Purpose
The User Management & RBAC system provides administrators with the tools to:- Manage the lifecycle of user accounts.
- Define how users authenticate (UI sessions, API keys).
- Organize users into logical teams.
- Grant fine-grained access to Tyk AI Studio resources (LLMs, Tools, Data Sources, Chat Experiences) based on team membership.
- Assign platform-level permissions using roles.
Core Concepts
- User: Represents an individual interacting with Tyk AI Studio. Users are typically identified by an email address or username and can be created manually by administrators, via invitation, self-registration (if enabled), or provisioned through SSO Integration.
- Authentication: The process of verifying a user’s identity.
- Session-based: For users logging into the Tyk AI Studio UI (using username/password or SSO).
- API Key: For applications or scripts interacting with Tyk AI Studio APIs (like the Proxy).
- API Key: A unique, long-lived token generated by a user. Applications use this key (typically in an
Authorization: Bearer <key>header) to authenticate requests on behalf of the user who generated it. - Team: A collection of users. Teams are the primary mechanism for assigning access rights to resources. A user can belong to multiple teams.
- Resource: Any entity within Tyk AI Studio whose access needs to be controlled. This includes:
- LLM Configurations
- Tool Catalogues (collections of Tools)
- Data Source Catalogues (collections of Data Sources)
- Chat Experiences (configurations for the Chat Interface)
- Role: Defines a set of broad, platform-level permissions. Common roles include:
- Admin: Full access to configure and manage the Tyk AI Studio platform.
- Standard User: Access to use assigned resources (e.g., chat, query LLMs) but limited or no administrative capabilities.
- RBAC (Role-Based Access Control): Tyk AI Studio’s access control model. Access is granted primarily by assigning resource access to Teams, and then adding Users to those Teams. Roles provide overarching platform permissions.
- User Entitlements: The complete set of permissions a specific user has at any given time. This is calculated based on their assigned Role and the combined permissions granted through all the Teams they belong to. Systems like the Proxy check these entitlements before allowing an action.
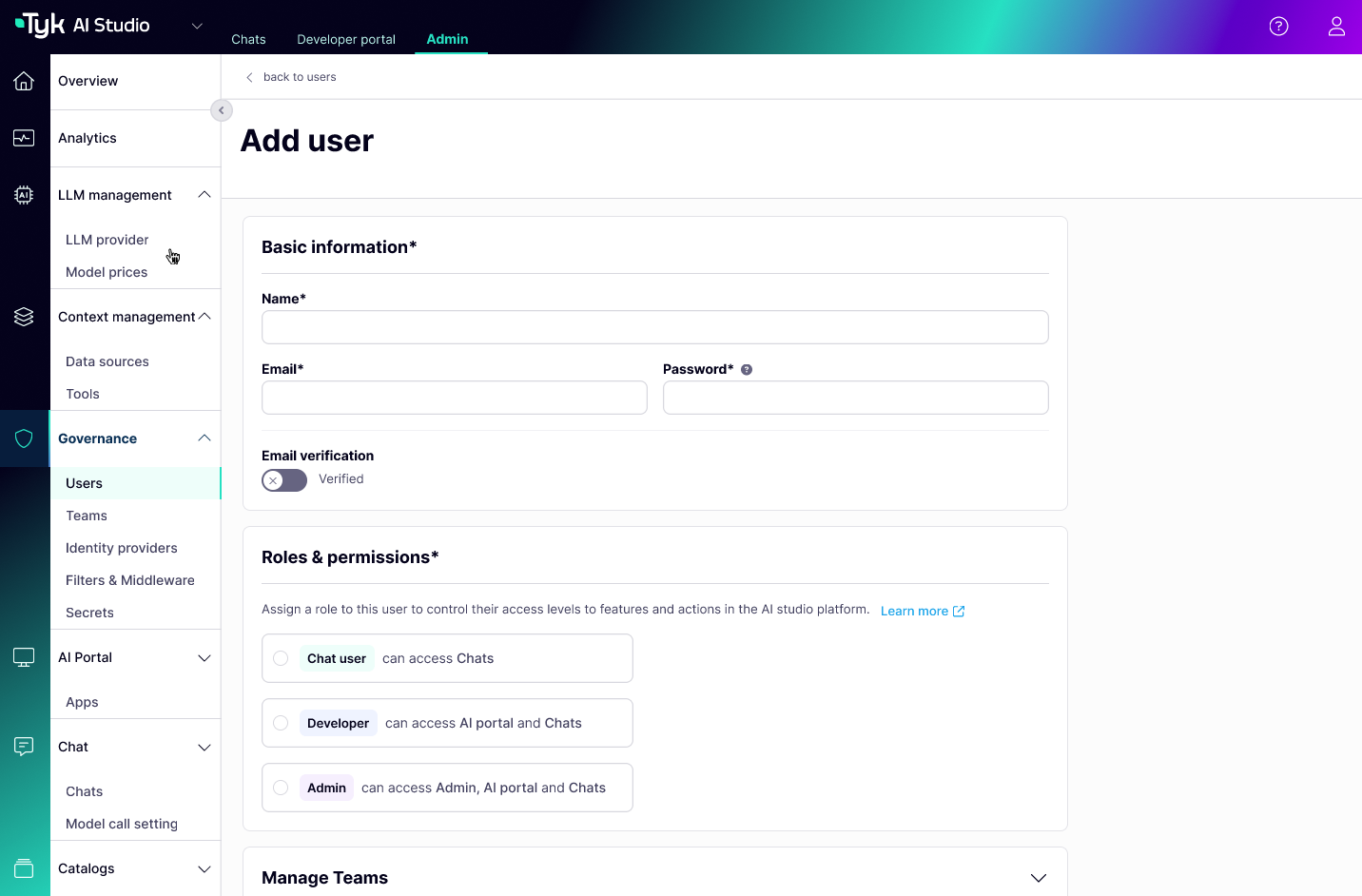
User Lifecycle Management (Admin)
Administrators manage users via the UI or API:- Creation: Create user accounts manually, send invitations, or manage users provisioned via SSO.
- Team Assignment: Add or remove users from various Teams.
- Role Assignment: Assign a primary Role (e.g., Admin, Standard) to each user.
- Status Management: Activate or deactivate user accounts.
-
API Key Management: Admins may have visibility into user API keys (though users typically generate their own).
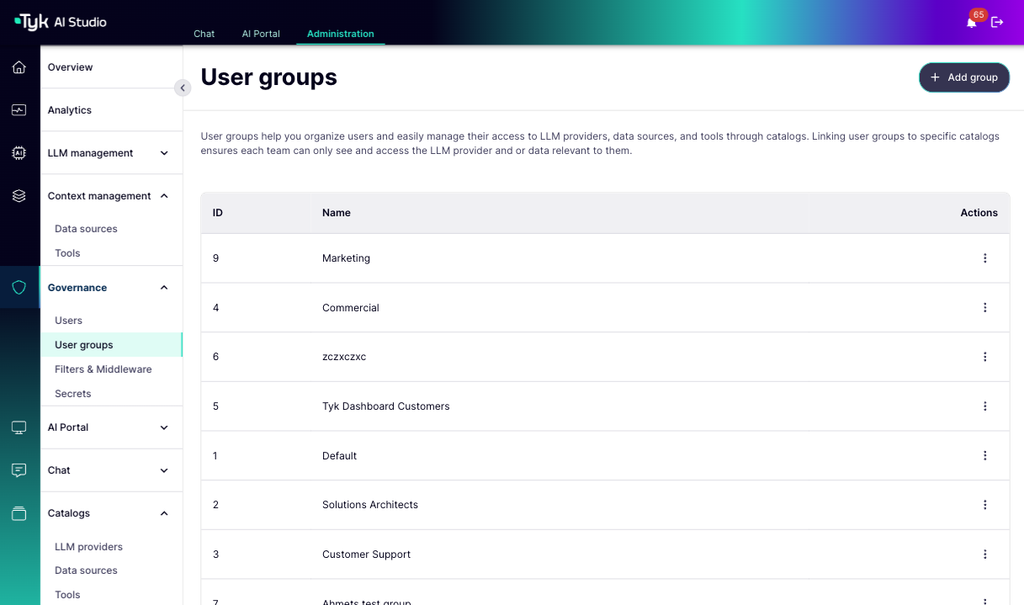
Team Management (Admin)
Teams are central to managing permissions:- Creation/Deletion: Create and manage teams (e.g., “Developers”, “Sales Team”, “Product Docs Users”).
- User Assignment: Add/remove users from teams.
-
Resource Assignment: Grant access to specific LLM Configurations, Tool Catalogues, or Data Source Catalogues to the team. Any user in that team inherits this access.
Authentication Methods
- UI Login: Users access the web interface by logging in with their credentials (username/password) or via a configured SSO Provider. This establishes a browser session.
- API Key Authentication:
- A user generates an API Key via their profile settings in the UI.
- The user securely provides this key to their application or script.
- The application includes the key in the
Authorizationheader for requests to Tyk AI Studio APIs: - Tyk AI Studio validates the key and associates the request with the user who generated it.
Access Control Flow Example (API Request)
When an application makes a request to the Proxy using an API Key:- Key Validation: Tyk AI Studio validates the API Key.
- User Identification: The system identifies the User associated with the key.
- Team Membership: The system determines all Teams the User belongs to.
- Resource Check: The request targets a specific resource (e.g., an LLM Configuration via its
routeId). - Permission Verification: Tyk AI Studio checks if any of the user’s Teams have been granted access to the requested resource.
- Entitlement Check: Additional checks based on the user’s Role and specific entitlements might occur (e.g., budget checks, model restrictions).
- Access Granted/Denied: If all checks pass, the request proceeds; otherwise, it’s denied (e.g., 401 Unauthorized or 403 Forbidden).