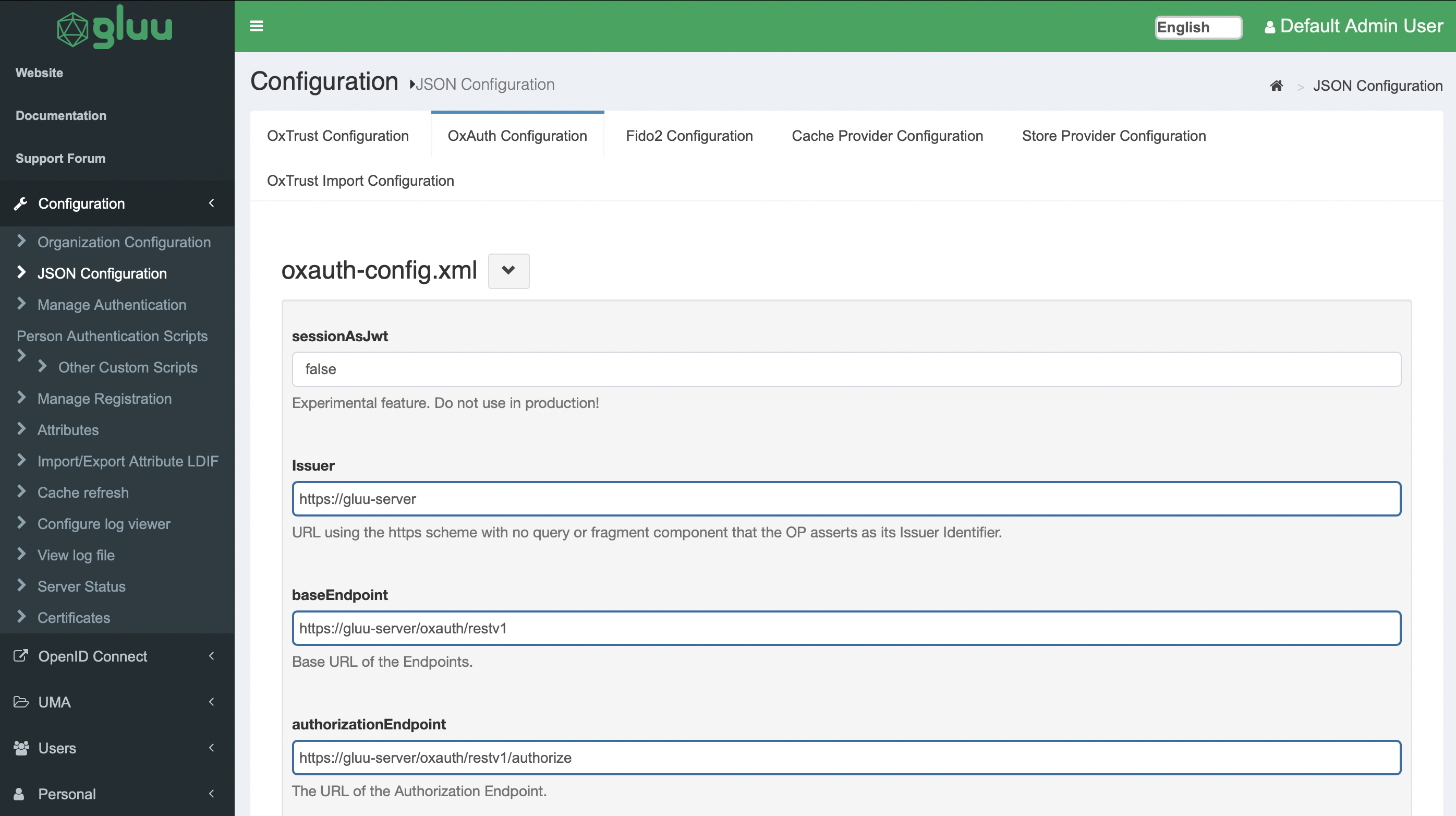
In this view you will find the registration endpoint:
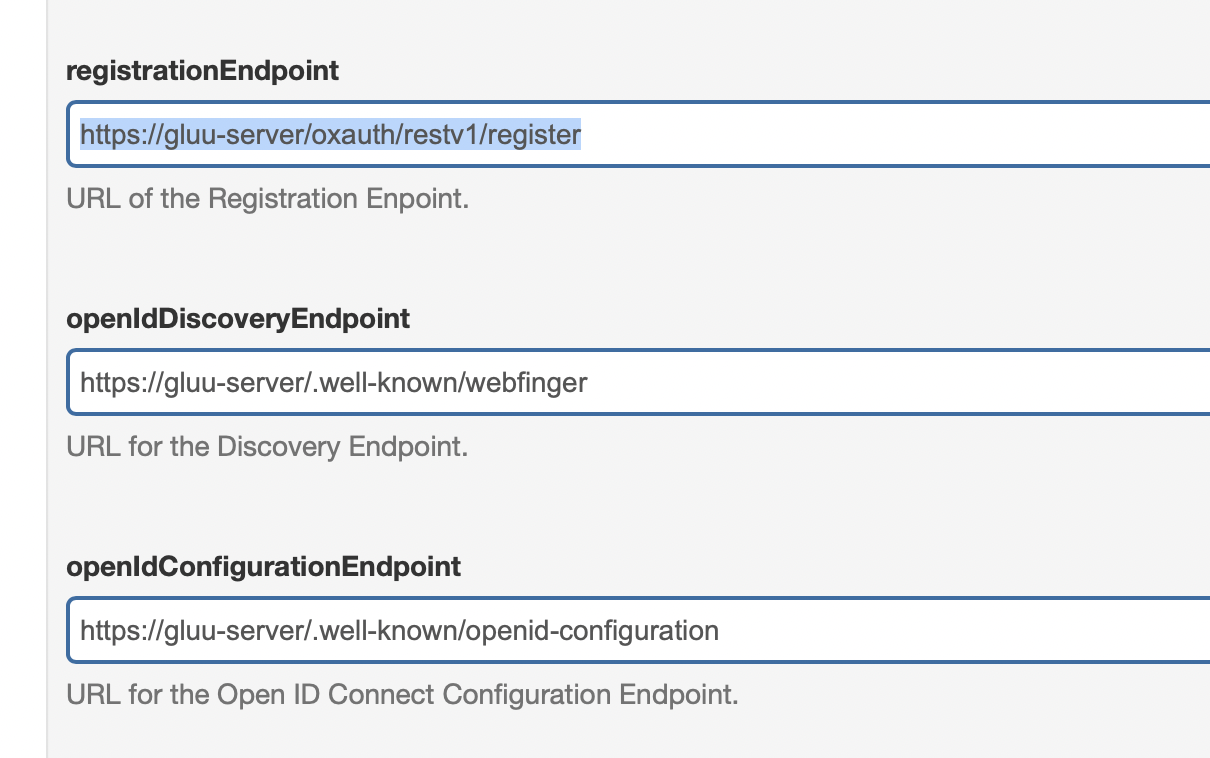
Another endpoint that will be relevant for your setup is the Well-Known configuration endpoint. Keep both URLs handy as you’ll use them for our next steps. This endpoint typically looks as follows: https://gluu-server/.well-known/openid-configuration
Because of known issues with Tyk’s JWT driver, you’ll set specific algorithms for the JWKS endpoint. In the same “OxAuth Configuration” tab, scroll down to “jwksAlgorithmsSupported” and select the following options:
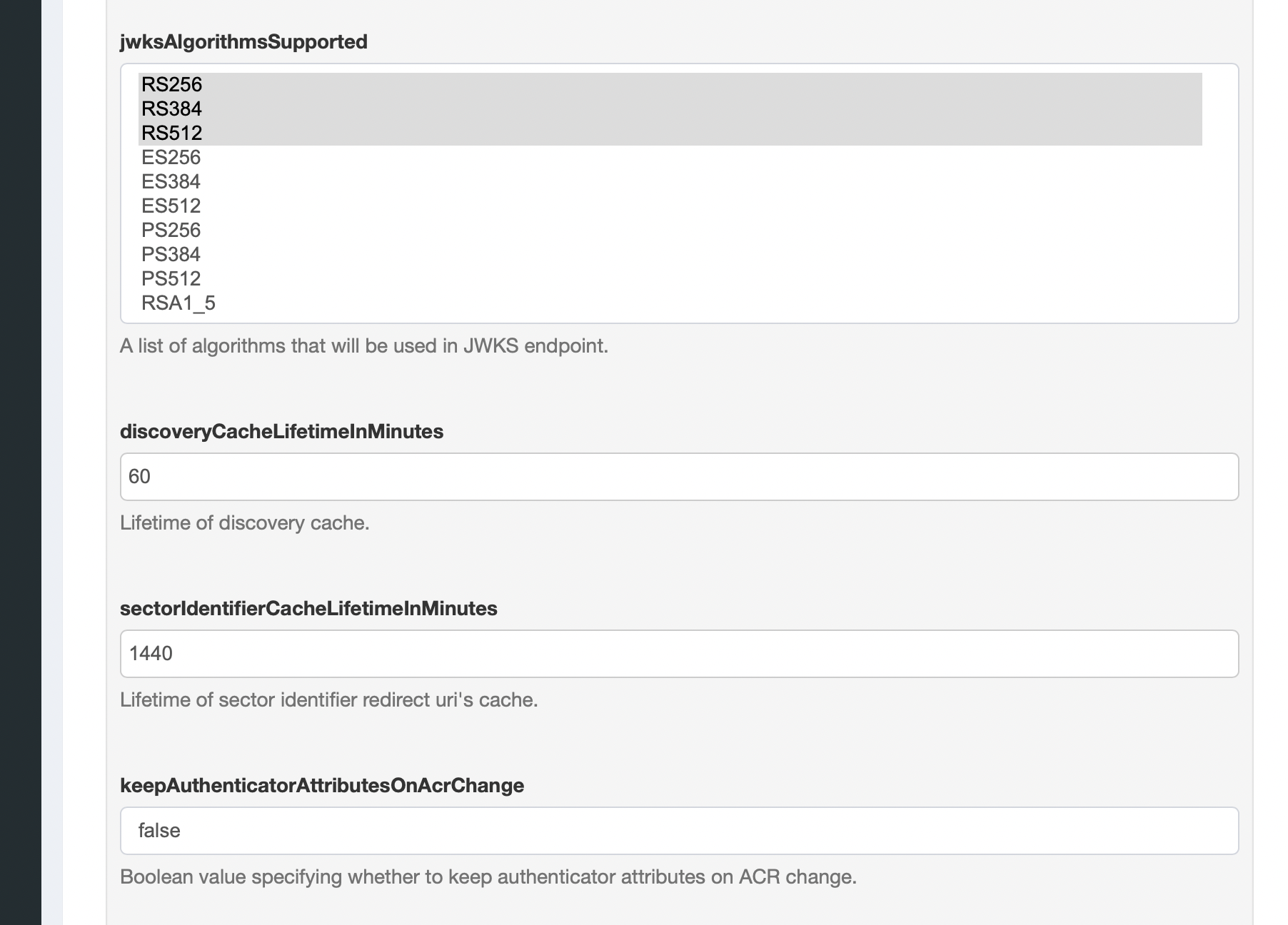
Click “Save OxAuth Configuration” afterwards.
For more information on this particular issue please check this thread in the Gluu forum.
Setting up Tyk
Now you’re ready to set up Tyk. For compatibility reasons, check your tyk_analytics.conf and make sure that a proper oauth_redirect_uri_separator parameter is set. You can use the following value:
"oauth_redirect_uri_separator": ";",
Remember to restart the service after applying the above change.
Now open the Tyk Dashboard and click APIs under System Management. Create a new API called “Gluu API”:
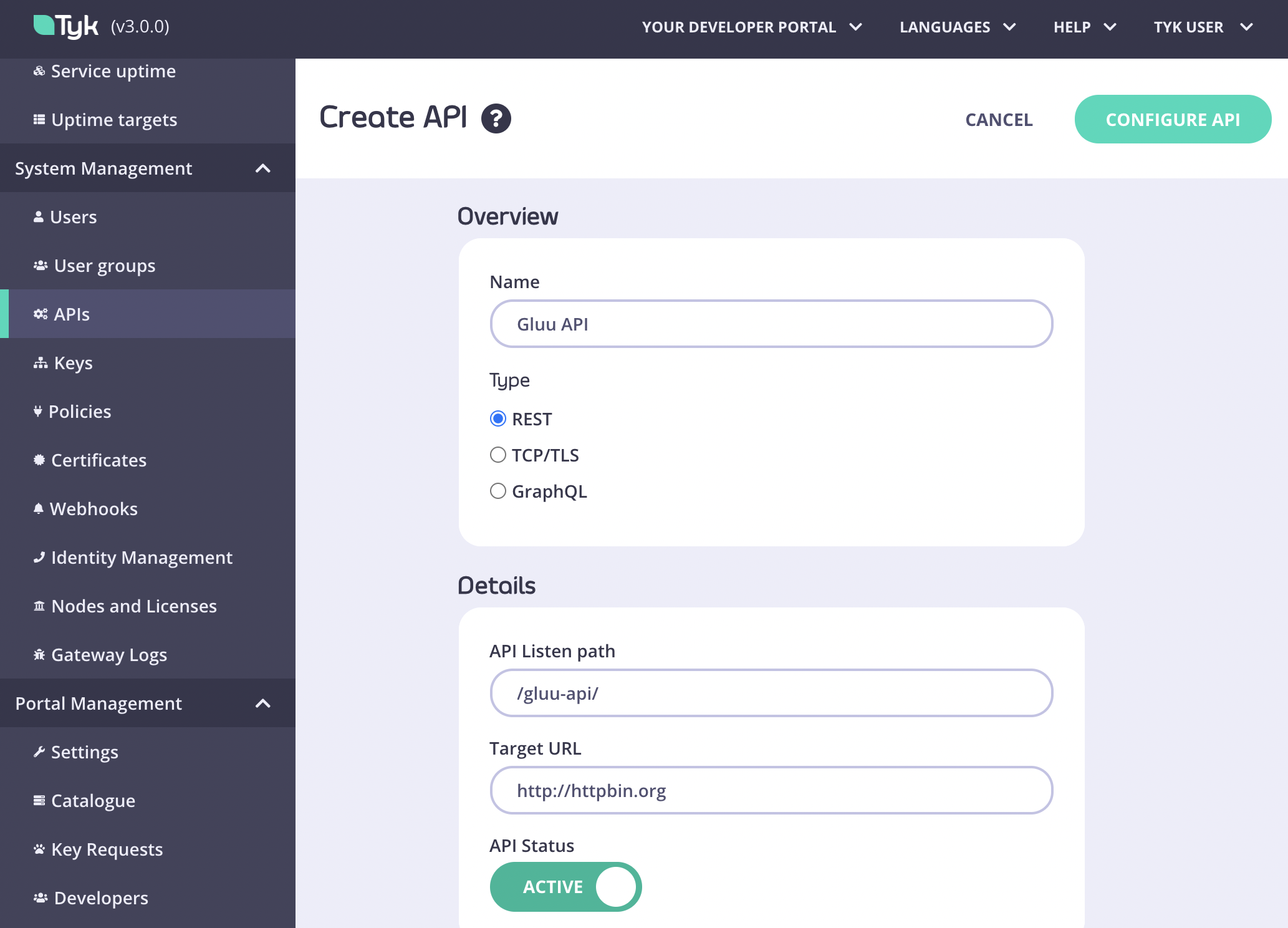
After the first part of the API creation form was filled, click on “Configure API” and set the authentication settings as follows:
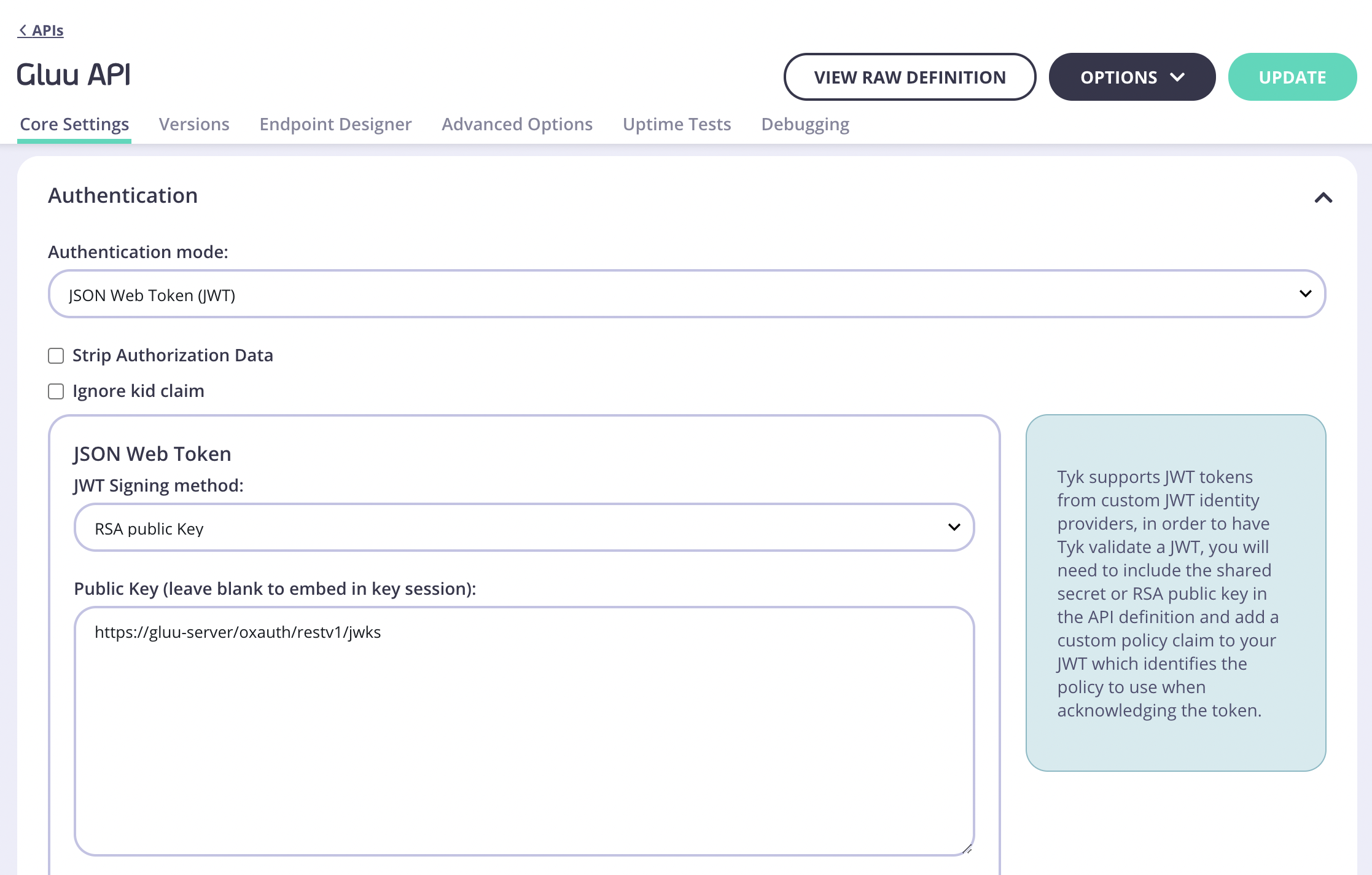
Note
Where do I get the proper JWKS URI for my Gluu environment?
The JWKS URI is a required field in the .well-known/openid-configuration endpoint of your OpenID Connect Provider metadata. Typically found as "jwks_uri". Please see the spec https://openid.net/specs/openid-connect-discovery-1_0.html#ProviderConfigurationResponse for further information.
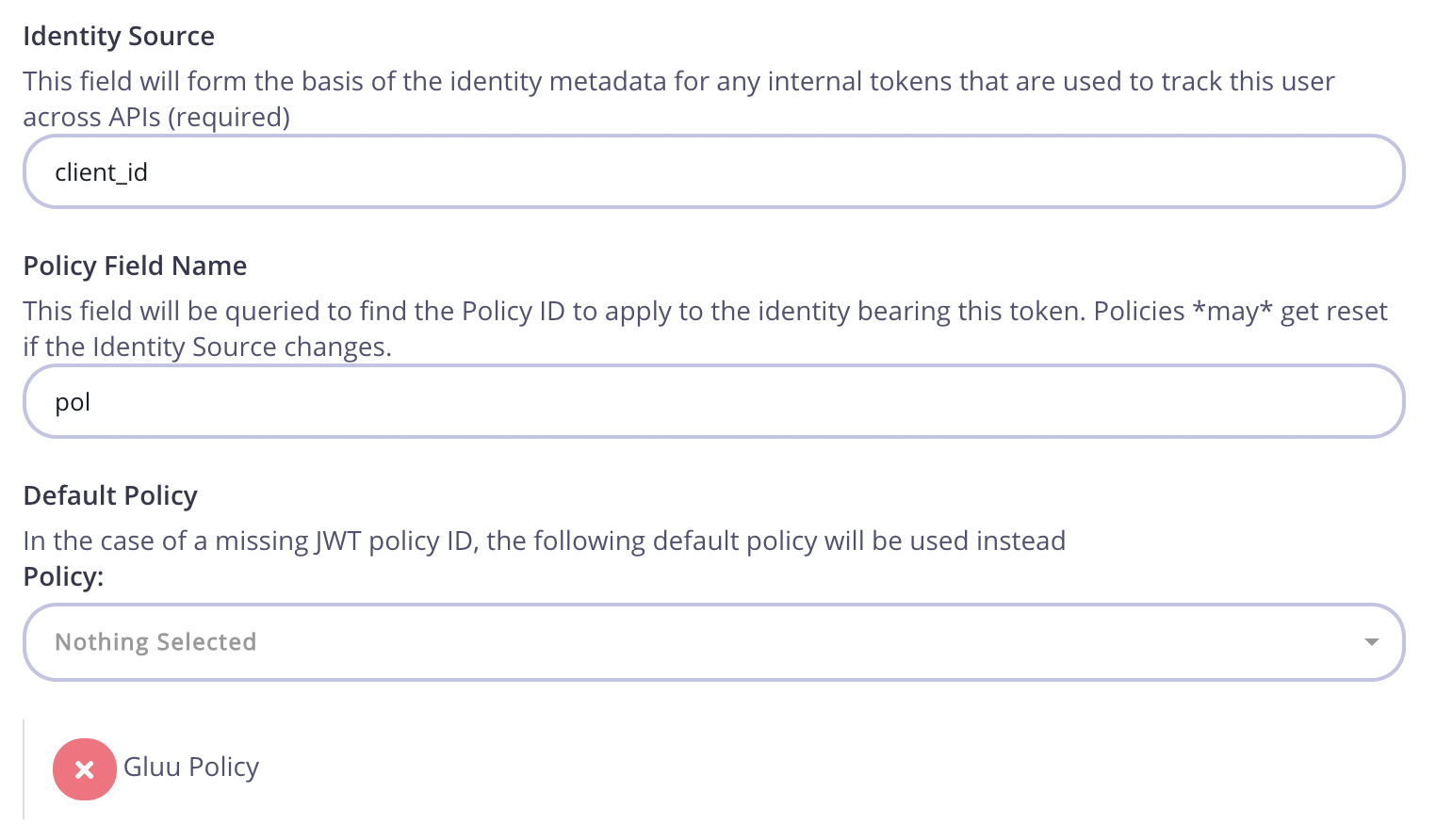
For the Identity Source field use "client_id" and for Policy Field Name use "pol".
Click “Save” and switch to the “Policies” button under “System Management”. Once in this section, click on “Create a Policy” and call it “Gluu Policy”. Use the default values for this one. Remember to select the previously created “Gluu API” in the access rights section. You will also need to set an expiration setting for the keys.
After the policy is ready, switch back to the API settings and make sure that the API is using the appropriate policy:
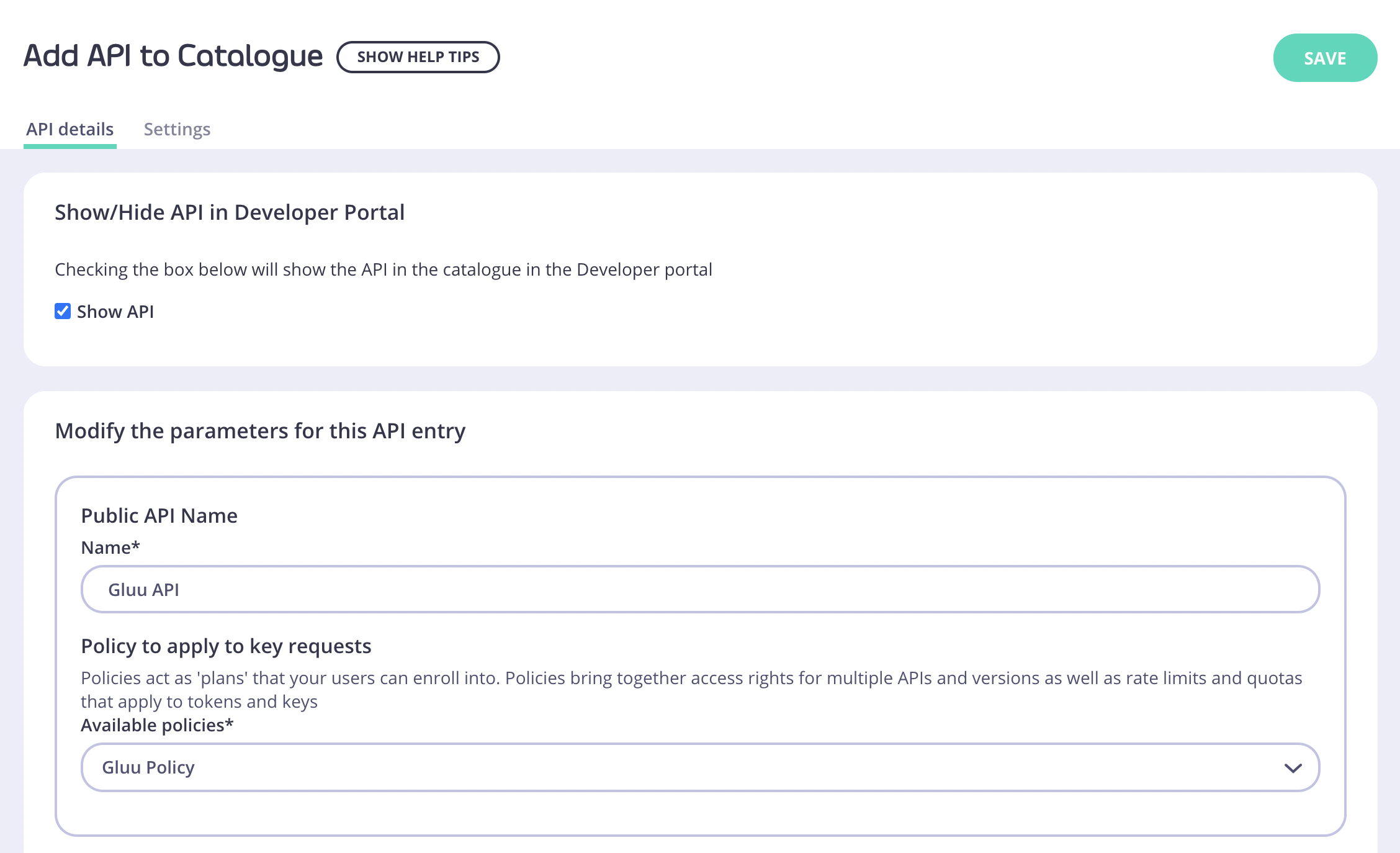
Now you’re ready to add this API to the developer portal. Switch to the “Catalogue” section under “Portal Management” on the navigation menu. Click on “Add New API”, set a name for it and select the newly created policy. For this example use “Gluu Policy”:
Hit “Save” and click on the recently created item again, switch to the “Settings” tab that’s next to “API Details”. In “API Details” toggle the “Override global settings” option.
Note
Tyk lets you set global portal settings that apply to all portal-listed APIs, in this guide we assume you’re enabling and setting up DCR for a single API. In case you want to enable DCR for all the APIs, you should go to the Settings section under Portal Management, and in the API Access tab you can enter your DCR settings there.
Once the “Override global settings” option is toggled, scroll down to the DCR section in the bottom and enter the following settings:
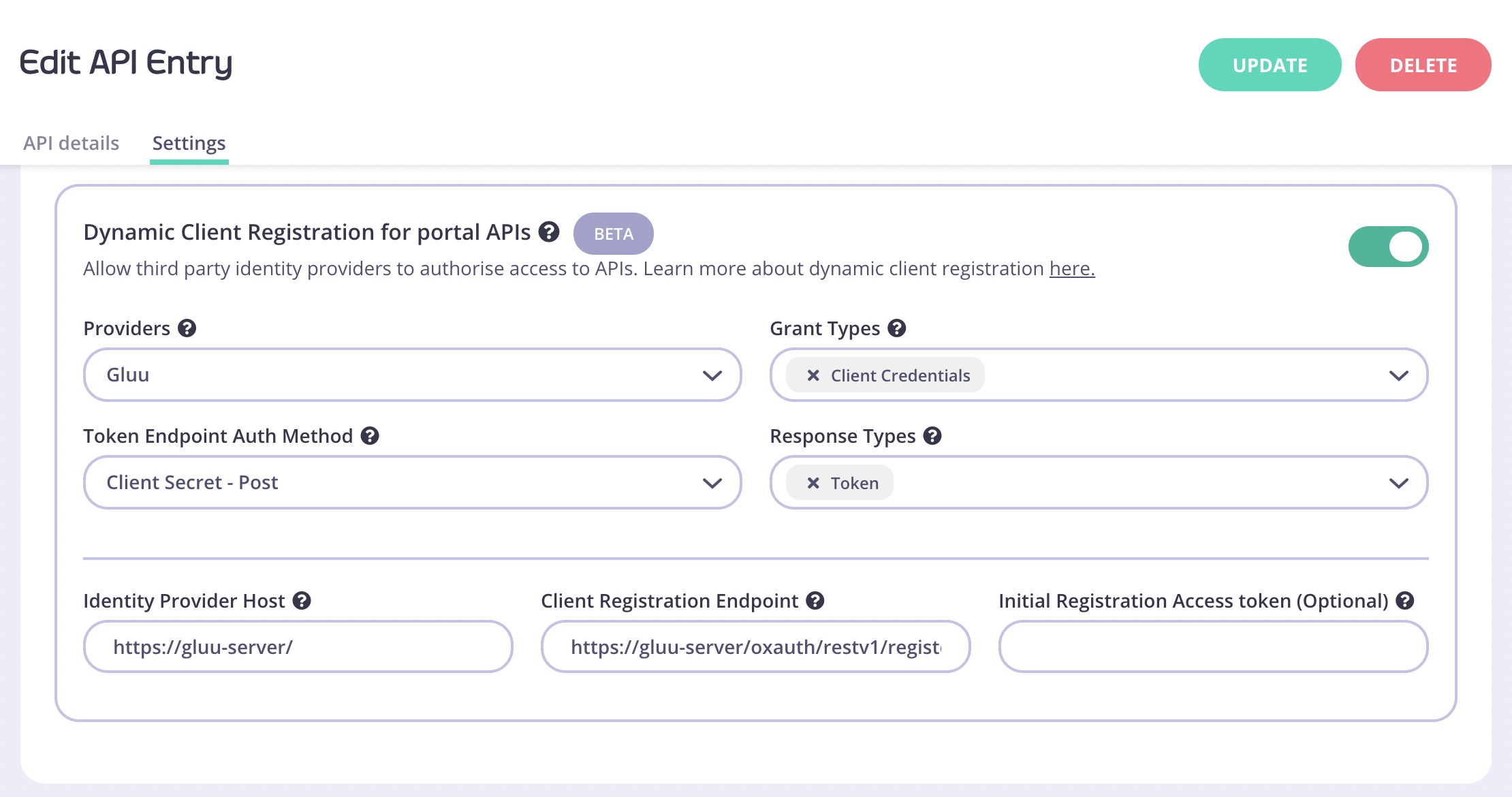
Providers: Different providers might implement the standard in slightly different ways. Tyk provides a specific driver for each one. For IDPs that aren’t on the list use the “Other” option. For this guide, pick “Gluu”.
Grant Types: The OAuth 2.0 grant types types that will be used by the client, see the specification for more details. Set “Client Credentials”.
Token Endpoint Auth Method: defines the way the client will authenticate against the token endpoint. Use “Client Secret - Post”.
Response Types: OAuth 2.0 response types that will be used by the client. Set Token.
Identity Provider Host: Base IDP URL, e.g. https://gluu-server/
Client Registration Endpoint: OpenID Connect client registration endpoint. The value we use is https://gluu-server/oxauth/restv1/register
This value is found in your well-known discovery document as registration_endpoint. The well-known location URL is typically https://gluu-server/.well-known/openid-configuration (replace “gluu-server” with your hostname).
Initial Registration Access Token: the token that’s used to register new clients, this was generated in the early steps of the guide.
Testing the flow
Now that both Tyk and Gluu are ready you can try the complete flow. Click “Developers” under “Portal Management”, then click “Add developer” and enter some basic information here to create a developer user.
After the developer is created, open the portal, click on the “OAuth Clients” navigation bar button and follow the wizard:
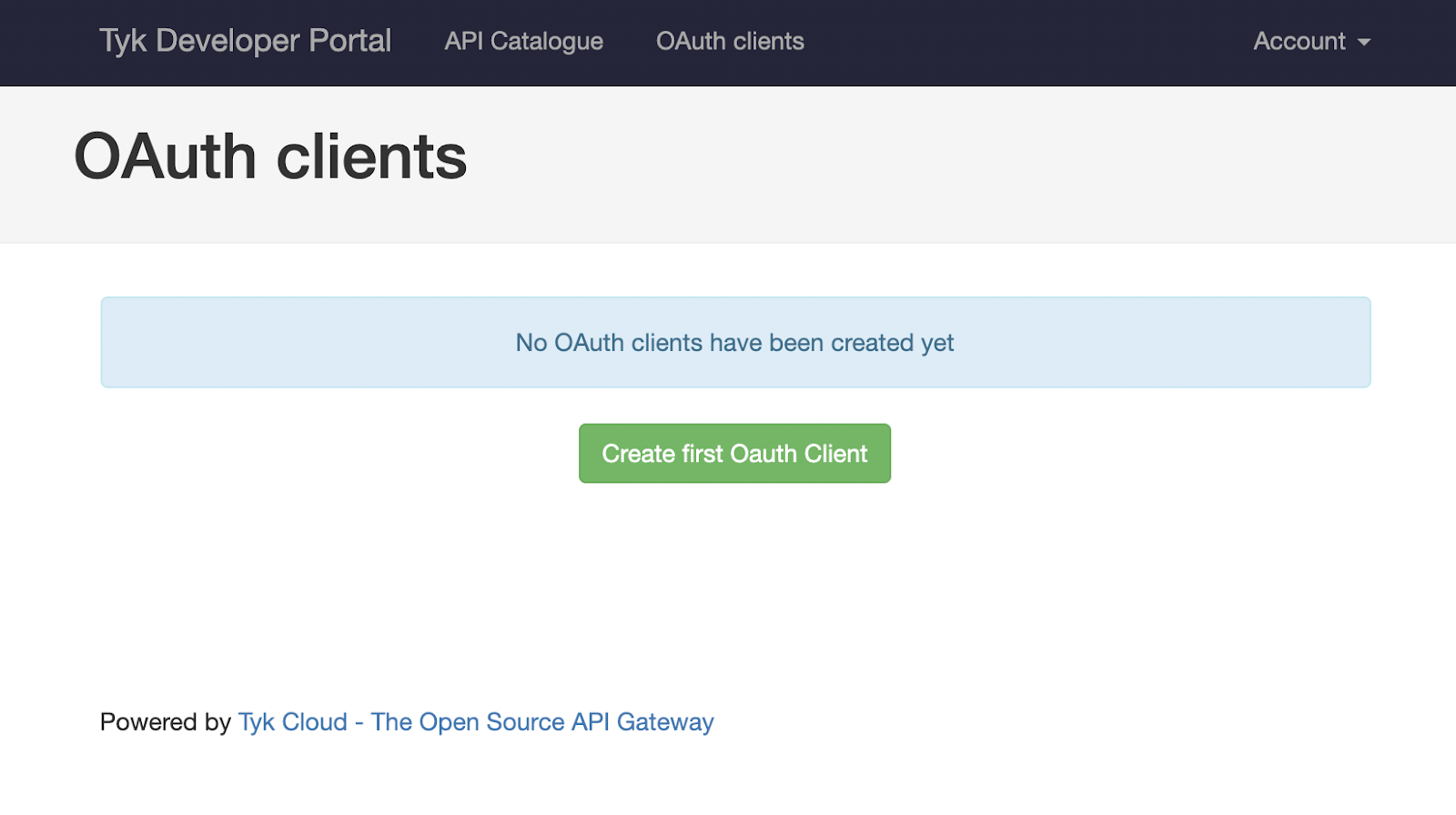
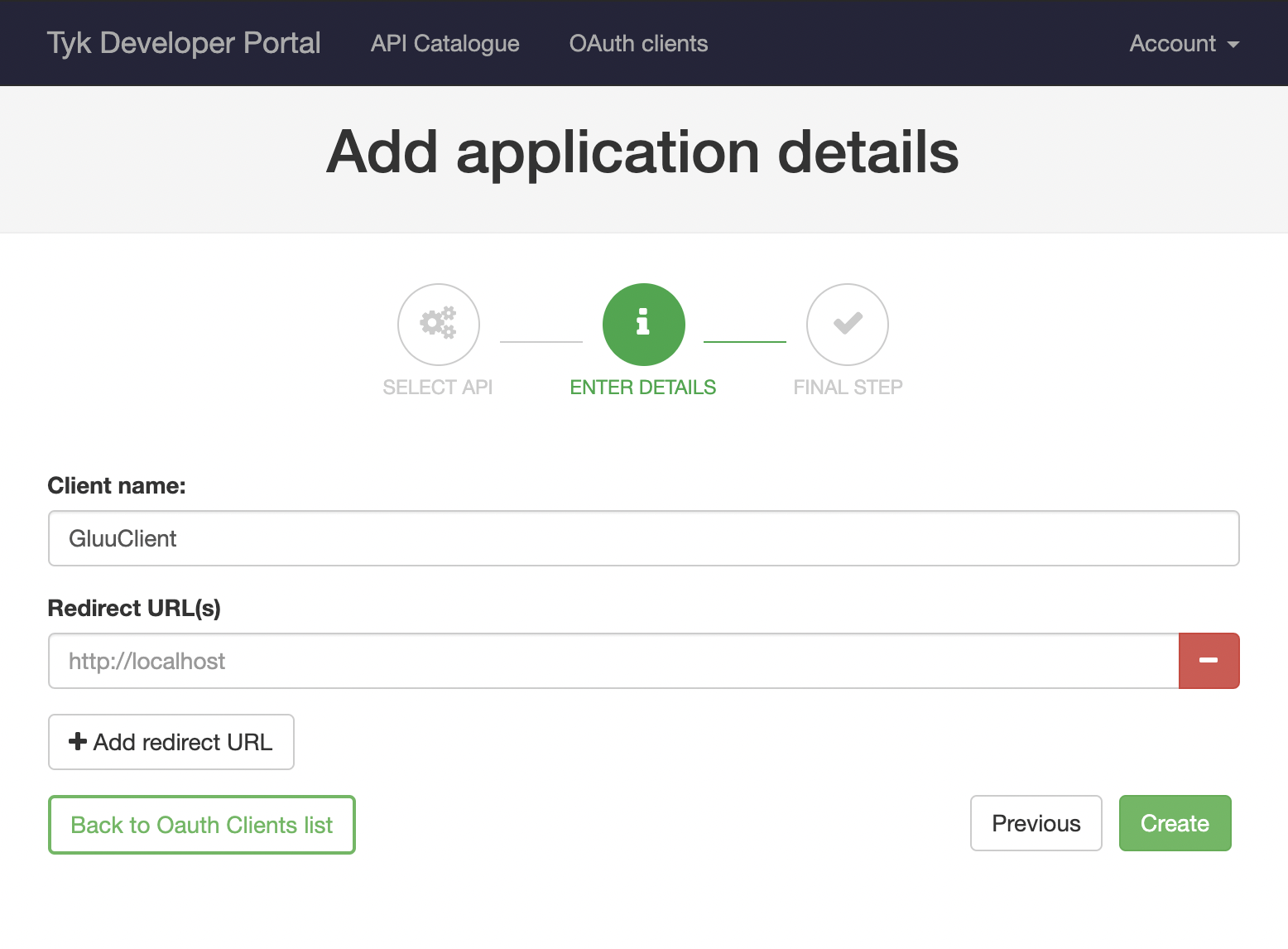
After clicking “Create first OAuth Client” you’ll see your previously created “Gluu API”. Select it and click “Save and continue”. The following screen will require you to enter a client name. It’s possible to set redirect URLs if you also plan to use this client for other flow types. This setting can be left blank for the purposes of this example.
Once you click “Create”, Tyk will trigger a registration on your IDP and the details of your client will show up:
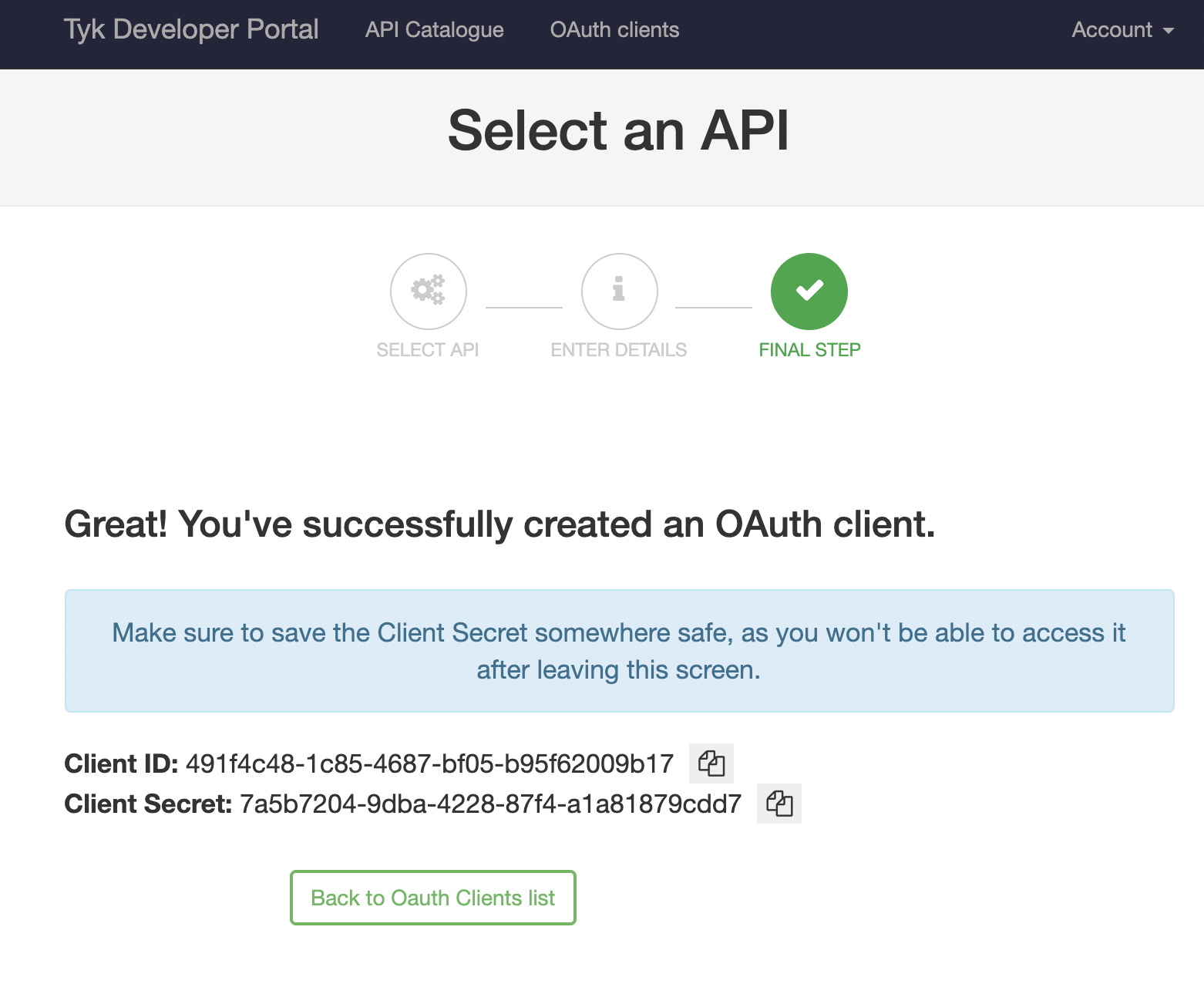
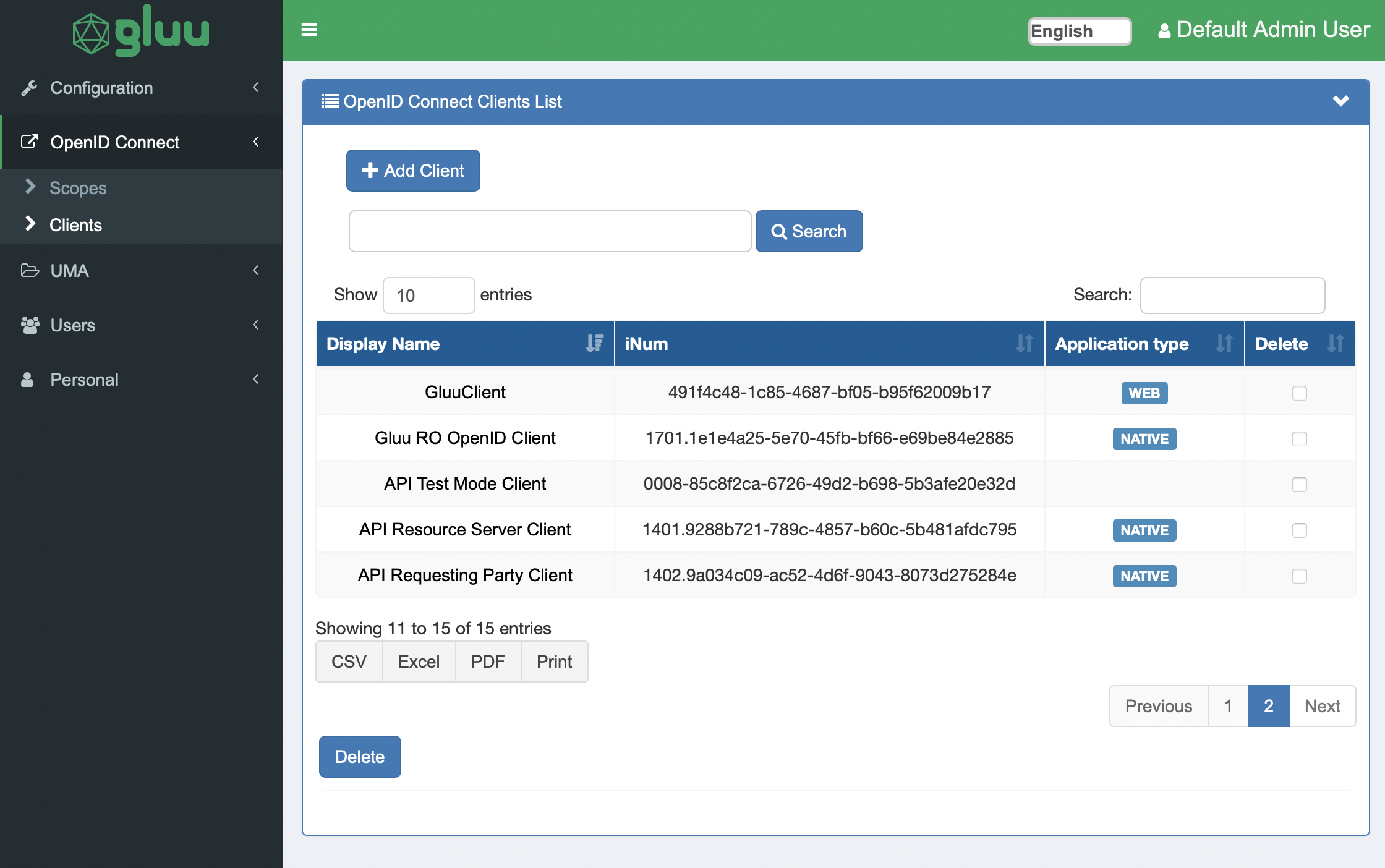
If you check the Gluu dashboard you will see new client (named “GluuClient”):
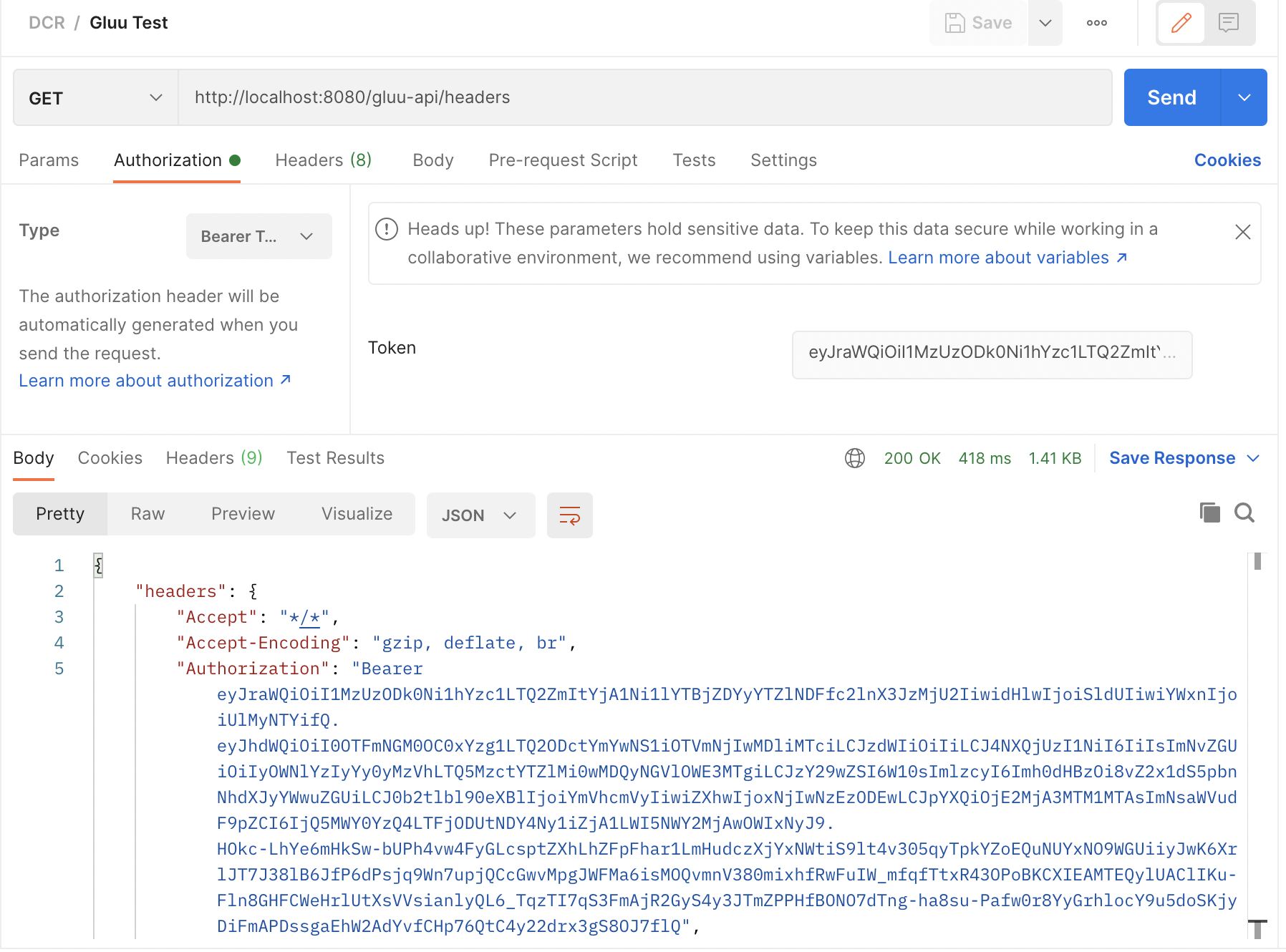
The next step is to generate a token and use it for accessing your “Gluu API”. you can use Postman for this. You will need the token URL which it’s also present in the Well-Known URI of your organization. The field is named "token_endpoint".
For this example use the following: https://gluu-server/oxauth/restv1/token
Your Postman request should contain the following body, where "client_id" and "client_secret" are the values you got from the developer portal:
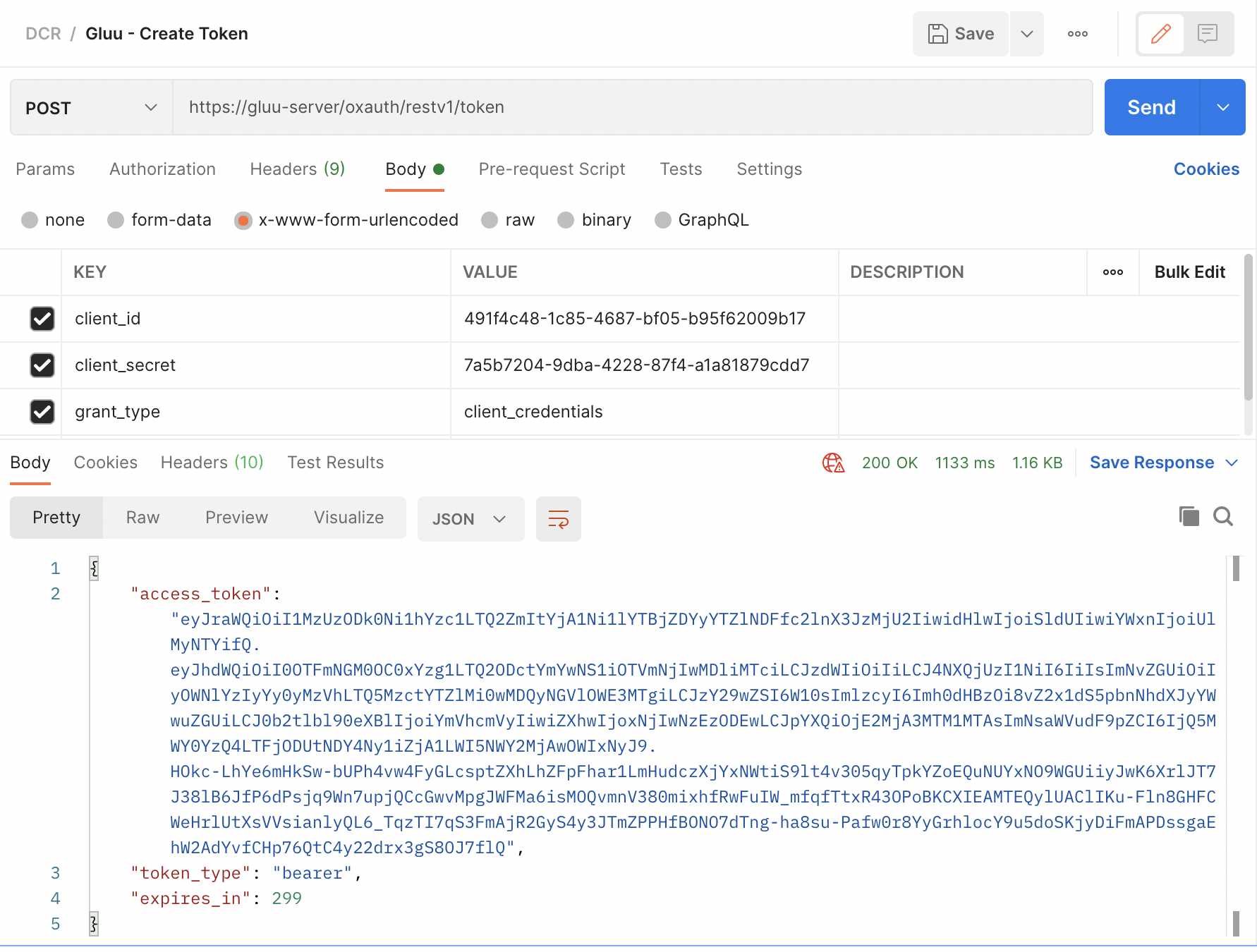
Note that you aren’t using any additional headers for this request, the client credentials are enough.
Once you get a response from the IDP, you can copy the "access_token" and use it to access your “Gluu API”, this request will be proxied by Tyk: